
Control Center
Administrator Guide
© 2024, Avigilon Corporation. All rights reserved. AVIGILON, the AVIGILON logos, and AVIGILON ALTA are
trademarks or registered trademarks of Avigilon Corporation. Allegion, ENGAGE technology and Schlage are
trademarks of Allegion plc, its subsidiaries and/or affiliates in the United States and other countries. Cisco and
Meraki are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. Mac
and App Store are trademarks of Apple Inc., registered in the U.S. and other countries and regions. Safari is a
trademark of Apple Inc., registered in the U.S. and other countries and regions. WORKDAY and the Workday Logo are
trademarks of Workday, Inc., some registered in the United States and elsewhere. XProtect is a registered trademark
of Milestone Systems A/S. ZAPIER is a trademark of Zapier, Inc. All other trademarks are the property of their
respective owners.
This document has been compiled and published using product descriptions and specifications available at the time
of publication. The contents of this document and the specifications of the products discussed herein are subject to
change without notice. Avigilon Corporation reserves the right to make any such changes without notice. Neither
Avigilon Corporation nor any of its affiliated companies: (1) guarantees the completeness or accuracy the
information contained in this document; or (2) is responsible for your use of, or reliance on, the information. Avigilon
Corporation shall not be responsible for any losses or damages (including consequential damages) caused by
reliance on the information presented herein.
Avigilon Corporation
avigilon.com
20240522-en
2

Revisions
Guide Description
Rev. 4.15 Alta Aware alarm management: Alarm Management workflow on page15, Event triggers and
advanced filtering on page132 (Aware rule), Schedules on page134
Common Alerting Protocol (CAP) integration with mass emergency notification and response
systems: Add rules and triggers on page126 (CAP message, Alert code), Action triggers and alarm
notifications on page134; Rave Alert notification system integration: Rave Alert app on page123
Avigilon Alta Open app (formerly, Openpath Mobile Access app), Avigilon Alta Access app (formerly,
Open Admin app) rebrand: User management on page37
Tip in Set up a maintenance window for all device updates on page97
Reset table option throughout Control Center: Show, hide, or reset information on page99
Rev.4.14 Occupancy report:Assign permissions to roles on page48, Reports on page98, Schedule report
generation and forwarding (Premium and Enterprise plans) on page100; Occupancy limit (previously,
Occupancy) widget: Create custom dashboards on page31
SAML Single Sign-on app: Sign in on page11, Identity management on page102, note in Manually
sync accounts on page103, SAML Single Sign-on app on page116, Device (Read-Only) role in Role
management on page46
Rev. 4.13 Device updates: Device update management on page96, Set up a maintenance window for all device
updates on page97
Avigilon Alta Open app help setup: Add help contact for mobile credential users on page142
Front Desk Connect and Visual Voicemail fields: Configure call routing to users, units, or front desk on
page91
Revisions 3

Contents
Revisions 3
Get started 11
Sign in 11
Notifications 12
Set your preferred language 12
Set language at sign-in 13
Set language in your profile 13
Set language in organization-wide emails 13
Set language in site-wide emails 13
Terms 13
For more information 14
Technical support 14
Product documentation 14
Workflows 15
Alarm Management workflow 15
Muster Reports workflow 16
Alta Aware, Alta DMP, and Control Center workflow 17
User and role management 18
Video playback and access events 18
Aware, DMP, and Control Center app navigation 19
Triggering lockdown plans 20
Use Control Center menu bar 20
Use Lockdown widget on custom dashboard 21
Use Lockdown event triggers 21
User profile 22
Update your account information 22
Change password 22
Add MFA devices 22
Enable intercom notifications 23
Play or mute alarm notification sounds 23
Revisions 4

Enable Dark mode, Light mode, or Match system theme 23
Dashboards 25
Activity dashboard 25
Filter by site 25
View camera snapshots 26
Alarms dashboard 26
Filter by alarm severity or status 26
Acknowledge, clear, or reactivate active alarms 26
Export alarm history 27
Entry dashboard 28
View usage statistics of an organization 28
Unlock entries 28
View entries on maps in AwareVMS 28
Device dashboard 29
Controller and reader status 29
Refresh controller data 29
Restart controller services 30
Verify the physical reader is connected to Alta Control Center 30
Restart the reader 30
Mute the controller or reader 30
Custom dashboards (Premium and Enterprise plans) 31
Create custom dashboards 31
Edit custom dashboards 32
Cameras 34
View live video feeds 34
Initiate calls to intercom on Video Intercom Reader Pro 35
Play and download video 35
Users 36
User data model 36
User management 37
Add users 37
Upload photo 38
Issue keycard, fob, mobile, PIN, wiegand, or cloud-based credentials 39
Revisions 5

Edit user access 41
View MFA credentials 43
Delete users 43
Import users by CSV file 43
Issue batch actions to users 44
Access groups management 45
Add access groups 45
Role management 46
Export information to CSV 47
Show, hide, or reset information 47
Add roles 47
Assign permissions to roles 48
Delete roles 49
User schedules 50
Multiple schedules 50
Add user schedules 50
Custom fields 52
Create custom fields 53
Sites 55
Site management 55
Add sites 55
Add zones 55
Building management 55
Add buildings 56
Add floors to buildings 56
Add units to floors and assign access 56
Zone management 56
Export information to CSV 57
Show, hide, or reset information 57
Zone sharing between customers 57
Add zones 57
Anti-passback and occupancy management 58
Entry management 60
Revisions 6

Export information to CSV 60
Show, hide, or reset information 61
Add entries 61
Edit entries 61
Entry states 65
View trigger methods in entry states 65
Add entry states 66
Entry schedules 67
Add entry schedules 67
Add holiday schedules 68
Lockdown plans (Premium and Enterprise plans) 69
Add lockdown plans 70
Assign users and group permissions for lockdown plans 71
Devices 72
ACU management 72
Export information to CSV 72
Show, hide, or reset information 72
Add ACUs or SDCs 73
Add expansion boards 75
Edit ACU ports 75
Reader management 77
Export information to CSV 77
Show, hide, or reset information 77
Add reader 77
Wireless lock management 78
Update lock firmware 78
Edit locks 78
Wireless lock gateway management 81
Sync gateways with Alta Control Center 81
Update gateway firmware 81
Video reader management 82
Export information to CSV 82
Show, hide, or reset information 82
Revisions 7

Add video reader 82
View activated video reader 83
Configure recording, detection, and ONVIF settings 84
Change cloud video storage plan 86
Video intercom reader management 87
Export information to CSV 87
Show, hide, or reset information 87
Add video intercom reader 87
View activated video intercom reader 88
Configure recording, detection, and ONVIF settings 88
Change cloud video storage plan 90
Configure two-way audio 90
Configure call routing to users, units, or front desk 91
Use QR codes to look up directories on phones (optional) 92
View live video feed 95
Answer calls from intercom 95
Device update management 96
Show or hide device updates 96
Apply device updates on demand 97
Set up a maintenance window for all device updates 97
Reports 98
Show, hide, or reset information 99
Export report to CSV 99
Configure reports (Activity logs, Alarms, and Portal audit report) 100
View and mark users as safe in the Muster report (Premium and Enterprise plans) 100
Schedule report generation and forwarding (Premium and Enterprise plans) 100
View scheduled reports (Premium and Enterprise plans) 101
App marketplace 102
Identity management 102
Manually sync accounts 103
Google Workspace 104
Microsoft Azure AD 106
Okta 110
Revisions 8

OneLogin 114
SAML Single Sign-on app 116
Workday reports 118
Video management 121
Alta Aware app 121
Camio 122
Cisco Meraki 123
Milestone 123
Rhombus 123
Emergency notification and response 123
Rave Alert app 123
Visitor management 124
Envoy 124
Workplace communication 124
Slack 124
Wireless lock integration 124
Schlage Wireless Locks 124
Middleware integration 124
Zapier 124
Troubleshooting 125
Event descriptions 125
Configurations 126
Rules 126
Add rules and triggers 126
Create custom rules 129
Alerts by email or SMS 129
Alarms (Premium and Enterprise plans) 131
Enable, disable, or silence alarms 131
Configure alarms 131
Mobile app 137
Enable badge view 137
Customize badge design 138
Badge templates 139
Revisions 9

Add badge template 139
Print badge 141
Printing tips 141
Administration 142
Account 142
Accept terms and conditions 142
Add help contact for mobile credential users 142
Edit organization information 142
Edit security settings 143
Quick start for sites, ACUs, and readers 143
Licenses 143
Glossary 145
Appendix A: Configure mobile gateway with legacy access control systems 146
System overview 146
Configure Wiegand device settings 147
Revisions 10
Get started
The Avigilon Alta Control Center is an online portal where Administrators can configure the Avigilon Alta access
control system through an internet browser. This guide covers how to get started in the Alta Control Center, manage
users and hardware, and provide access to your entries.
Note: Some features in the Alta Control Center are only available in certain software packages and as add-on
features. Also, depending on your role, not all of these features may be visible to you.
Sign in
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
Note: The Alta Control Center is shown automatically in French, Spanish, Italian, German, or English
based on the language and locale set in your browser.
2. Sign in using one of these options.
Note: If your Alta Aware and Control Center systems have been unified, the Alta Control Center
password must be used to sign in. The Alta Aware password is no longer used in both systems. Normal
browsing mode must also be used. The button and app switcher links do not work in Chrome™
Incognito mode or private mode.
Get started 11
l
If you have not configured Multi-Factor Authentication (MFA) for your account, you are prompted to
set it up. For more information, see User profile on page22.
l
If you received admin credentials through Avigilon Alta Control Center, enter your email and password,
click Enter two-factor authentication code to enter the code generated by your app. Click Sign in.
l
To use the Single sign-on (SSO) method, your organization must have enabled authentication with an
identity provider and sign-in using an identity credential, such as your Okta on page110 account. If
enabled, enter your email and click Continue. Enter the two-factor authentication (2FA) code and click
Sign in.
Note: If an error message asks for your namespace, it means your organization has enabled
SSO for two or more identity providers. Ask the admin who set up the identity provider
integrations for the correct namespace to use. See also User data model on page36.
l
If you are using the SAML Single Sign-on app method for the first time, enter your email and click Use
Avigilon Alta Id. Enter the ID provided by your administrator and click Continue.
Notifications
Notifications (also referred to as popup or toast notifications) are system messages that need your attention, such
as alarm events, intercom events, and more.
ll
A visual indicator (blue dot) in the browser tab indicates new notifications.
Tip: This indicator helps notify you when you have Alta Control Center notifications even if you are
viewing a different browser tab.
l
The dot is removed when you click a notification or close all alerts in the Alta Control Center.
Note: Ensure the audio on your device or machine is enabled when using the alarm notification sound.
Set your preferred language
You can set your preferred language to French, Spanish, Italian, German, or English in the Alta Control Center.
Get started 12

Set language at sign-in
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
Note: The Alta Control Center is shown automatically in French, Spanish, Italian, German, or English
based on the language and locale set in your browser.
2. Select your preferred language in Language in the lower-left corner.
3. Click Sign in. The selected language is shown in your current login session.
Set language in your profile
1. Click your name in the upper-right corner and select Profile.
2. Select your preferred language in Language.
3. Click Save. The selected language is shown every time you log in to the Alta Control Center.
Set language in organization-wide emails
1.
Go to Administration > Account.
2. Click Change settings in the Info section.
3. Select the preferred language in Organization Language.
4. Click Save. All Alta Control Center emails for the org will be sent in the selected language.
Set language in site-wide emails
1.
Go to Sites > Sites, and select a site or click the Add Site button.
For multiple site creation, go to Administration > Quick start and follow the screen workflow.
2. Select the preferred language in Site language.
3. Click Save. All Alta Control Center emails for the site will be sent in the selected language.
Terms
l
ACU — Access Control Unit. A cloud-based control panel that manages access to a secured area.
ll
Avigilon Alta Open app — Used for providing mobile credentials and remote unlock for users. The app is
available for iOS and Android devices.
l
Cloud Key credential — A credential that lets users generate links to provide temporary access through the
Avigilon Alta Open app or Alta Control Center.
Get started 13
l
Control Center — An online portal that lets administrators manage users, set up entries and permissions, and
troubleshoot hardware.
l
Credential — A key presented to a reader to gain access to an entry. Examples include key cards, fobs, and
mobile credentials.
l
CSN — A card serial number on the key card.
l
Entry — A door, gate, turnstile, elevator floor, or other point of access. Often secured with a reader or wireless
lock.
l
Entry state — Determines whether an entry is locked or unlocked and defines what kinds of credentials and
trigger methods are valid.
l
Mobile credential — An access method tied to a user's smartphone through the use of the Avigilon Alta Open
app.
l
Remote unlock — A feature that lets users unlock an entry using the Avigilon Alta Open app without needing
to be in rangeof the Avigilon reader. Supported in gateway-connected devices.
l
Request to Exit (REX) — A sensor that detects when someone is exiting an entry which lets the Smart Hub
ACU know to unlock the door.
l
Schedule — A set of defined dates and times that can be used to restrict access to entries or users.
l
Site— A physical location (usually a building) that contains zones and entries.
l
Smart Reader — A device installed near an entry capable of reading information stored on keycards, fobs, and
Avigilon mobile credentials.
l
Trigger method— A combination of credential type and 1FA/2FA.
l
User— A person defined in the Control Center with credentials.
l
Wiegand reader— A device installed near an entry capable of reading information stored on a Wiegand card
and transmitting to an access control unit.
l
Zone — Contains one or more entries within a site. Zones are the units of physical access permissions that
you assign to users and groups.
l
1FA — Single-Factor Authentication.
l
2FA — Two-Factor Authentication.
For more information
Technical support
For additional support documentation, see help.openpath.com.
Product documentation
For additional product documentation, see the Avigilon Alta (Cloud Solutions) product suite on
avigilon.com/product-documentation.
Get started 14
Workflows
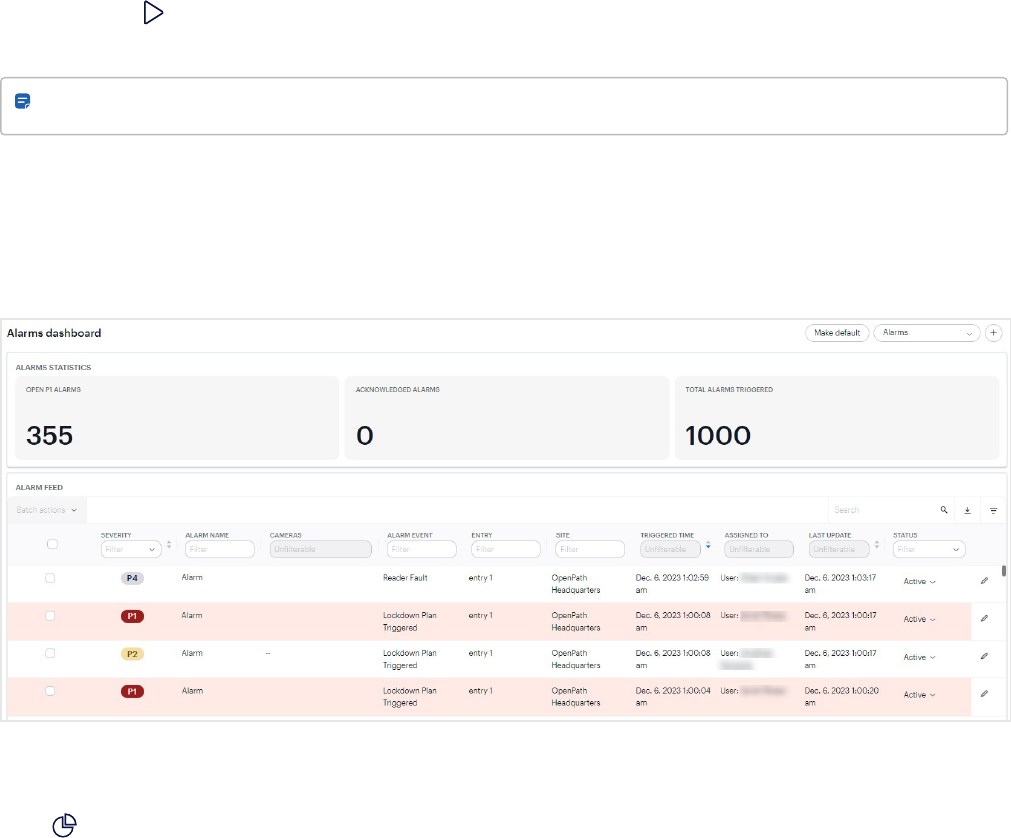
Alarm Management workflow
Note: A Premium or Enterprise plan is required.
The Alarm Management app supports alarm configuration, monitoring, and reporting for alarm monitoring operators
and administrators. Use this app to configure and monitor visual and audible alarms, and take the necessary actions
to resolve them.
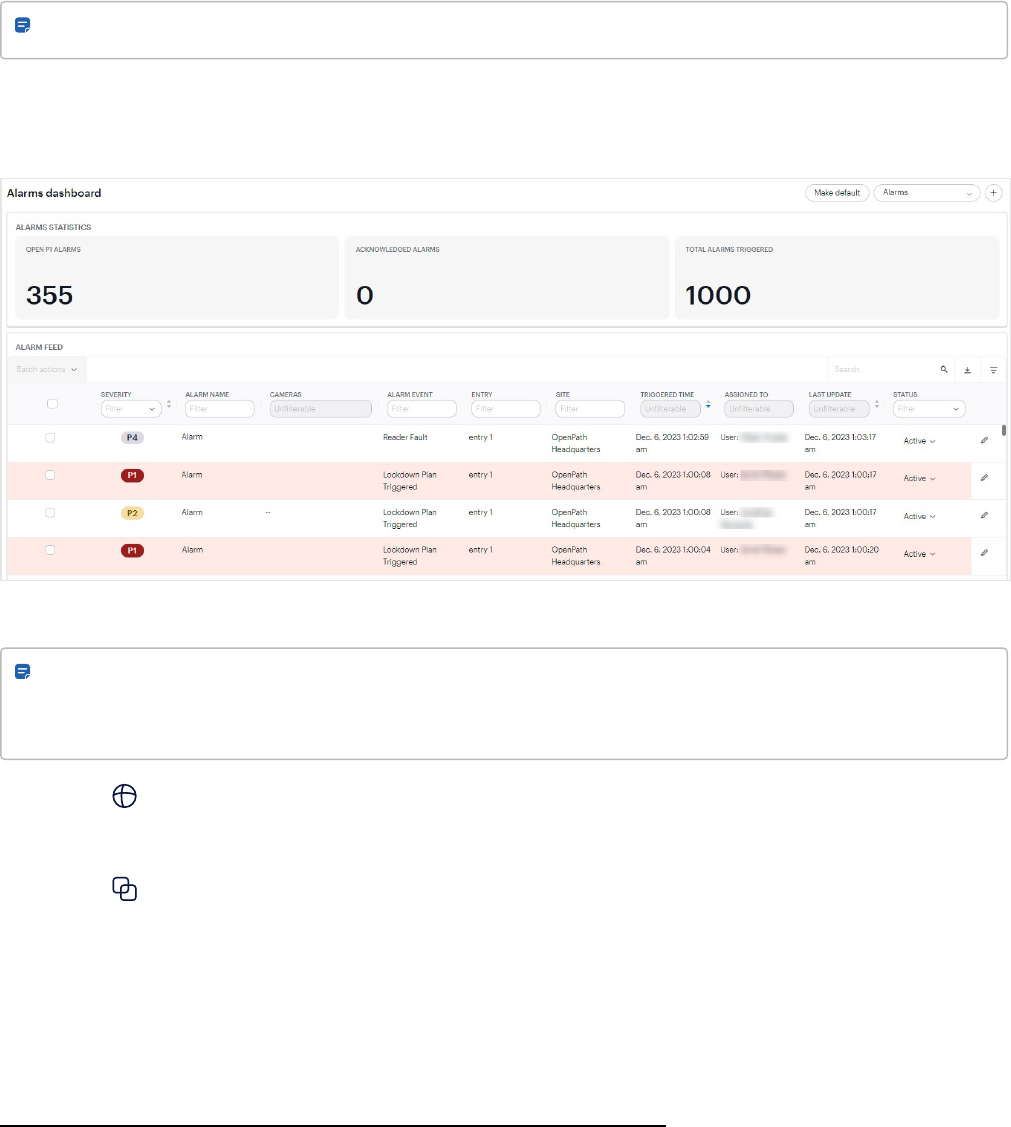
Figure 1 Example of triggered alarms in the Alarms dashboard
Note: If your Alta Aware and Control Center systems have been unified, you can define rules in the Alta Aware
video management system and use them to trigger alarms in the Alarms dashboard. For more information
about the Avigilon Alta Rules tool, see Aware documentation.
1
1.
Go to App marketplace and install the Alarm Management app, if not already done.
For more information, see App marketplace on page102.
2.
Go to Configurations > Alarms, configure the alarms, and assign them to roles or users.
For more information about configuration, see Alarms (Premium and Enterprise plans) on page131.
1
https://aware.docs.alta.avigilon.com/en/Products/aware/rules/awarerules.htm
Workflows 15
Note: The Premium plan supports 100 alarm configurations. The Enterprise plan supports 500 alarm
configurations. These limits include any Aware alarms that are configured in the Control Center.
Notifications to the assigned monitoring operator can be specified in an alarm action. For more information,
see Action triggers and alarm notifications on page134.
3.
Go to Dashboards, and add the Alarm feed and Alarm statistics widgets to your custom dashboard. Or,
change Activity to Alarms in the upper-right corner. For an example, see Figure 1 on the previous page. For
more information, see Alarms dashboard on page26 and Custom dashboards (Premium and Enterprise
plans) on page31.
Note: The Premium plan supports 100 open alarms. The Enterprise plan supports 1000 open alarms.
These limits include any Aware alarms that are configured in the Control Center.
Notifications are sent as these limits are approached, and again, when the limit is reached. After that, old
open alarms are auto-cleared as new alarms are triggered. For more information, see Alerts by email or SMS
on page129.
4.
Go to Reports > Alarms, and configure the data to be displayed in the report. For example, configure an
Alarm report that includes the users who triggered the alarms (see Triggered column) and the assigned
monitoring operators who acknowledged the alarms with notes (see Note Added column).
For more information, see Configure reports (Activity logs, Alarms, and Portal audit report) on page100.
Muster Reports workflow
Note: A Premium or Enterprise plan is required.
The Muster Reports app is an emergency response tool to quickly view the Avigilon Alta users who may be in your
building during an emergency evacuation. Use this app to rapidly generate a report, identify who may be on site, and
account for their safety.
1.
Go to App marketplace and install the Muster Reports app, if not already done.
For more information, see App marketplace on page102.
Workflows 16
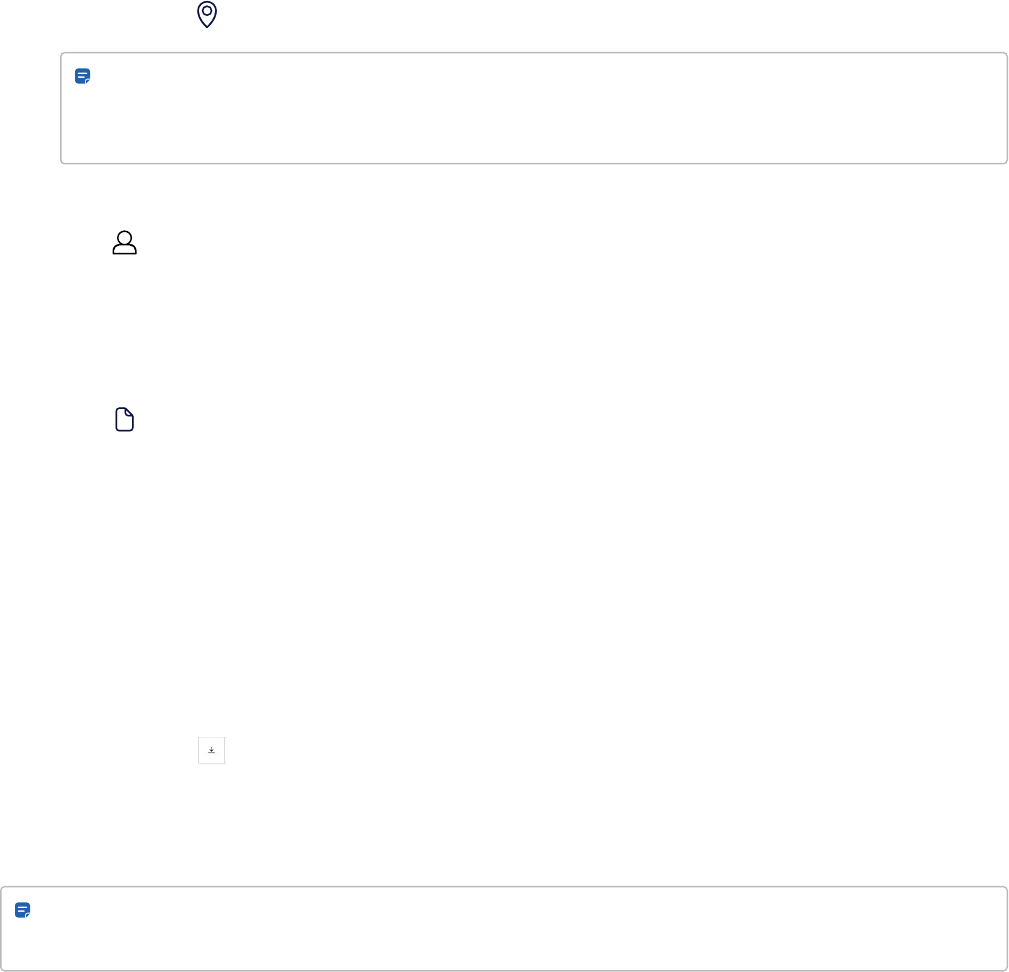
2.
Optional. Go to Sites > Entries, and add an entry for the muster point.
Note: Optional muster point entries can be installed at your emergency assembly locations. A
credential reader is required to be installed at the entry. The reader should only be used in a muster
event and not for any other purpose.
For more information, see Add entries on page61.
3.
Go to Users > Roles and select the role that will view and edit muster reports.
a. Scroll down to the REPORTS section and find Muster report.
b. Select the View and edit a muster report toggles.
c. Click Save.
4.
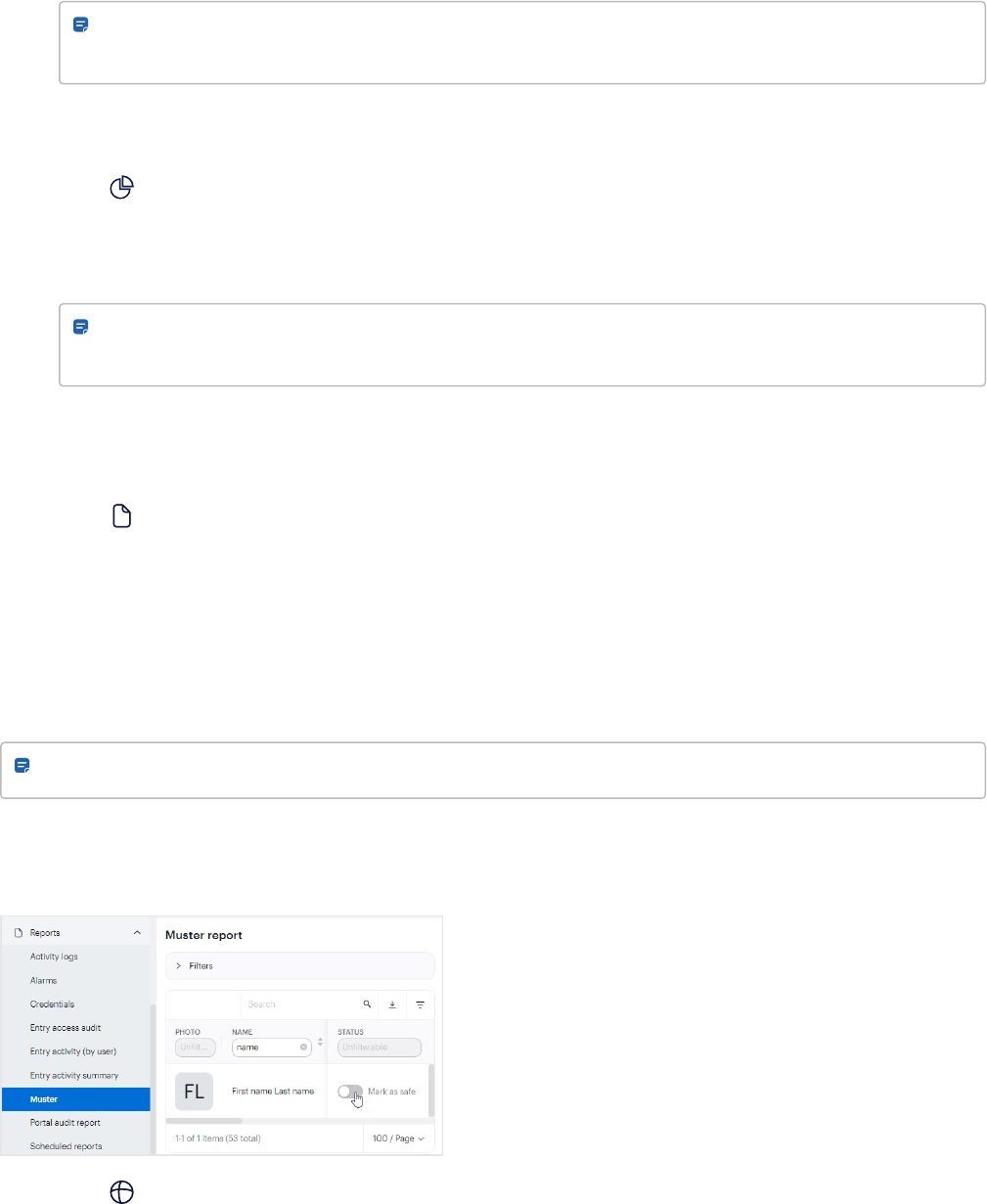
Go to Reports > Muster and generate a report.
a. Select a time period for the report.
b. Optional. Select sites and zones.
c. Click Search. Do any of the following:
l
Select the Mark as safe toggle in the generated report after you have ensured a user is safe.
l
View the users who are automatically marked as safe in the generated report, if their credentials
were scanned at the muster point entry before you generated the report.
5. Export the report to CSV for record keeping.
l
Click the icon.
Alta Aware, Alta DMP, and Control Center workflow
Note: The preview features in this section are not available to all organizations. DMP is only available to Alta
Aware partners and resellers.
If your Alta Aware, Alta Deployment Management Portal (DMP), and Alta Control Center systems have been unified,
you can use three-way app navigation (see example below) and the same password for those systems. If the Alta
Aware app integration is enabled, you will have access to video playback of Avigilon Ava camera feeds, access event
sharing, and more. If the Control Center Alarm Management app is installed, you can can define rules in Alta Aware
and use them to trigger alarms in the Alarms dashboard (seeAlarm Management workflow on page15) . If the Alta
Deployment Management Portal (DMP) is enabled for Alta Aware partners, they will have access to an app for
managing their customer deployments.
Workflows 17
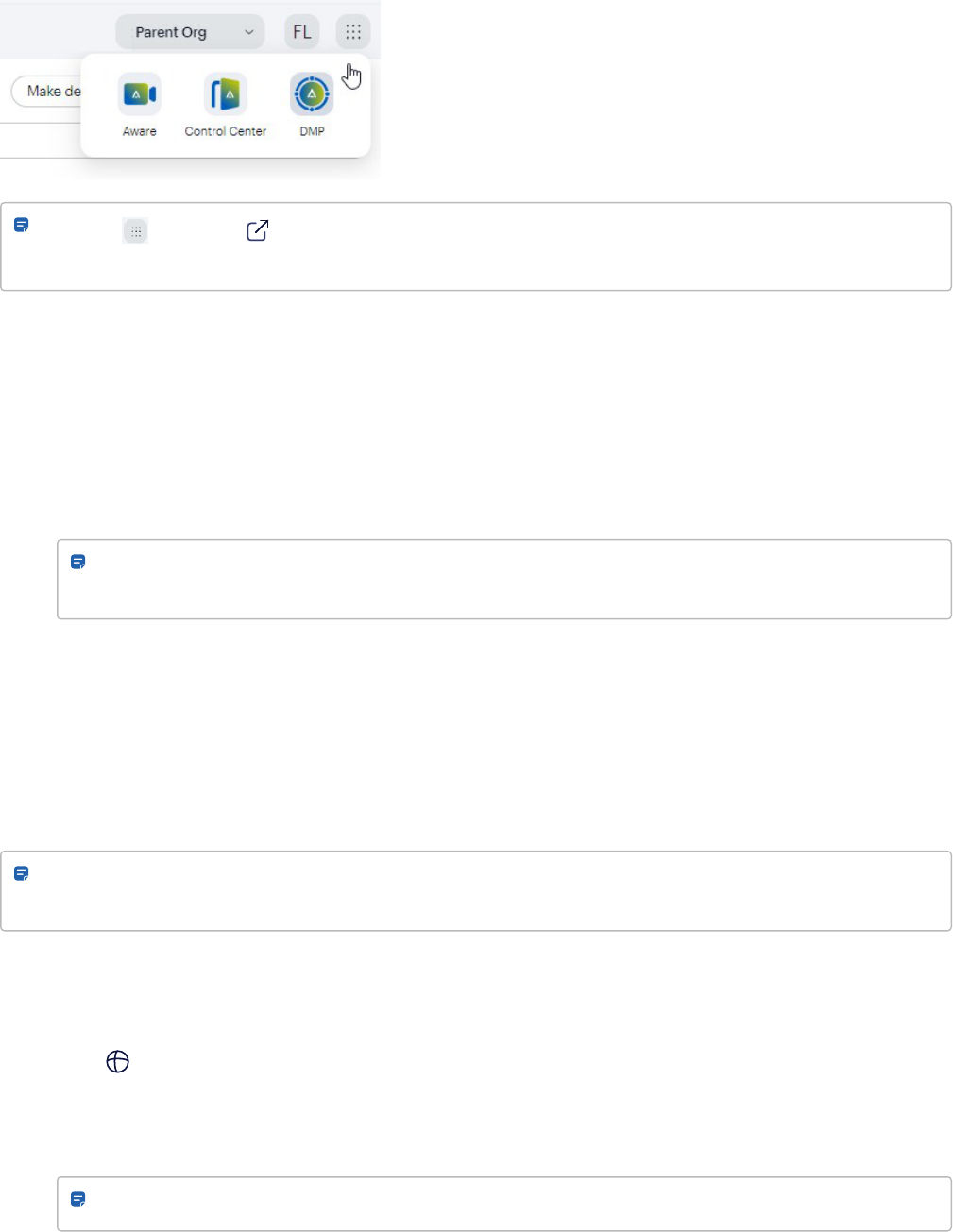
Note: The button and app switcher links cannot be disabled (default setting). Administrators may
contact support.avigilon.com for more information.
User and role management
To give an Alta Aware user access to the Alta Control Center:
l
In the Alta Aware dashboard, add the Alta Aware user to the Administrators user group.
The Aware Default Role is assigned automatically and generates an email invite to set up a password for the
new Alta Control Center account. For more information about default roles, see Role management on
page46.
Note: If your Alta Aware and Control Center systems have been unified, the Alta Control Center
password must be used to sign in. The Alta Aware password is no longer used in both systems.
l
To assign more permissions in the Alta Control Center, see Add users on page37.
To give an Alta Control Center user access to the Alta Aware video management system:
l
Assign the Aware Default Role to the Alta Control Center user account. For more information about default
roles, see Role management on page46.
l
Or assign the Operators role to the user account in Alta Aware. If more permissions are needed, see Aware
documentation.
Note: Alta Aware SSO users do not have access to the app switcher links in both Alta Aware and Alta Control
Center. Alta Control Center SSO users cannot sign in using the Alta Aware sign-in page.
Video playback and access events
To view the Avigilon Ava cameras and access events in Alta Control Center:
1.
Go to App marketplace and install the Alta Aware video management system, if not already done.
For more information, see Alta Aware app on page121.
2. Sign in to Alta Control Center or Alta Aware using the Control Center password.
Note: The Alta Aware password is no longer used.
Workflows 18
If signing in through Alta Aware, select the button and then Control Center.
3.
Go to Cameras and select any Avigilon Ava camera connected through your Alta Aware account.
For more information about video playback, see Cameras on page34.
4.
Go to Dashboards, and add the Activity logs and Visual activity report widgets to your custom
dashboard. Or, change Activity to Activity logs or Visual activity report in the upper-right corner to view
relevant access events.
For more information about access events, see Dashboards on page25 and Reports on page98.
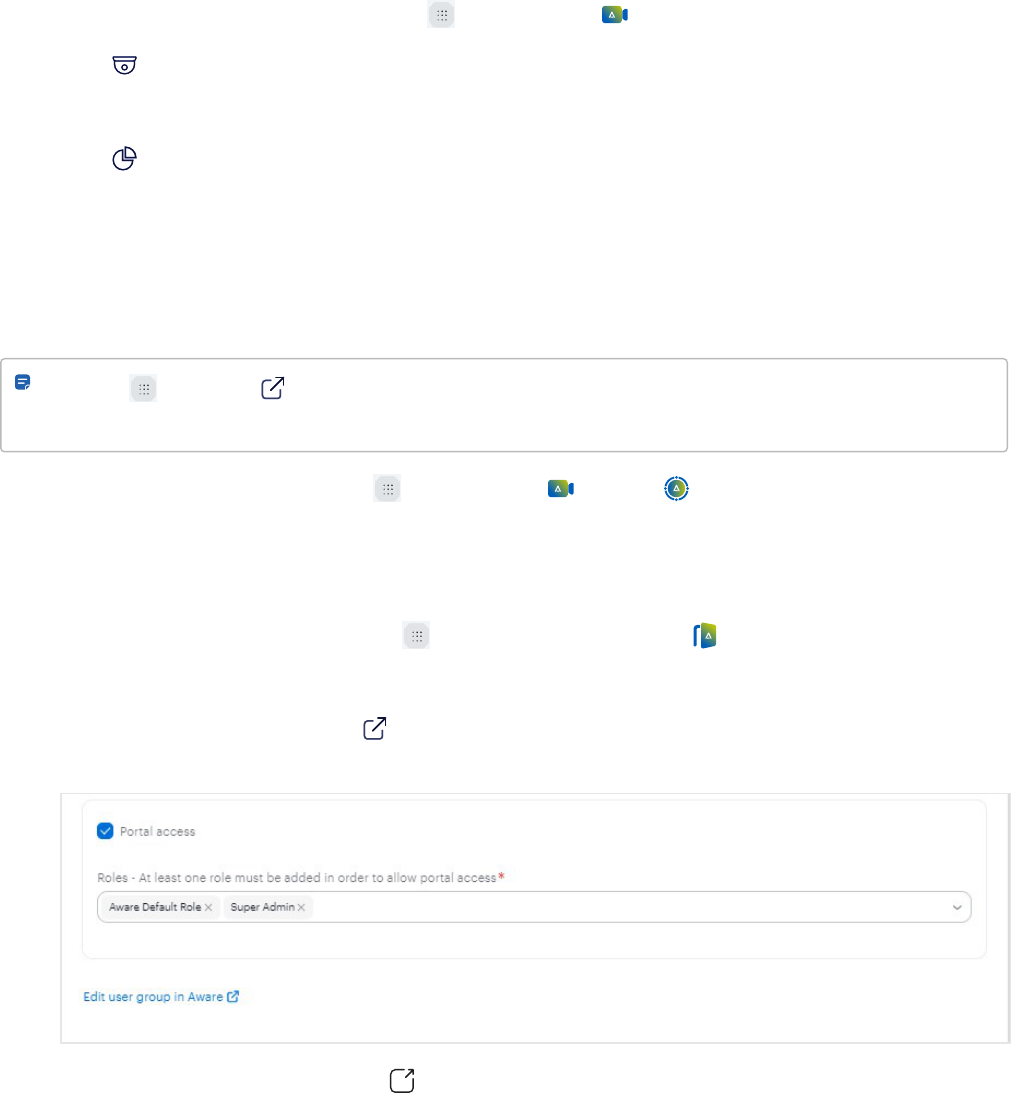
Aware, DMP, and Control Center app navigation
Note: The button and app switcher links do not work in Chrome™ Incognito mode or private mode. Alta
Aware SSO users do not have access to these links.
l
In the Alta Control Center, select the button and then Aware or DMP (Deployment Management
Portal), if the latter is enabled for your user account in Alta Aware.
The Alta Aware page is displayed on a new browser tab, already signed in. For more information about the
Aware dashboard or the DMP portal, see Aware documentation and Aware DMP documentation, respectively.
l
In the Alta Aware dashboard, select the app switcher button and then Control Center.
The Alta Control Center page is displayed on a new tab, already signed in.
l
In the Alta Control Center, click the link (example is shown below) on the Edit user page or Entry
dashboard page. Alta Aware is displayed on a new tab.
l
In the Alta Aware dashboard, click the link (example is shown below) on the Edit access settings in Control
Workflows 19
Center. Alta Control Center is displayed on a new tab.
Triggering lockdown plans
Note: A Premium or Enterprise plan is required. You must also have a Cloud Key credential to trigger and
revert lockdown plans from the Alta Control Center.
Lockdown plans for an organization can be triggered or reverted in any of the following ways. If you need to create a
lockdown plan, see Lockdown plans (Premium and Enterprise plans) on page69.
Use Control Center menu bar
Note: To view the Lockdown dropdown menu, users must be assigned the Lockdown - Override Only state.
See Assign permission to override lockdowns on page43.
1. Click Lockdown next to your organization and profile in the top-right corner.
2. When a lockdown situation occurs, click Trigger on the lockdown plan.
Workflows 20
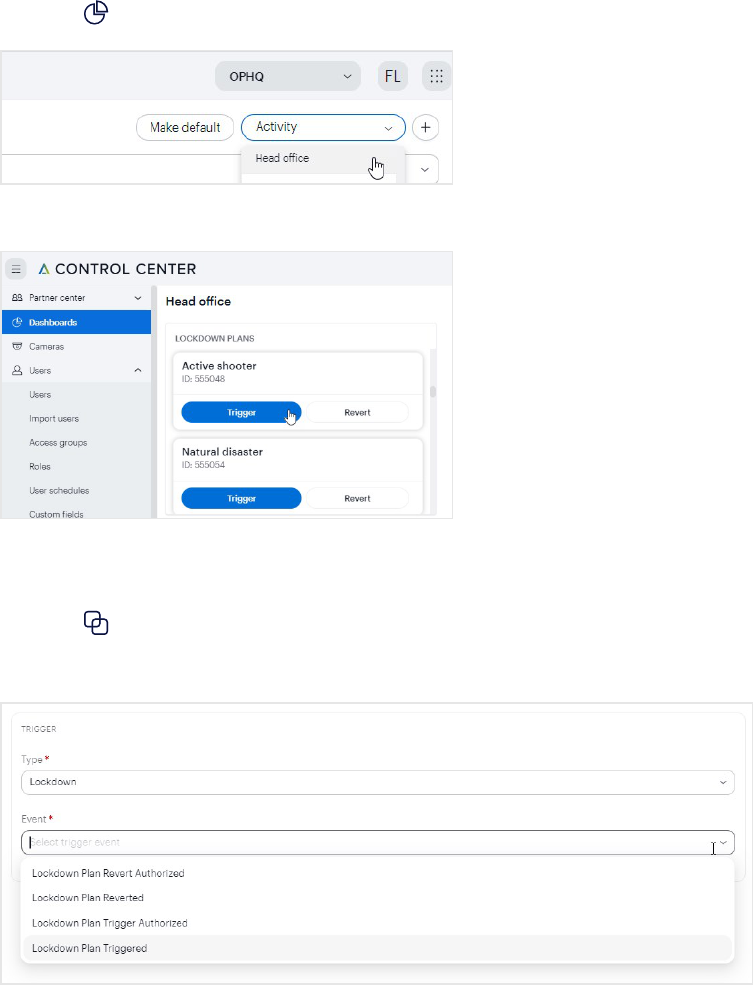
If a lockdown plan is triggered, the Lockdown menu name changes to red.
3. When the lockdown situation is resolved, click Reverton the lockdown plan. The lockdown plan is reverted
and the red flag is removed.
Use Lockdown widget on custom dashboard
1.
Go to the Dashboards page and select the custom dashboard in the upper-right corner.
2. When a lockdown situation occurs, click Trigger, or when a lockdown situation is resolved, click Revert.
Use Lockdown event triggers
1.
Go to the Configurations > Alarms or Rules.
2. Set up the lockdown trigger for the alarm or rule.
Workflows 21

User profile
View and edit your profile as follows.
1.
Go to in the upper-right corner of the Alta Control Center.
2. Click Profile.
Update your account information
1. On the Info tab, edit your email and name.
Note: An account imported from an identity provider cannot be edited.
2. Select your preferred language in Language.
3. Click Save.
Change password
1. On the Password tab, enter your old and new passwords.
2. Click Save.
Add MFA devices
For extra security, add one or more multi-factor authentication (MFA) devices that can generate a passcode for two-
step identity verification at time of login.
Note: Before you start, ensure a Time-based One-Time Password (TOTP) compatible app is installed and
configured on your device.
1. On the Security tab, click Add MFA device.
2. In MFA device type, select TOTP soft device Google Authenticator, Authy, Duo or compatible).
3. Enter a name for the device and click Next. A QR code is generated.
4. Set up the app on your mobile or desktop device by scanning the QR code.
If your device can't scan, click (show secret) to display the contents of the QR code. Go to your app and type
the code.
5. Enter the code generated by the app in the Enter 2FA code field.
6. Click Activate MFA device. The device is added.
User profile 22

Enable intercom notifications
1. On the Settings tab, select the Enable intercom notifications toggle to receive notifications from the Video
Intercom Reader Pro.
2. Click Save.
When enabled, the following is shown:
ll
A visual indicator (blue dot) in the browser tab indicates new notifications.
Tip: This indicator helps notify you when you have Alta Control Center notifications even if you are
viewing a different browser tab.
l
The dot is removed when you click a notification or close all alerts in the Alta Control Center.
Play or mute alarm notification sounds
Note: A Premium or Enterprise plan is required. Ensure the audio on your device or machine is enabled when
using the alarm notification sound.
On the Settings tab:
l
To play the default sound when an alarm is generated, select the Play alarm notification sounds toggle
(default).
l
To mute the default sound, deselect the toggle and click Save.
Enable Dark mode, Light mode, or Match system theme
l
On the Settings tab, select the Dark mode (shown below) or Match system theme, which uses the current
theme of your operating system. Light mode is the default theme.
User profile 23
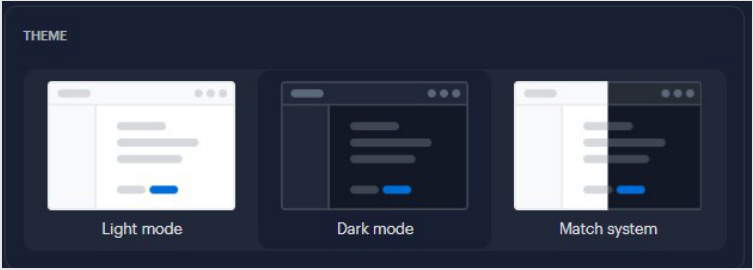
The selected theme is displayed every time you log in to the Alta Control Center.
User profile 24

Dashboards
The Dashboards page lets you monitor access control events in the default Activity, Alarms, Device, and Entry
dashboards, and to create custom dashboards for your org.
Note: If you are viewing Schlage no-tour wireless locks, information may be out-of-date. Dashboard
information is available only after visiting the no-tour wireless lock in person and completing a manual sync
using the Avigilon Alta Access app.
Activity dashboard
After signing in, you'll see the Activity dashboard which shows a live feed of recent access events, as well as
statistics about event activity and active users. Click the name of a user to view their details.
Note: When the 1,000 event limit is reached in the dashboard, the events over the limit are cleared on an
hourly basis. To view the cleared events, go to Reports > Activity logs.
Filter by site
l
At the top of the Activity dashboard page, select a site to narrow down the list of event activity.
Dashboards 25
View camera snapshots
If you have the Avigilon Video Reader Pro or Video Intercom Reader Pro installed, or the Cisco® Meraki® or Alta
Aware camera integration enabled, you can view snapshots.
1. Go to the CAMERAS column in the Activity dashboard.
2.
Click the play icon to view video footage in the Alta Control Center or in the Meraki dashboard for the
Cisco integration.
Note: Video footage may take up to a minute to appear in the Alta Control Center.
Alarms dashboard
The Alarms dashboard shows a live feed of alarm events and statistics for alarm monitoring operators and
administrators.
Filter by alarm severity or status
Go to Dashboards and change Activity to Alarms in the upper-right corner.
l
Click the SEVERITY column in the alarm feed, and select a P1 to P5 level.
l
Click the STATUS column in the alarm feed, and select the Active, Acknowledged, Cleared, Cleared - False
Alarm, or Auto Cleared status.
Acknowledge, clear, or reactivate active alarms
Monitoring operators can respond to an Active alarm either in the Alarms dashboard or below the ALARM DETAILS
section of the alarm page, depending if notes are needed.
Dashboards 26
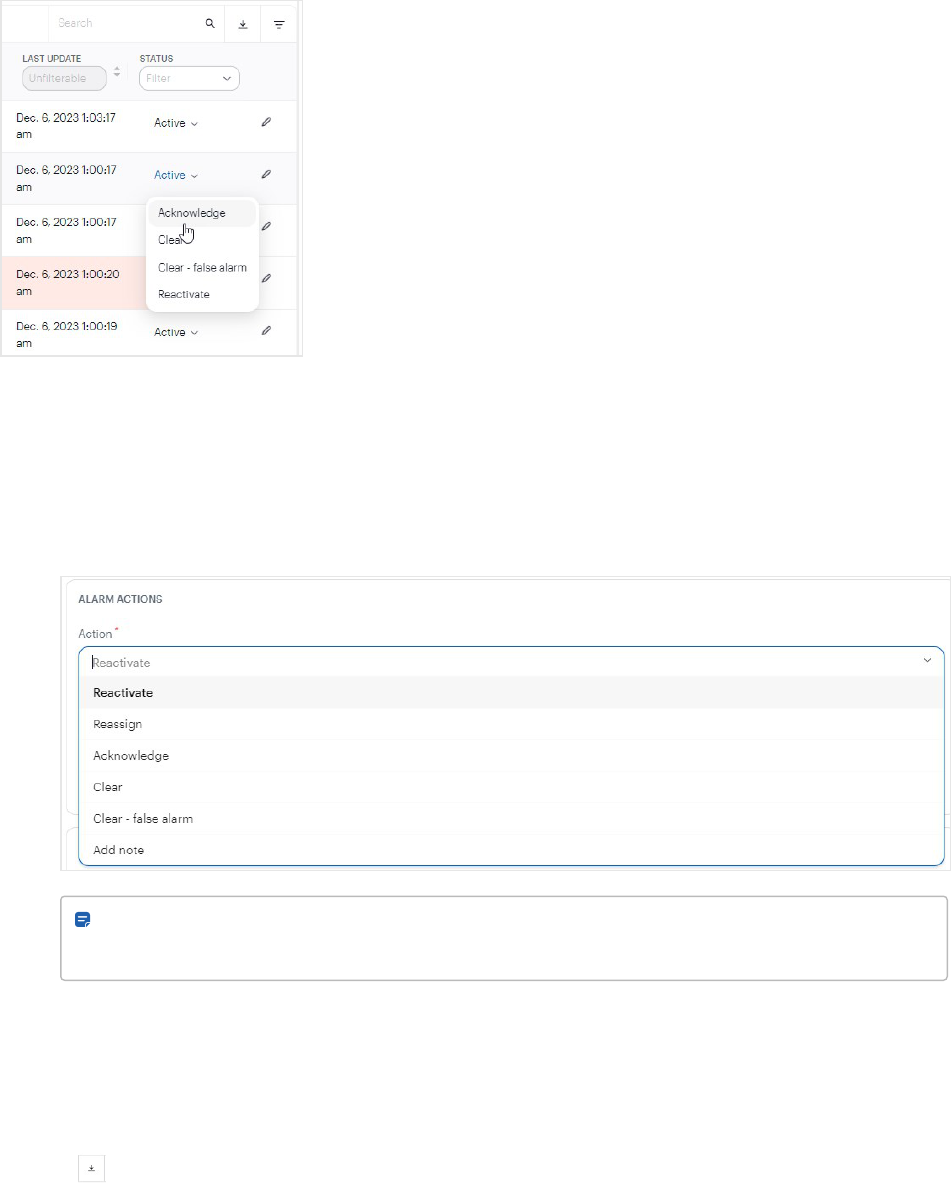
l
On the Alarms dashboard page, select an Active alarm in the STATUS column and an action.
(Reactivate takes an alarm out of a cleared state, back to an active state.)
l
To view the alarm page, click the alarm row or View alarm in an open alarm notification in the lower-right
corner.
a. On the alarm page, read the Instructions for handling the alarm.
b. Select the appropriate action in Action, and add a note.
Note: The alarm page includes the additional Add note action and Reassign action for
reassigning the alarm to another monitoring user.
c. Click Save.
Export alarm history
In the HISTORY section of the alarm page:
l
Click the icon.
Dashboards 27
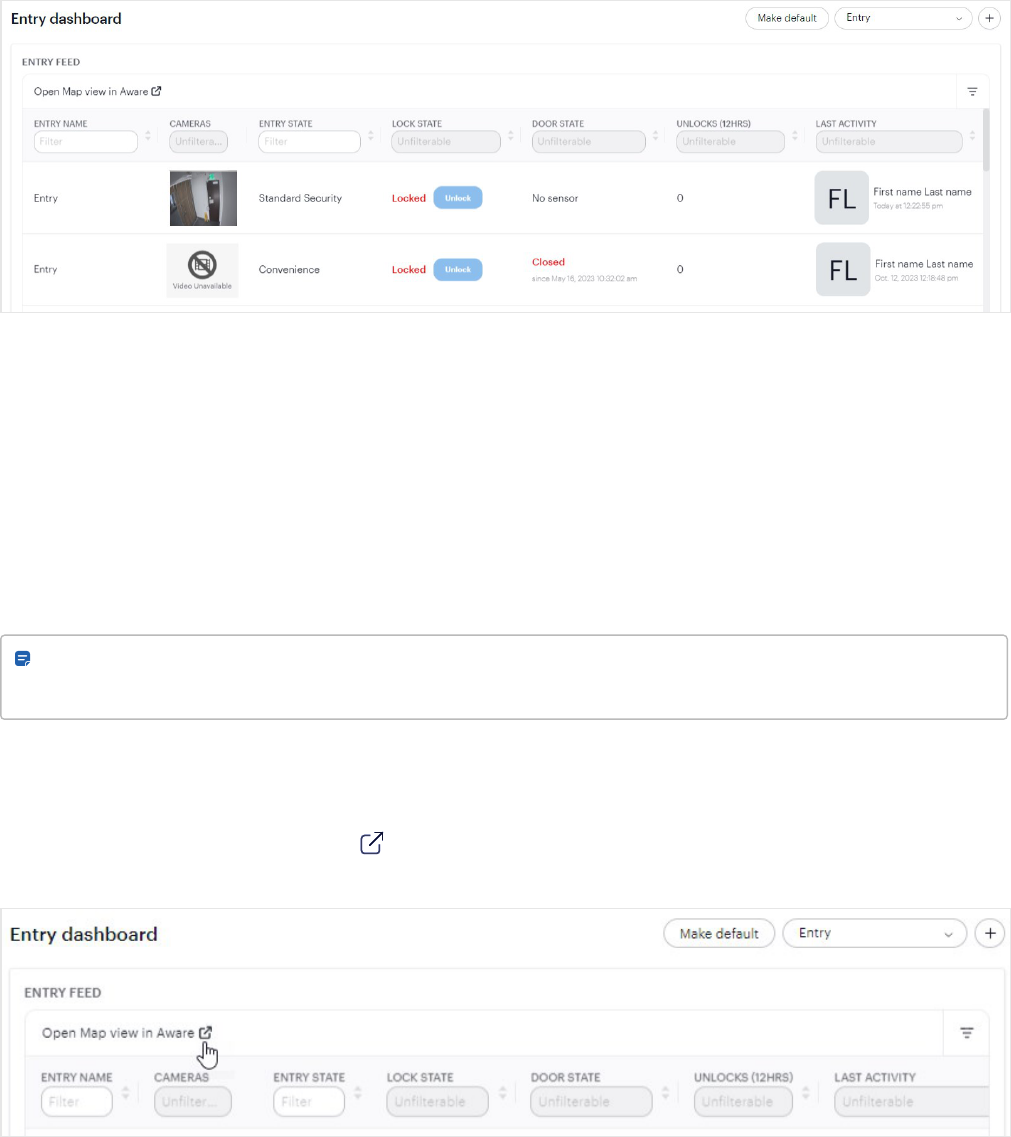
Entry dashboard
The Entry dashboard shows the live status of every entry in your site.
View usage statistics of an organization
This is where you can see your organization's usage statistics as well as the current lock state for entries. The data
on the Dashboard is real time, so as soon as an entry unlock request is made or denied or a lock state changes, the
data displayed will update immediately.
Unlock entries
If you have a Cloud Key and remote unlock permissions (and the entry's state also allows remote unlock requests),
you can unlock entries from the Main Dashboard by clicking the Unlock button next to the entry's name.
Note: If a door is ajar or not properly closed, the Door Ajar alarm will be prominently displayed in the Door
State column.
View entries on maps in AwareVMS
If your Alta Aware and Alta Control Center systems have been unified and you have the permissions in Alta Aware to
view maps, the Open Map view in Aware link will be visible. Click to go directly to the Map view tool in the Alta
Aware system. For more information, see Aware documentation.
Dashboards 28
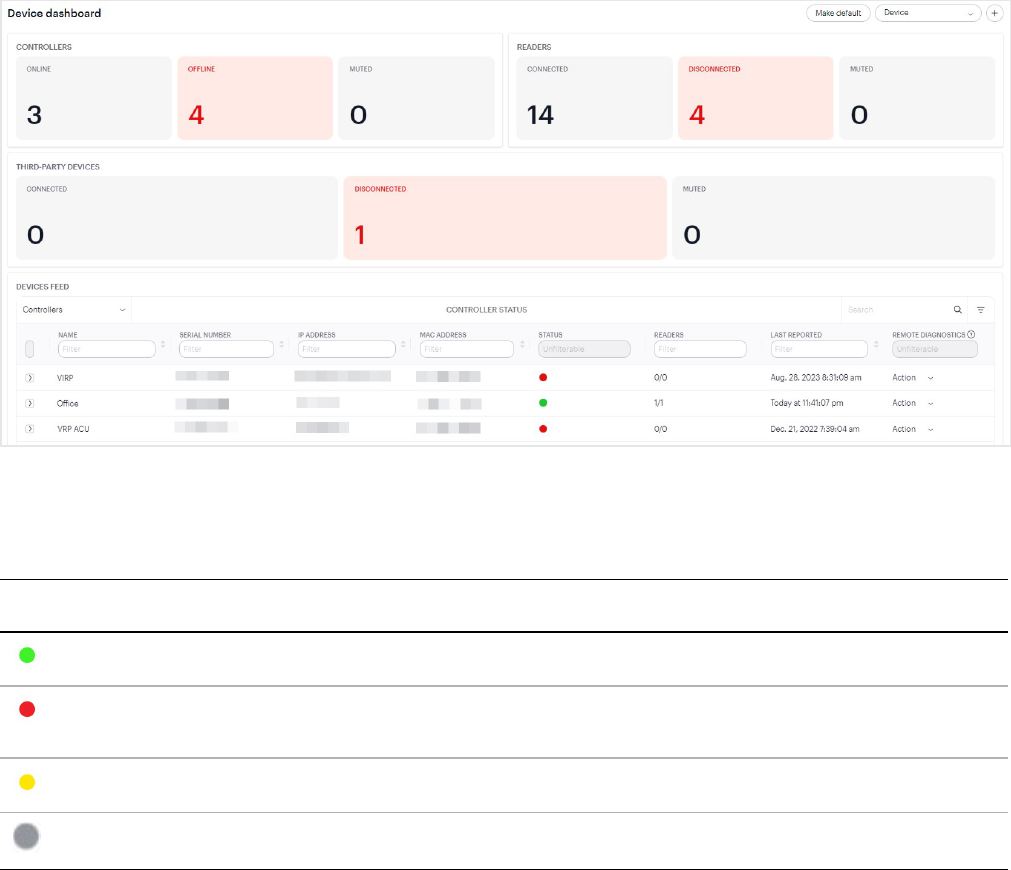
Device dashboard
The Device dashboard is where you can get a high-level overview of your organization's controllers (ACUs and SDCs)
and readers.
Controller and reader status
The dashboard indicates the online status of controllers and readers in the STATUS column.
Color Description
Green The controller or reader is online and communicating as expected.
Red The controller or reader is offline. The last message received from the controller is more than 60
minutes old, or more than 20 minutes old and the VPN is down.
Yellow The last message received from the controller is more than 12 minutes old and the VPN is down.
Gray The controller or reader is muted in the Device dashboard.
Refresh controller data
1. Select the controller in the dashboard.
2. Select Action > Refresh in the REMOTEDIAGNOSTICS column.
The latest data is sent from the physical device to the Alta Control Center to ensure that the device is online.
Dashboards 29

Restart controller services
Note: Restarting a service may interrupt the affected service for up to 60 seconds. We recommend restarting
services one at a time, waiting a few seconds after restarting one before restarting the next.
1. Select the controller in the dashboard.
2. Select Action and a restart option in the REMOTEDIAGNOSTICS column.
l
Restart all services — Restarts all services on the controller.
l
Restart APIserver — Restarts the core application that processes authorization, authentication, and
execution of unlock requests.
Restart this service if issues occur with the Avigilon Alta Open app, such as unlock requests not
working.
l
Restart cloud communicator — Restarts the service that receives live messages from the cloud,
including entry configuration changes, user permissions changes, and cloud-based unlock requests.
Restart this service if changes, such as new credentials and new schedule, in the Alta Control Center
aren't syncing with the controllers, or if issues occur with remote unlock requests.
3. Click Yes.
Verify the physical reader is connected to Alta Control Center
1. Select the controller in the dashboard.
2. Select the reader from the list.
3. Select Action > Identify in the REMOTEDIAGNOSTICS column.
l
The outer ring LED on the physical reader will light up.
l
The center dot on the physical reader will light up green.
l
The buzzer on the physical reader will beep several times.
Restart the reader
1. Select the reader in the dashboard.
2. Select Action > Restart to force a reboot.
This will interrupt services provided by the reader for up to 60 seconds.
Mute the controller or reader
1. Select the controller or reader in the dashboard.
2. Select Action > Mute in the REMOTEDIAGNOSTICS column.
Dashboards 30
The status changes to a gray circle. Any alerts or rules created for the controller or the reader will not be
impacted. The device is muted only on your browser.
Custom dashboards (Premium and Enterprise plans)
You can create custom dashboards by adding widgets for use in your organization in addition to the Avigilon Alta
default dashboards (Activity, Alarm, Device, and Entry).
Note: Your dashboard can be viewed and edited by all Super Admin users in your organization.
Create custom dashboards
1.
Go to the Dashboards page.
2.
Click the button in the upper-right corner.
3. Enter a name for the dashboard and click Save.
4. Click Add your first widget in the tool tip and choose a widget.
l
Activity feed — A live feed of the entry activity log.
l
Alarm feed — A live feed of all alarm events. A Premium or Enterprise plan is required.
Dashboards 31
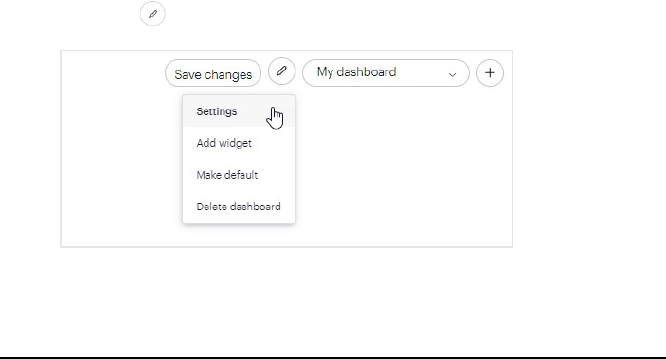
l
Alarm statistics — The open alarms, open P1 alarms, acknowledged alarms, and total alarms
triggered. A Premium or Enterprise plan is required.
l
Device count — The number of controllers and readers configured in the system and their online
status.
l
Entry controls — Lets you pin one or more entries to the dashboard and temporarily unlock them
instantly, or keep them unlocked for 5, 10, 15, or 60 minutes.
You need a Cloud Key credential
*
and appropriate access to one or more entries in order to trigger
unlocks.
l
Event feed — A live feed of entry events, door ajar and door propped open alarms, and lockdown
activations.
l
Lockdown — A list of all lockdown plans in the organization with buttons to trigger and revert plans. A
Premium or Enterprise plan is required.
You need user permission to trigger and revert lockdown plans. For more information, see Assign
permission to override lockdowns on page43 and Assign users and group permissions for lockdown
plans on page71.
l
Occupancy limit — The occupancy of areas configured using anti-passback.
You need to configure anti-passback and set occupancy limits to use this widget. For more
information, see Anti-passback and occupancy management on page58.
l
Statistics — The total events, number of active users, and percentage of active users from the last 12
hours.
l
User verification — Lets you monitor access events at a particular entry and displays a user's photo
when they unlock an entry.
l
Video player — A live feed of the selected video reader.
5. Click Save changes. The widget is added to your new dashboard.
Edit custom dashboards
l
Click the edit button in the upper-right corner for the customization options.
*
For more information, refer to https://help.openpath.com/what-are-cloud-key-credentials-and-how-do-i-send-guest-access-links-
HJ3crp38_.
Dashboards 32
Update dashboard title
1.
Select Settings from the menu.
2. Update the Dashboard title and click Save.
Add more widgets
1.
Select Add widget from the edit menu.
2. Choose a widget and do any of the following:
l
Click the icon to flip over the widget and see more configuration options.
l
Click in the upper-right corner to delete the widget.
l
Click and drag to place the widget anywhere on the dashboard.
l
Resize the widget by clicking and dragging the lower-right corner.
3. Click Save changeswhen you're done customizing the dashboard.
The custom dashboard appears in the Dashboards menu in the upper-right corner.
Set dashboard as default
l
Select Make default from the edit menu.
The custom dashboard appears at the top of the Dashboards dropdown menu in the upper-right corner.
Delete dashboard
l
Select Delete dashboard from the edit menu.
Dashboards 33
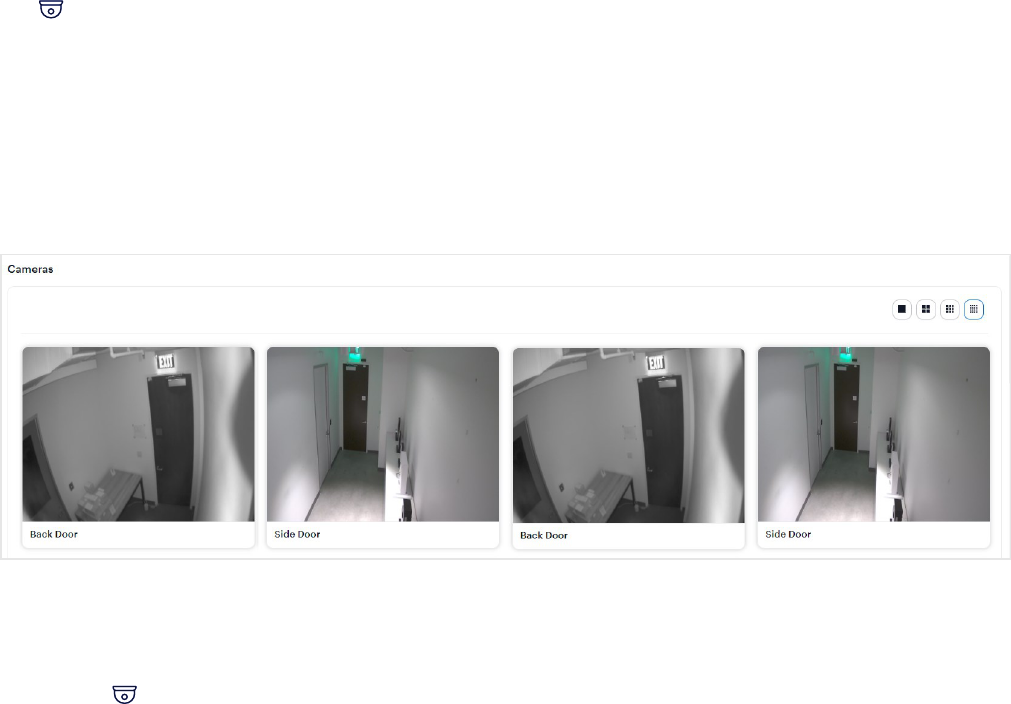
Cameras
The Cameras page shows all cameras in your org, including the cameras connected through your Alta Aware
account, Video Reader Pro and Video Intercom Reader Pro devices, and Cisco Meraki cameras.
l
Click a camera, video reader, or video intercom reader to view a live feed and list of events, such as door
unlocks, audio and motion detection, and tamper detection.
l
Initiate a call to the video intercom reader using the built-in microphone and speaker on your desktop or the
Avigilon Alta Open app.
l
Click a Cisco Meraki camera to go to the Cisco Meraki dashboard.
View live video feeds
l
Go to Cameras and select a camera.
A live video feed is shown at the top.
Cameras 34
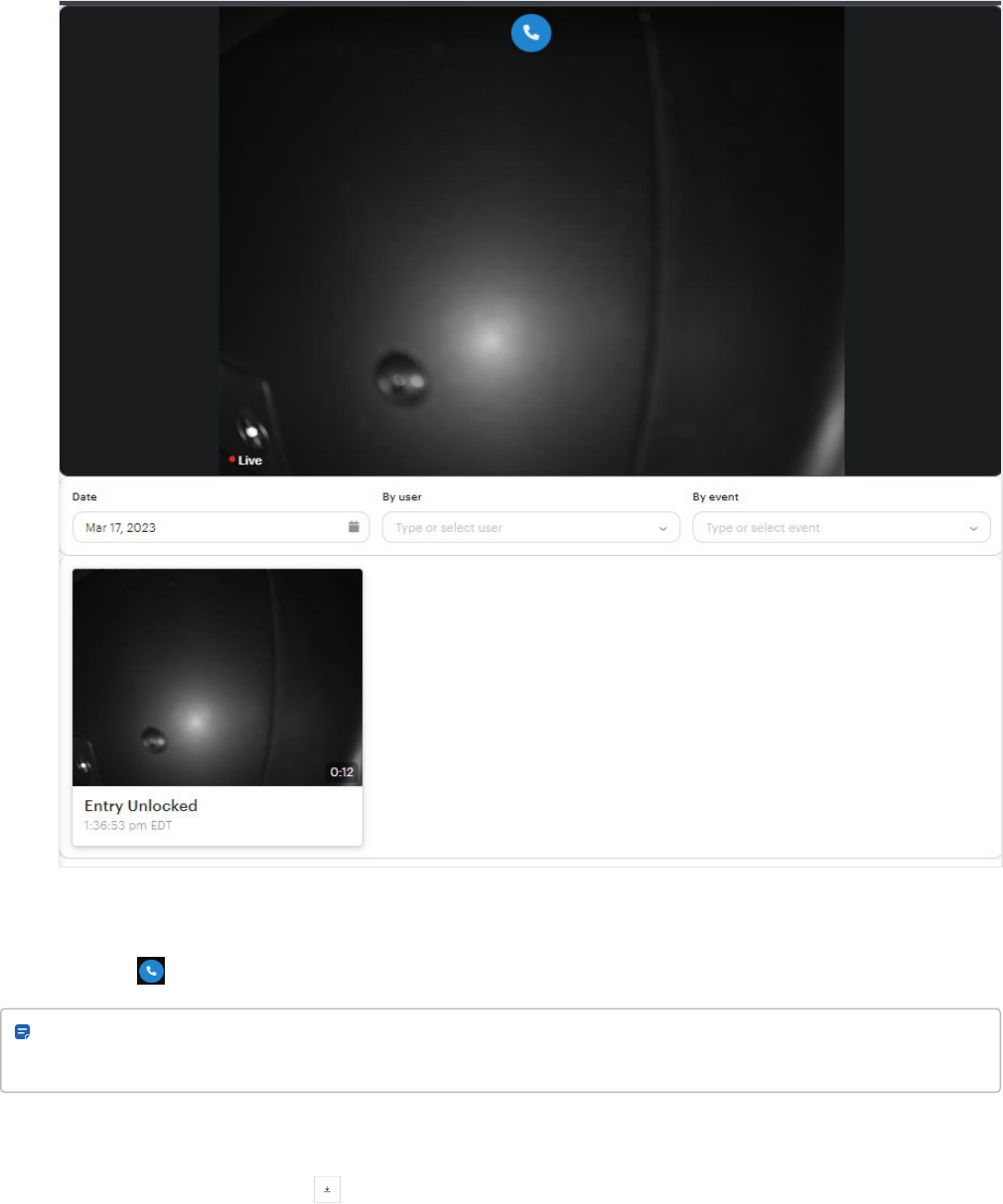
Initiate calls to intercom on Video Intercom Reader Pro
l
Click the phone button on the live video feed.
Note: Calls are not supported in Safari and Firefox browsers. Users can also click the phone button on the live
feed in the Avigilon Alta Open app.
Play and download video
1.
Play a recording and click the button in the upper-right corner.
2. Find the MP4 file in the Downloads folder on your desktop.
Cameras 35
Users
The Userspage lets you manage and import users, create and define groups, credentials, and roles.
User data model
If you have access to more than one organization (org) in the Alta Control Center portal, or you are using multiple
identity provider integrations with SSO enabled, you should be familiar with the Alta Control Center user data model.
This model allows a single identity to access multiple orgs, which is useful for resellers and installers that need to log
in once but have access to many orgs.
Namespace
Identity provider or localorg
Ü
Identity
SSO or local authentication
Email + name + password
ß Ü à
User
Org 1
Role + entry access
User
Org 2
Role + entry access
User
Org 3
Role + entry access
Users 36
Data Description
Namespace A contained pool of emails, all of which must be unique within the namespace. The two types of
namespaces are identity provider and local org.
Namespaces allow the flexibility of having multiple instances of the same email that come from
different sources or have different authentication mechanisms, such as local password
authentication or SSO.
under the local org namespace that is authenticated through email and password. If you sync with
under the identity provider namespace.
Identity The data record of a person needing access to the Alta Control Center, including email, first name,
last name, and other information. An identity is separate from, but related to a user.
Identities are authenticated when signing in to the Alta Control Center. For the supported identity
provider integrations, see Identity management on page102.
User An instance of an identity that belongs to a specific org. A single identity could have multiple
users. User configurations include portal access, roles, and entry access for a particular org.
User management
Tip: You can choose to use the Avigilon Alta Access app (formerly, Open Admin) to perform user man-
agement on your mobile device.
For more information, see this Avigilon Alta article.
App Store® and the Apple logo® are trademarks of Apple Inc. Google Play and the Google Play logo are trademarks of Google LLC.
Add users
1.
Go to Users > Users.
2.
Click the button in the upper-right corner.
3. Enter the user's email, name, and mobile phone number.
Note: If the email matches a deleted user, that user will be reactivated with all the permissions and
credentials they had before deletion.
Users 37
Note: If the user belongs to another organization, you can skip the name and enter a checkmark in the
Add a user from an existing namespacebox and the namespace in Namespace. For more
information about namespaces, see User data model on page36.
4. Enter other fields, as needed.
l
Start date/time, End date/time, and Timezone.
l
Person ID, External ID — For employee IDs or other useful information.
l
CUSTOMFIELDS — Additional fields that are configured by your administrator, such as License Plate
Number.
l
Portal access — For a user who is an admin and requires access to the administrator web portal, add
the Super Admin role. For the default roles that are assigned automatically by the system, see Role
management on page46.
Note: Only give administrator portal access to users who require it, such as an office manager
or security guard. To give someone limited access to the Alta Control Center, create a role with
granular permissions, as described in Assign permissions to roles on page48.
5. Click Save. A unique User ID isassigned, which may be used in search filters.
6. Optional. See Upload photo below.
Note: If your Alta Aware and Alta Control Center systems have been unified and you have the permissions in
Alta Aware to view users, the Edit user group in Aware link will be visible. Click to go directly to the Users
list in the Alta Aware system on a new browser tab.
Upload photo
To upload the user's photo to the Alta Control Center and user's Avigilon Alta Open app:
1.
Hover your mouse over the photo tile on the user's page and click EDIT.
2. Click the + Add photo button.
Users 38
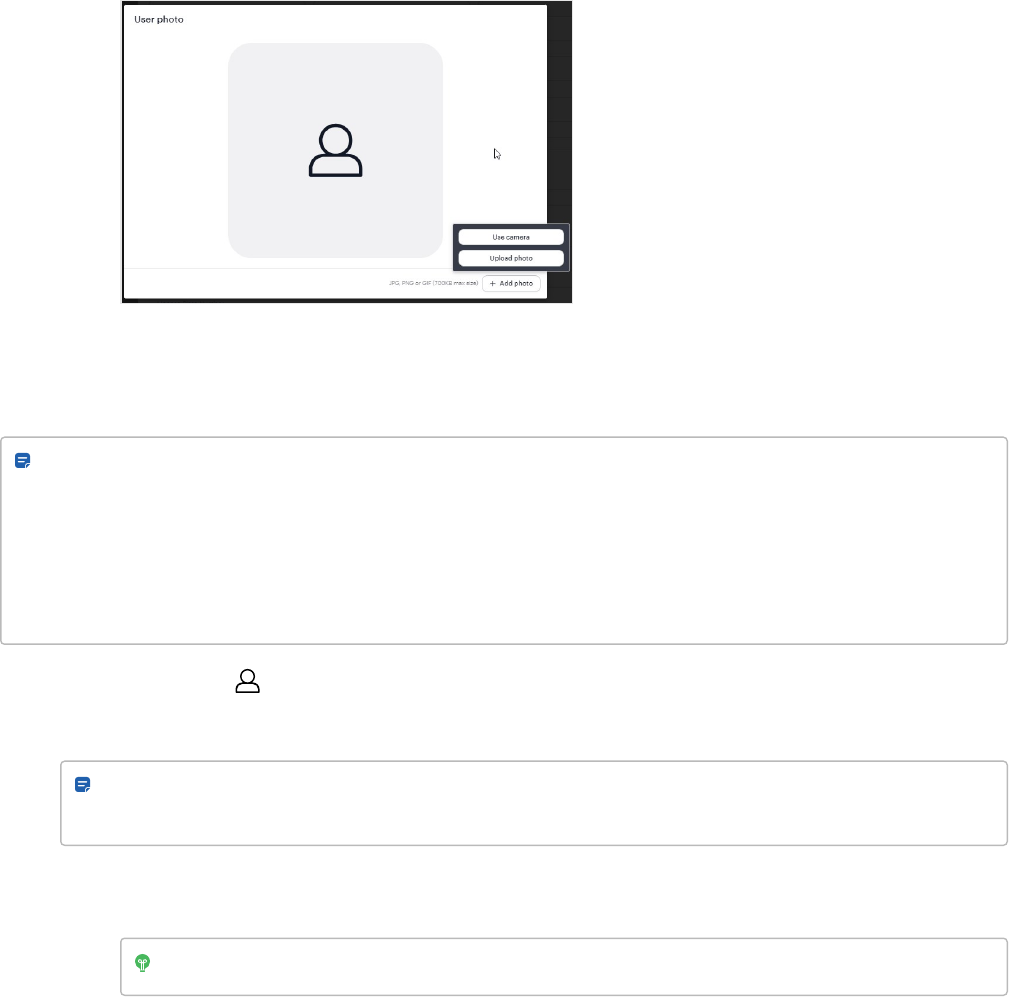
l
To take a new photo using your device's built-in camera or webcam, click Use camera and then Take
photo. Click Save photo.
l
To upload a new photo, click Upload photo and upload the photo. Click Save photo.
Issue keycard, fob, mobile, PIN, wiegand, or cloud-based credentials
You can issue credentials to a user. A credential is a keycard or fob presented to a reader to gain access to an entry.
Note: The EV3-B MIFARE® DESFire® cards can support a broader set of devices than the EV3-A DESFire
cards. If your org is planning to continue using EV3-A DESFire cards or to migrate to EV3-B cards, see this
Avigilon Alta article for the steps to maintaining backward and forward compatibility with your devices and
readers.
For information about issuing credentials to Schlage no-tour wireless locks, see the Avigilon Access Control
System Integration Guide for Schlage Wireless Locks No-Tour (link).
1.
Select a user on the page, and click the Credentialstab.
2. Select the type of credential to access an entry, depending on your device.
Note: If the Embedded USB Smart Reader is installed as an enrollment device, it supports only Avigilon
MIFARE and DESFire card credentials.
l
Card: Openpath DESFire (Encrypted) - Secure — An Avigilon (formerly Openpath) high-frequency (HF)
EV3 card.
Tip: The user may need to hold card on the reader a little longer than the CSN option.
l
Card: Openpath/MIFARE (CSN) - Fast — The Card Serial Number of an Avigilon HF card or fob.
l
Card: Schlage — A Schlage card or fob for Allegion Schlage wireless devices.
Users 39

l
Card: Wiegand ID — An Avigilon low-frequency key fob or card for Wiegand-based access control
systems. If you choose this option, see Add Wiegand credentials below after saving.
l
Cloud Key - For Guest Passes, Portal Dashboards, APIIntegrations — A web link issued by the
Avigilon Alta Open app or the Alta Control Center to grant temporary or scheduled access to an entry. If
you choose this option, see Generate guest access links and webhook URLs below.
l
Mobile — The Avigilon Alta Open app used to access an entry. If you choose this option, see Add
mobile credentials below after saving.
l
PIN — A PIN on the keypad of an Avigilon Smart Reader v2.
3. Enter the required information depending on the device.
4. Click Save.
Add mobile credentials
After saving a mobile credential:
l
Click Sendto email instructions to the user on how to set up their mobile device as a credential. The
Activation Pendingcolumn indicates that an email has been sent, but the user has not yet activated their
mobile credential.
Click Resend to issue another mobile credential to a new mobile device.
Add Wiegand credentials
After saving a Wiegand credential:
l
For Avigilon LF cards, select Prox 26-bit (H10301) in Card format.
l
If you don't know the card format, select Raw 64-bit in Card format and enter the Card number.
Note: If you don't know the card number, you can swipe the card at the reader and take note of the
rejected access entry in Reports > Activity logs. The card number will be displayed in the
CREDENTIAL DETAIL column.
l
To send card credential data to a third-party control panel, set Use for Gatewayto Enabled. You must also
configure the Wiegand reader to enable this feature. See Edit entries on page61.
Generate guest access links and webhook URLs
After saving a Cloud Key credential on the Credentials tab:
1. In the CLOUD KEYCREDENTIALS list, click Get webhook URL next to the credential.
l
The URL can be used to unlock entries through a web browser and shared with a guest.
l
The URLcan be integrated into the software or external services.
2. In the window pop-up, select the entries the URL will unlock:
Users 40

l
Entries (for example, front entry, rear entry)
l
Description
l
Start time and End time (optional)
3. Click Generate links.
l
For a Guest access link , click Copy to clipboard and share the URL with the guest.
l
For an API link, click Copy to clipboard and use the URL in your own software or external service.
Note: A Cloud Key credential can have multiple webhooks for multiple entries associated with it. Deleting a
Cloud Key credential will also remove all the valid webhooks associated with it.
Edit user access
You can assign groups, sites, and zones, and enable permission override and remote unlocking for a user.
Users 41
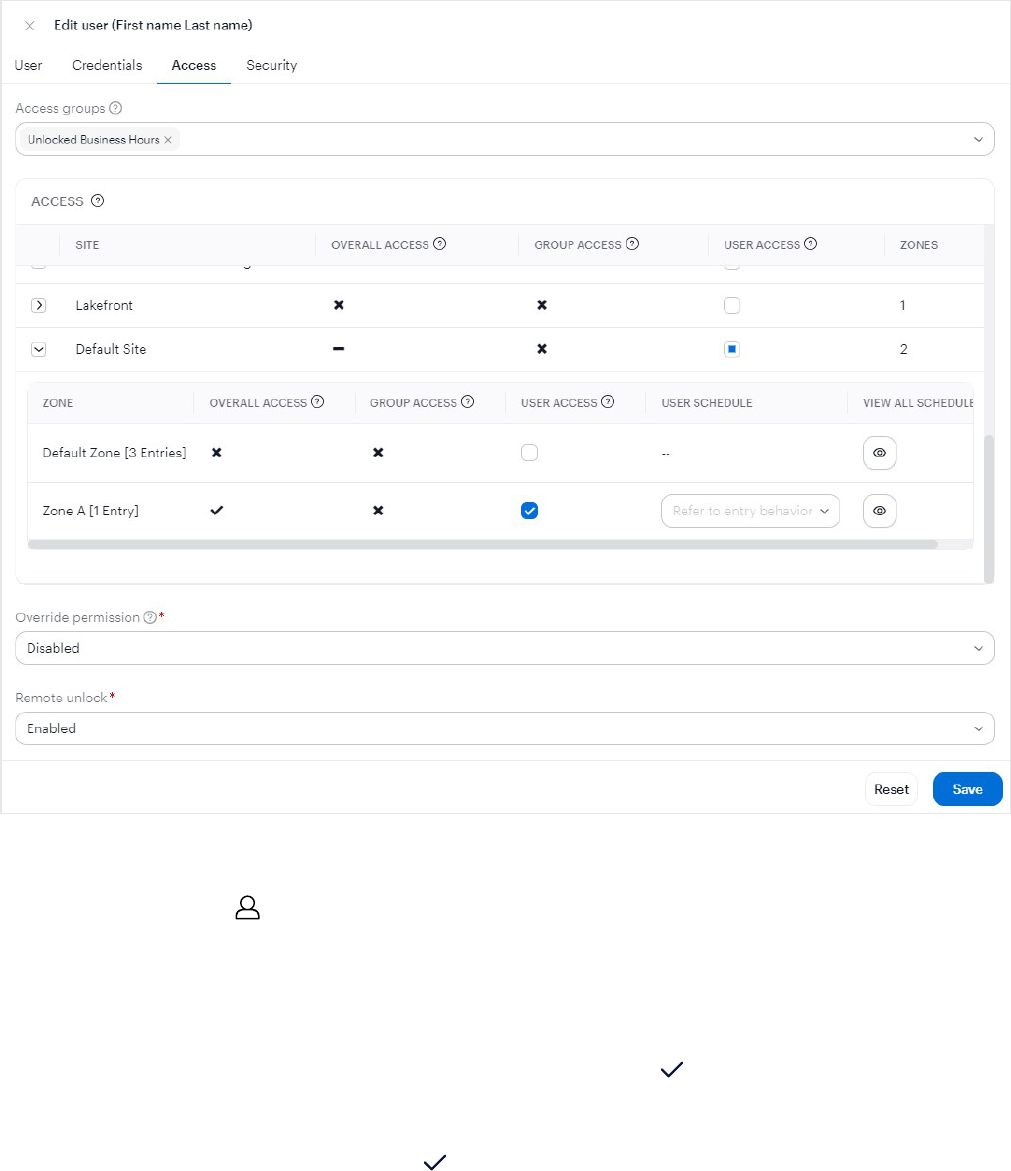
Assign access groups, sites, zones, and schedules
1.
Select a user on the page, and click the Accesstab.
2. In Access groups, add the user to one or more access groups to give them access to the zones predefined
for those groups.
If you need to add an access group, see Add access groups on page45.
3.
In the grid below, add the user to specific sites and zones by entering checkmarks.
a. In the SITE column, click a site to view the related zones.
b.
In the USER ACCESS column, click to add a user to a schedule.
c. In the USER SCHEDULE column, select a predefined user schedule.
Users 42

If you need to add a user schedule, see User schedules on page50.
d.
In the VIEW ALLSCHEDULES column, click to view all schedules that you've assigned.
4. Click Save.
Assign permission to override lockdowns
1.
Select a user on the page, and click the Accesstab.
2. Enable Override permission to give the user permission to unlock entries in the Lockdown - Override Only
state.
3. Click Save.
Assign permission to remote unlock using Avigilon Alta Open app
1.
Select a user on the page, and click the Accesstab.
2. Enable Remote unlock to let the user unlock a door remotely using the Avigilon Alta Open app.
Note: This feature is not applicable to Schlage no-tour wireless locks.
3. Click Save.
View MFA credentials
The Security tab is where you can manage Multi-Factor Authentication (MFA) credentials. You cannot add MFA
credentials for other users — only view and delete. You can add a MFA credential for yourself under User profile on
page22.
Delete users
1. Select the user on the Users page.
2.
Click the icon.
3. Click Yes. The user's access is deleted.
Note: The deleted user is kept in the system for reporting and record-keeping purposes. To find a deleted user,
go to the Users page and select Deleted from the STATUS column.
Import users by CSV file
You can import and update users by uploading a CSV file. To import users by using a directory service integration,
see App marketplace on page102.
1.
Go to Users > Import users.
Or, click the Import users button in the upper-right corner of the Users page.
Users 43
2. Create the CSV file in one of the following ways:
l
Click Download sample CSVand fill out all required fields in the supported formats. Save the file as
a CSV file (for example, mycompany-bulk-import-users.csv). Excel file extensions do not work.
l
Click the Export to CSV icon in the upper-right corner of the Users page, and modify the
downloaded file.
Tip: Refer to the Valid fields tooltip for the supported values.
3.
Click the Select CSV button and locate the file.
4. Select your Namespace:
l
Local— For adding new users or updating existing ones, and if you are not using an identity provider.
Choose to Skip existing users or Update them in the How to handle existing users field.
l
Google Workspace, Microsoft Azure AD, Okta,or OneLogin — For updating existing users you
previously synced with the Avigilon Alta system. New users will not be added.
5. Click the Upload file button.
The Upload status field will log all users added, updated, and skipped. This step may take a few minutes.
When finished, you'll see an IMPORTCOMPLETE message along with any errors.
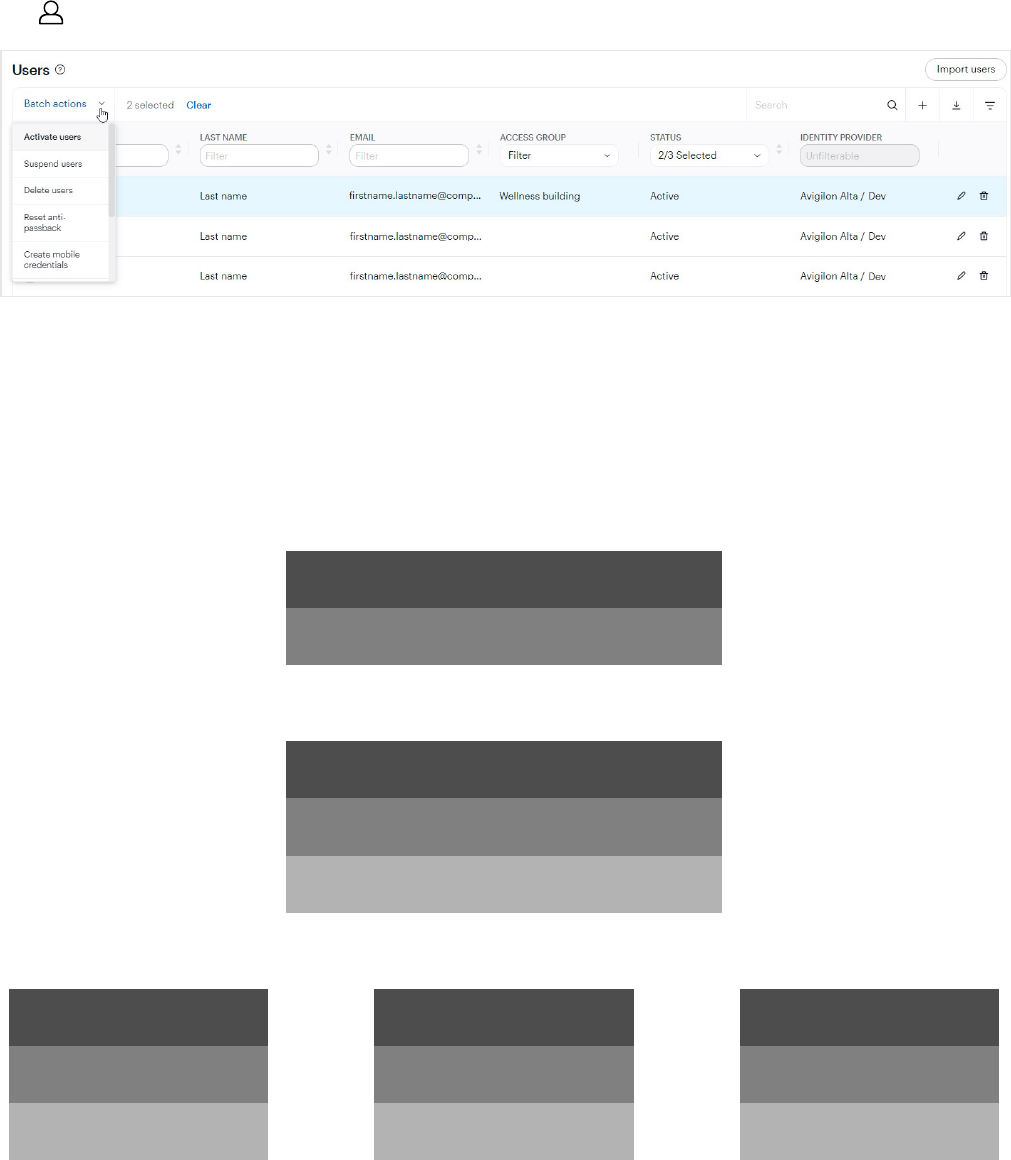
Issue batch actions to users
1.
Go to Users > Users.
2. Enter a checkmark next to one or more users.
3. In Batch actions (activated by the previous step), issue any of the following actions to the selected users:
l
Activate users — Reactivates a suspended user.
l
Suspend users — Disables credential use and admin portal access, if granted to the user.
l
Delete users — Revokes access from the user and keeps the user in the system for reporting and
record-keeping purposes.
l
Reset anti-passback — Resets the anti-passback state of a user, if using anti-passback. See Anti-
passback and occupancy management on page58.
l
Create mobile credentials — Automatically creates mobile credentials for the selected users.
Users 44

l
Send mobile credentials —Sends mobile setup emails to the selected users. If a user has multiple
mobile credentials, they'll receive multiple setup emails.
l
Disable remote unlock —Disables the remote unlock permissions for the selected users.
l
Enable remote unlock — Enables the remote unlock permissions for the selected users.
Note: This feature is not applicable to Schlage no-tour wireless locks.
Access groups management
The Access groups page is where you can create and manage groups of users. Groups let you assign access and
entry permissions for one or more users, and are useful for organizing your user base by department or role.
Add access groups
1.
Go to Users > Access groups.
2.
Click the button in the upper-right corner.
3.
Enter a name, description, badge template, and assign users using the button.
Note: The Badge template field appears only if the Badge Printing app is installed.
4. Select the sites and/or zones the access group will have access to.
Users 45
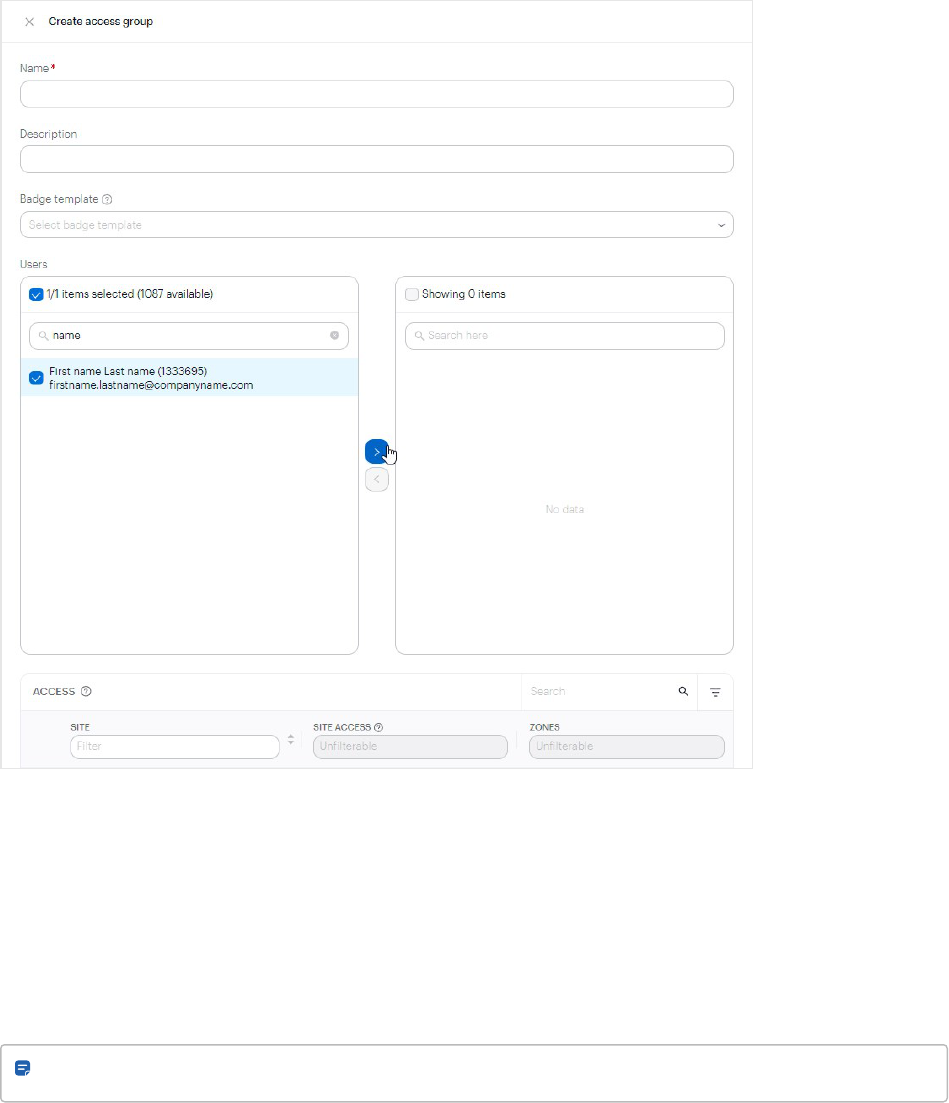
5. Click Save.
Role management
A role is a set of portal access permissions that can be assigned to users in an organization. The following default
roles cannot be edited:
l
Dashboard (Read-Only) — Gives dashboard access with read permissions.
l
Super Admin — Gives full portal access with edit permissions.
Note: Users with the Super Admin role can assign and revoke portal access for other users.
l
Super Admin Read-Only — Gives full portal access with read permissions.
l
MFA enforced Super Admin — Gives full portal access with edit permissions for users who use MFA.
Users 46

l
MFA enforced Super Admin Read-Only — Gives full portal access with read permissions for users who use
MFA.
l
Aware Default Role — Gives Alta Aware Operator users read permissions to the Activity dashboard. Users are
created automatically with this role when they are added to the Administrators group in Alta Aware. (Aware
Operator users will need to check their inbox for an invite from Alta Control Center to set up a password for
their new Control Center accounts.)
Note: If your Alta Aware and Control Center systems have been unified, the Alta Control Center
password must be used to sign in. The Alta Aware password is no longer used in both systems.
l
Device (Read-Only) — Gives device access with read permissions. If new users sign in for the first time using
the SAML Single Sign-on (SSO) app integration, they will be assigned this role. The organization's
administrator must manually update the assigned roles to expand their permissions.
If more permissions are needed, see Assign permissions to roles on the next page.
Export information to CSV
l
Click the icon.
Show, hide, or reset information
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
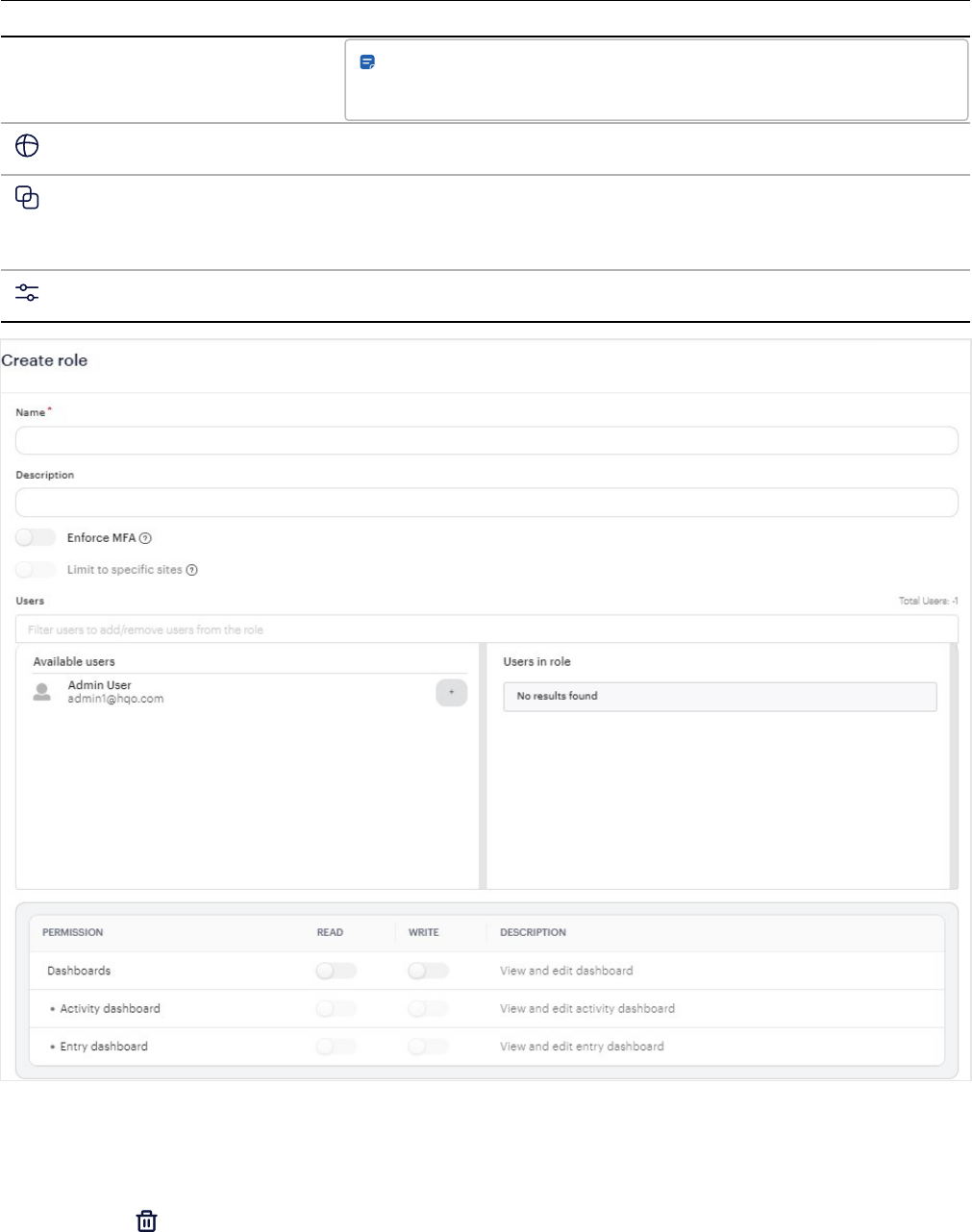
Add roles
1.
Go to Users > Roles.
2.
Click the button in the upper-right corner.
3. Enter a name, description, and assign users.
l
Enforce MFA — Require user to set up Multi-Factor Authentication at login.
l
Limit to specific sites — Specify the Sites. Requires a package upgrade. A Premium or Enterprise plan
is required.
4. Select the permissions the role will have.
Note: You cannot create a role with more permissions than you have, and you cannot assign a role with
more permissions to yourself or another admin.
You can assign multiple roles to the same user. The user's permissions will be cumulative across all
assigned roles.
5. Click Save.
Users 47
Assign permissions to roles
Permissions gives additional specificity when creating roles. For example, you create a role that limits access to just
the Entry dashboard. Or, create a role with full portal access but only for one site.
Note: You cannot limit access to the users of a specific site. If you create a role that has access to users, the
role will have access to all users within that organization.
Permissions Description
Dashboards View and edit the dashboards, Activity dashboard, Entry dashboard, and
Alarms dashboard.
Note: Access to the Devices dashboard is provided by the
Devices permission, not the Dashboards permissions.
A Premium or Enterprise plan is required to use the Alarms
dashboard.
Users View and edit users.
Roles View and edit roles, and assign roles to users.
Sites View and edit sites, buildings, entry states, general site settings, and
lockdown plans.
Note: A Premium or Enterprise plan is required.
Cameras
View live feed View live feed from linked cameras. Avigilon Pro series readers only.
Playback video clips Play back video clips from linked cameras. Avigilon Pro series readers
only.
Export video clips Export video clips for local storage.
Devices View and edit devices.
Openpath video device Adjust video settings for Avigilon (formerly Openpath) Video Reader Pro
devices.
Openpath video intercom Adjust video settings and routing for Avigilon (formerly Openpath) Video
Intercom Reader Pro devices.
Reports View and edit reports, entry access audit, portal audit report, credentials,
general report settings, alarm report, muster report, and occupancy
report.
View and download report links.
Users 48
Permissions Description
Note: A Premium or Enterprise plan is required to use the Alarm
report, Muster report, or Occupancy report.
App marketplace View and edit app marketplace.
Configurations View and edit configurations, rules, alarms, alarm actions on open
alarms, alerts, mobile app settings, and badge template printing, which is
applicable only if the only if the Badge Printing app is installed.
Administration View and edit administration, account, and the Quick start page.
Delete roles
1. Select the role with no active users on the Roles page.
2.
Click the icon.
Users 49
Note: If a user assigned to alarm monitoring is deleted, the alarms continue to be displayed in the
Alarms dashboard and report history. You will be prompted to assign another user the next time you
edit the alarm configuration.
3. Click Yes.
User schedules
The User schedules page is where you can define schedules for users and groups. User and group schedules are
useful if you want to restrict access or trigger methods for certain users and groups. For example, you can define
normal business hours for employees or require that certain users only use key cards.
Multiple schedules
You can assign multiple User or Group schedules to users or groups. Access is cumulative of the assigned
schedules. For example, if a user has a group schedule that gives access 9:00 am to 5:00 pm and a user schedule
that gives access 3:00 pm to 9:00 pm, then that user will have a combined access of 9:00 am to 9:00 pm.
Add user schedules
Note: This feature is not applicable to Schlage no-tour wireless locks.
1.
Go to Users > User schedules.
2.
Click the button in the upper-right corner.
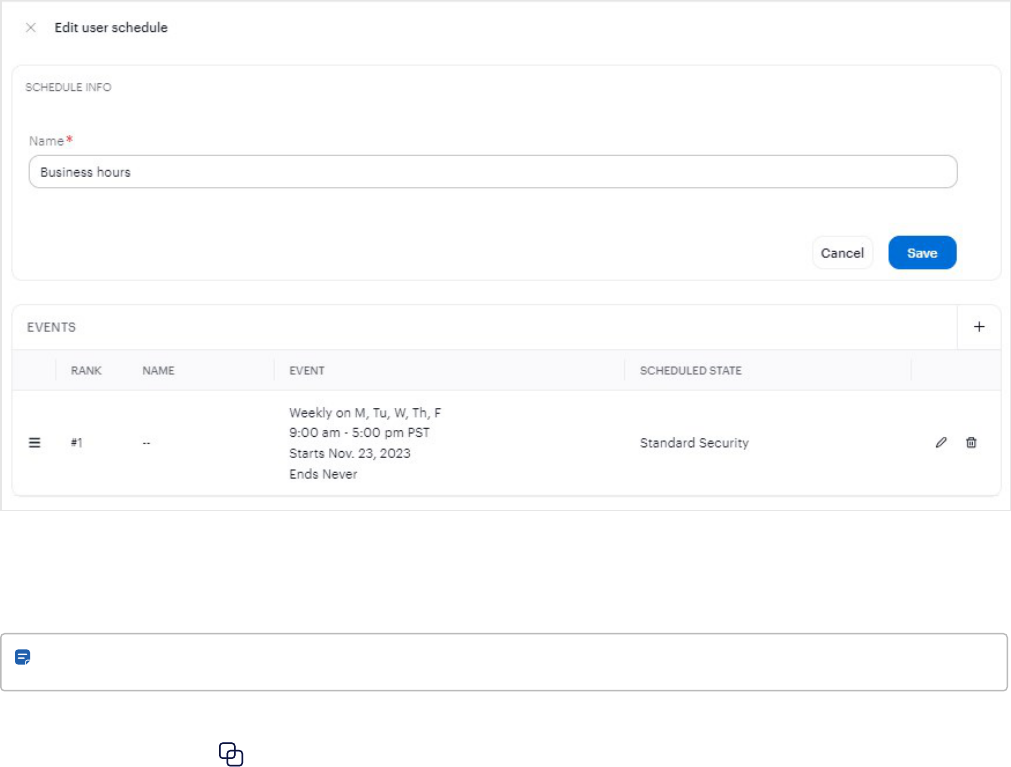
3. Enter a name for the user schedule and click Next.
4.
Click the button in the EVENTS section.
a. Choose Repeating Eventor One-time event.
b. Optional: Enter a Name.
5. For Repeating Event only:
Users 50
a. In Frequency, select Daily, Weekly, Monthly, or Annually.
b. Select the days or dates the schedule will occur on.
6. Enter a Start time and End time, and Time zone.
7. Enter a Start date and End date.
8. Select the Scheduled state. The default scheduled states are:
Note: This list depends on the entry states that are created in Sites.
l
Convenience— Allows all valid credentials and trigger methods.
l
Lockdown - Override Only — No entry allowed, even with an otherwise valid credential (overrides
allowed).
l
No Entry — No entry allowed, even with an otherwise valid credential.
l
Onsite Only — Allows all valid onsite credentials and trigger methods.
l
Standard Security— Allows most mobile access and cards supported by Avigilon readers, and
excludes remote mobile 1FA and third-party Wiegand methods.
l
Strict Security— Allows only interactive 2FA onsite mobile access and encrypted smart cards, and
excludes all remote, 1FA, and non-encrypted methods.
l
Standard Security MFA- PIN— Standard MFA - Allows most mobile access, cards, and PINs
supported by Avigilon readers, and excludes remote mobile 1FA and third-party Wiegand methods for
MFA with PIN required as the second factor.
l
Strict Security MFA - PIN — Strict MFA - Allows only interactive 2FA onsite mobile access, PINs, and
encrypted smartcards excluding all remote, 1FA, and non-encrypted methods for MFA with PIN
required as the second factor.
9. Click Save.
Note: A user schedule cannot be more permissive than what the entry allows. In the following example, the
Scheduled state is defined as Standard Security, which only works if the entry state is also set to Standard
Security or Convenience (but not say, Strict Security).
Tip: To disable remote unlock access to all users in a group, create a schedule with Onsite Only as the
Scheduled state.
Users 51
Custom fields
Note: A Premium or Enterprise plan is required.
You can create custom, optional fields to capture additional user information (shown below), and filter them on the
Users page. See also the Configurations > Mobile app or Badge templates pages.
Example:
Users 52
Create custom fields
1.
Click the button in the upper-right corner.
2. If you do not want to use the field yet, click the Enabled slider to disable .
3. Enter a Name for the field.
4. In Field type, select:
l
Checkbox for checked and unchecked states
l
Date for a calendar date picker
l
Dropdown for a list of items
l
Text for a box for typing in text
5. Click Save.
6. For a Dropdown field:
a.
Click the button in the DROPDOWN ITEMS section.
b. Enter a Name for the item and click Save.
Users 53
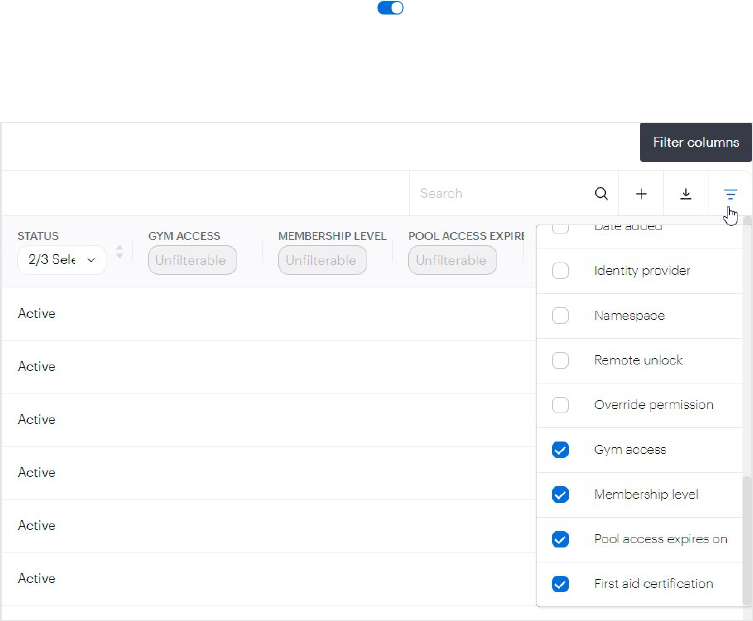
c. Repeat for the remaining items.
7. Ensure the Enabled slider is enabled .
The fields will appear in the CUSTOMFIELDS section on the user page. They can be filtered as shown below.
Example:
Users 54
Sites
Sites are physical locations, such as office buildings, comprised of zones and entries.
Site management
The Sites page lets you create a site for every location where you have an Avigilon Alta system installed.
Add sites
1.
Click the button in the upper-right corner.
2. Enter a name for the site, the physical address, and a phone number.
3. Optional. Set the language of the Alta Control Center site-wide emails in Site language.
4. Click Save.
Add zones
1. Click the site on the Sites page.
2.
Click the button in the ZONES section.
See Add zones on page57.
Building management
You can view and manage the floors and units in buildings, and assign access to users and groups, on the Buildings
page.
Sites 55

Add buildings
1.
Go to Sites > Buildings.
2.
Click the button in the upper-right corner.
3. Enter the name of the building and the site.
4. Include the address, phone number, and a description.
5. Click Save.
Add floors to buildings
1. Click the building on the Buildings page.
2. Click the Floors tab.
3.
Click the button.
4. Enter the name of the floor and a description.
5. Click Save.
Add units to floors and assign access
1. Click the building on the Buildings page.
2. Click the Units tab.
3.
Click the button.
4. Select the floor.
5. Enter the unit and a description.
6. Select the users and access groups that need access to the unit.
7. Click Save.
Zone management
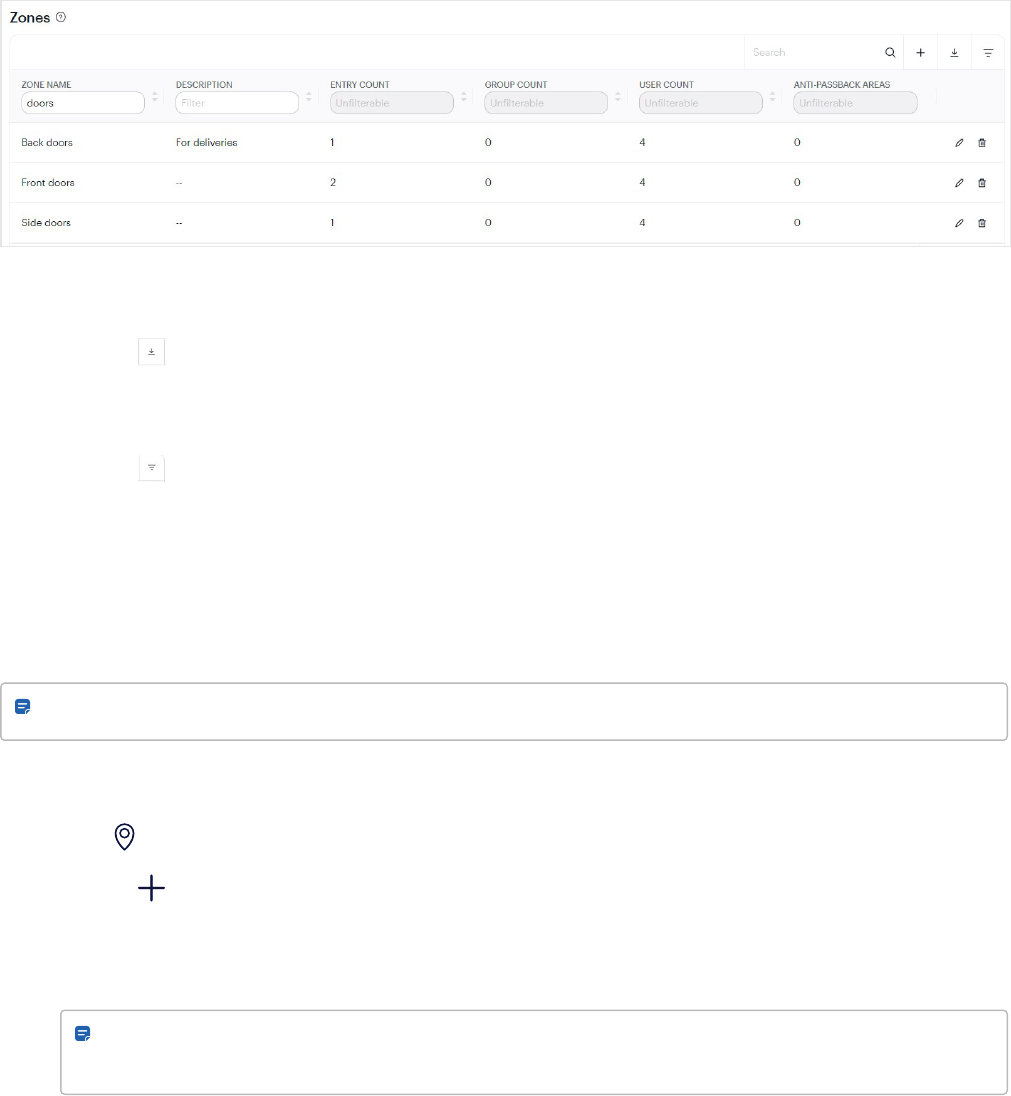
The Zones page is where you can view and manage zones. Zones are groups of one or more entries that you can
assign to sites. Zones are useful for breaking up large sites into smaller areas like floors or common areas in multi-
tenant scenarios. Most significantly, zones are the units of physical access permissions that you assign to users.
Sites 56
Export information to CSV
l
Click the icon.
Show, hide, or reset information
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
Zone sharing between customers
Zones can be shared between multiple customers. This is useful if you're a landlord who wants to share a zone of
common entries with multiple tenants. Recipients cannot edit shared zones.
Note: This feature is not applicable to Schlage no-tour wireless locks.
Add zones
1.
Go to Sites > Zones.
2.
Click the button in the upper-right corner.
3. Enter a Name and description (optional).
4. Select the Site to which the zone will be assigned.
Note: A zone can only be assigned to one site, but a site can have multiple zones assigned to it. A zone
can include a mix of Avigilon locks and Schlage wireless locks.
5. Optional. Add Access groups and Users to the zone.
6. For Schlage no-tour wireless locks only. In the Entries list, click and drag the no-tour locks installed in the
zone (left pane)to the zone list (right pane).
7. Optional. If you want to share this zone with a different organization, enter the Org IDs.
8. Click Save.
Sites 57
Anti-passback and occupancy management
Note: If you are working with Schlage no-tour wireless locks, information may be out-of-date. Anti-passback
and occupancy information is available only after visiting the no-tour wireless lock in person and completing a
manual sync using the Avigilon Alta Access app.
Anti-passback lets you define a sequence in which entries must be accessed in order to gain entry. Sequences are
defined using
areas
. Each area contains a set of inbound and outbound entries.For each area, after every successful
inbound entry, the user must exit through an outbound entry before entering an inbound entry again.
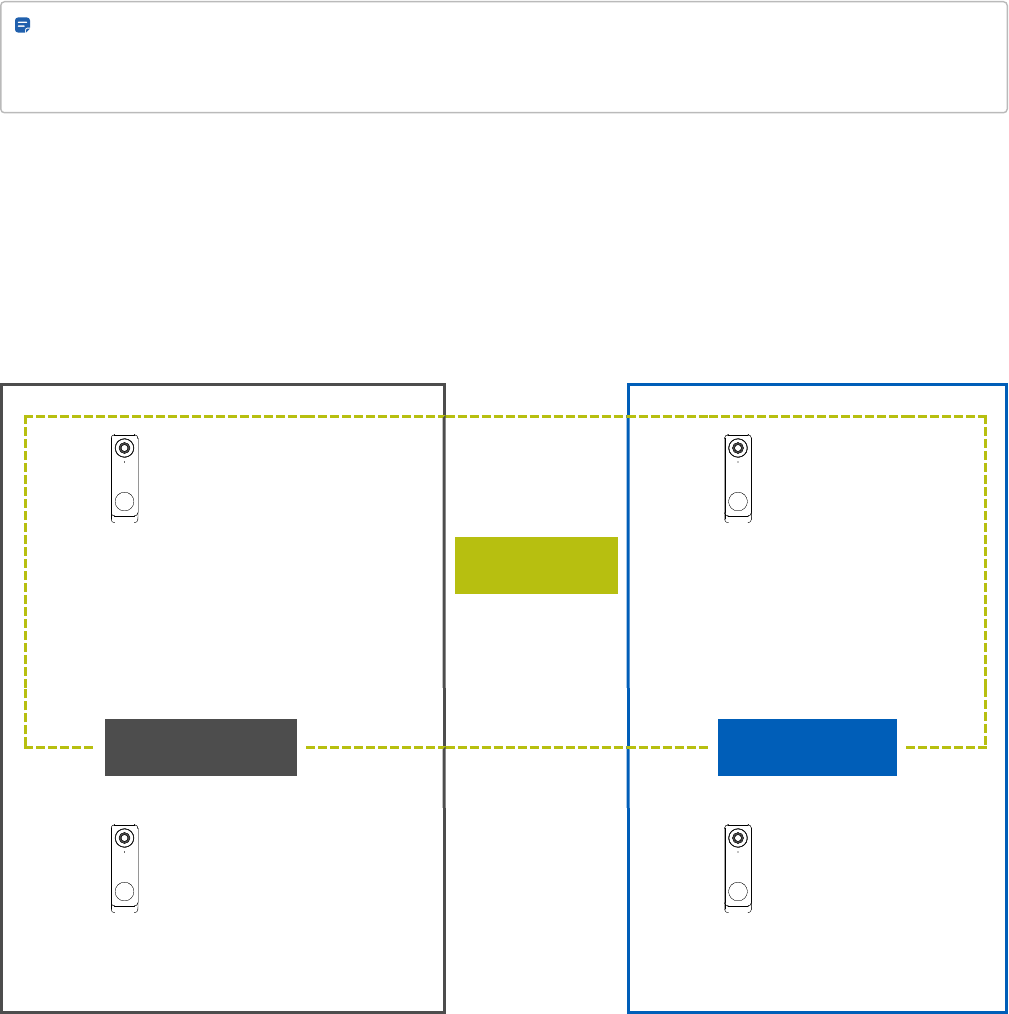
Overview of multiple area anti-passback
Most anti-passback scenarios will only require a single area, but multiple areas can be used to create multi-step
sequences of entry access. In the following example, all four readers reside on the same ACU and are configured
across three areas.
Û
Inbound Area 2
Reader 2
OutboundArea1
Reader 2
Ú
Area2
Ú
OutboundArea2
Reader 3
Inbound Area 3
Reader 3
Ü
Area 1 Area 3
Û
Inbound area1
Reader 1
(J
Entry Anti-
Passback
Breach)
Outboundarea3
Reader 4
Ü
Figure 1 Anti-passback logic
The ACU tracks each user's most recent direction of movement (inbound or outbound) within each area. When the
user's most recent direction is known, any attempt by that user to move in the same direction again will result in an
Entry Anti-Passback Breach event (see the J example in the above figure).
When the user's most recent direction is unknown, as in the case of a newly created area, or following a scheduled or
manual reset action, the user's next movement will be allowed in either direction, after which normal rules will apply
again.
Sites 58

Configure Entry Anti-Passback Breach event
Entry Anti-Passback Breach events can trigger alerts. See Alerts by email or SMS on page129. They can also be
used to trigger custom integrations. See Rules on page126.
Note: Anti-passback logic also applies to Cloud Key credentials and other remote unlock methods. In general,
you might not want to allow remote unlock methods on zones with anti-passback enabled.
Set up anti-passback and occupancy limit
To set up anti-passback and occupancy limit in a zone:
1. Select the zone and click the Anti-passback tab.
2. Enable any of the following settings:
l
Expiration time — Time in seconds after which the anti-passback state will reset for the user.
l
Reset Anti-passback Periodically — A schedule during which a user is not limited to anti-passback
logic, until after their second unlock attempt.
a. Enter a Reset Time and Time zone.
b. Select the days or dates the schedule will occur on.
l
Use contact sensor — Changes a user's anti-passback state after the contact sensor reports open.
l
Shared-To Orgs Can Reset Anti-passback — Gives your organizations that sharethis zone the
permission to reset anti-passback for their users.
3. Define the area within the zone to be enforced by anti-passback and an occupancy limit.
a. Click Add area and enter a Name.
b. Set the Inbound modeand Outbound mode to configure the system response to anti-passback
breaches:
l
None— Access is granted; no additional response.
l
Alert— Access is granted and an event is generated.
l
Enforce— Access is denied and an event is generated.
c. Add your entries in Inbound entries and Outbound entries.
Note: An entry can only be used once within an area, either as inbound or outbound but not both.
However an entry canbe used in multiple areas. In addition, all entries within an area must
reside on the same ACU, and all entries belonging to the parent zone must reside on the same
ACU.
d. Optional. In Occupancy limiting mode, select Alertor Enforce. Enter the number in Occupancy limit.
e. Click Add area to save. The area is added to the zone.
Sites 59
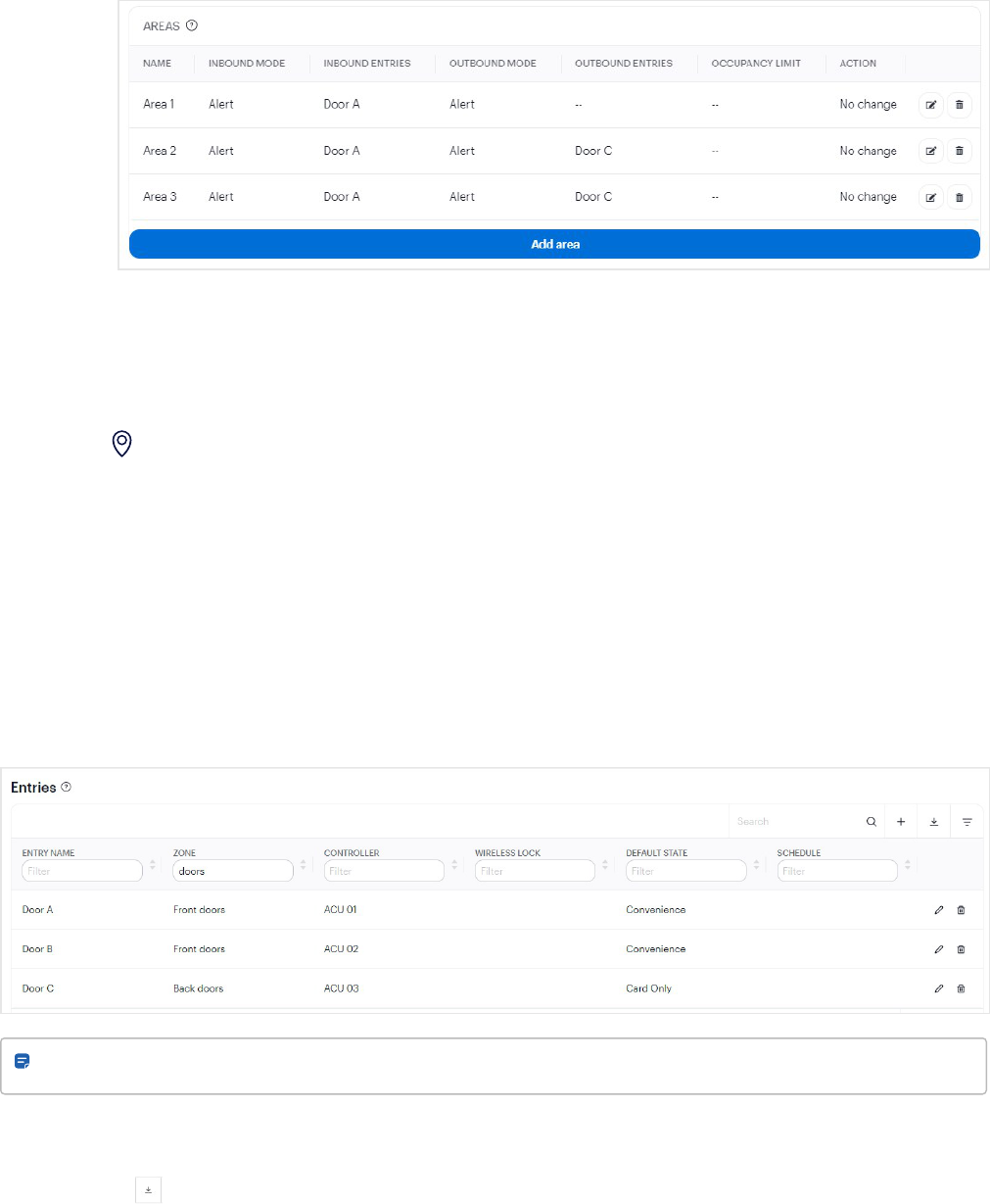
f. Optional. Repeat the above steps to add more areas to the zone.
4. Click Save.
Reset anti-passback on zones and users
To reset anti-passback at the zone level:
1.
Go to Sites > Zones.
2. Click Reset anti-passback in the ANTI-PASSBACK AREAS column.
3. Click Yes.
To reset anti-passback on a user or multiple users, see Issue batch actions to users on page44.
Entry management
The Entries page is where you can add and manage entries. Generally speaking, entries are doors, but can also be
gates, turnstiles, and elevator floors. An entry is often secured with a reader or wireless lock.
Note: Your installer may provision some or all of the following features for you during the installation process.
Export information to CSV
l
Click the icon.
Sites 60

Show, hide, or reset information
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
Add entries
1.
Go to Sites > Entries.
2.
Click the button in the upper-right corner.
3. Enter a name and select the zone.
4. In Cloud gateway device type, select the hardware that is configured at the entry.
l
Openpath hardware
o
Select the ACU in Controller.
o
Select the video reader or video intercom reader in Controller.
l
Schlage for Allegion Schlage hardware
o
Select the lock in Schlage wireless lock.
Note: The Entry Open Duration and Entry state settings are not applicable to no-tour wireless
locks.
5. Optional. Select the Muster point toggle to designate the entry as a safe area, where personnel should gather
in an emergency situation.
Note: A credential reader is required to be installed at the entry. The reader should only be used in a
muster event and not for any other purpose. For more information, see Muster Reports workflow on
page16.
If you are working with Schlage no-tour wireless locks, information may be out-of-date. Mustering
information is available only after visiting the no-tour wireless lock in person and completing a manual
sync using the Avigilon Alta Access app.
6. Click Save.
Edit entries
After saving a new entry, you can configure these settings depending on the installed device.
Sites 61

Set default state and schedule for the entry
1. In ENTRY BEHAVIOR, you can set the default state for the entry.
Note: Entries installed with gateway-connected Allegion Schlage NDEB and LEB wireless locks only
support Unlocked, No Entry, and Convenience entry states. Entry states are not supported by Schlage
Control locks and no-tour connected NDEB and LEB series wireless locks.
l
Convenience— Allows all valid credentials and trigger methods.
l
Lockdown - Override Only — No entry allowed, even with an otherwise valid credential (overrides
allowed).
l
No Entry — No entry allowed, even with an otherwise valid credential.
l
Onsite Only — Allows all valid onsite credentials and trigger methods.
l
Standard Security— Allows most mobile access and cards supported by Avigilon readers, and
excludes remote mobile 1FA and third-party Wiegand methods.
l
Standard Security MFA- PIN— Standard MFA - Allows most mobile access, cards, and PINs
supported by Avigilon readers, and excludes remote mobile 1FA and third-party Wiegand methods for
MFA with PIN required as the second factor.
l
Strict Security— Allows only interactive 2FA onsite mobile access and encrypted smart cards, and
excludes all remote, 1FA, and non-encrypted methods.
l
Strict Security MFA - PIN — Strict MFA - Allows only interactive 2FA onsite mobile access, PINs, and
encrypted smartcards excluding all remote, 1FA, and non-encrypted methods for MFA with PIN
required as the second factor.
2. Optional. Assign a schedule.
If you need to create a new schedule, click Manage schedules. See Entry schedules on page67.
Schlage wireless lock (gateway connected) settings
l
For NDEB and LEB only. In SCHLAGE WIRELESS LOCK, Ajar Detection and Forced-open detection are always
enabled for wireless locks.
If needed, edit the duration in Ajar Duration (255 Sec Max), and specify seconds or minutes in Unit.
l
In Entry Open Duration, edit how long the entry will remain unlocked (maximum is 30 seconds).
l
For NDEB and LEB only. Card Reader Sensitivity is set to Normal by default, but you can select High or Max
for more reliable reading of key fobs.
Contact sensor settings
In CONTACT SENSOR, you can specify the port to which the entry is wired and related settings.
Sites 62

l
Port— The port for the contact sensor. A contact sensor detects if an entry is open.
l
Ajar feature — If enabled, the maximum time the door can be ajar before an event is generated indicating the
door is ajar. Edit the maximum allowed time the door can be ajar before events are generated in Ajar duration
(15 min max).
If disabled, no system action occurs if the door is ajar.
l
Forced-open detection — If enabled, an entry opening without first unlocking through the Openpath device
(specified in Cloud gateway device type) or triggering the REX, will generate an event.
To monitor the entry, you can set up contact sensor events that can trigger alerts. See Alerts by email or SMS on
page129 and Rules on page126 for triggering custom integrations.
Entry and exit hardware settings
In ENTRY/EXIT DEVICES, you can specify the relay port on the ACU or expansion board to be used for controlling
electric strikes or maglocks, and related settings.
l
Port — The Relay 1, Relay 2, Relay 3, or Relay 4 port to assign the Avigilon reader. When installed, the electric
strike is wired to one of the four ACU ports, and the reader is wired to the strike. You will need to select the
ACU relay for which this reader/entry is wired to the ACU.
l
Entry open duration (10 min max) — The maximum time the entry can remain unlocked before reverting back
to its default state. Supported range is 1 second and 10 minutes. Specify seconds or minutes in Unit.
l
Invert output — An advanced setting for elevator relays. If enabled, the NC/NO configuration of the physical
relay is flipped.
Openpath reader settings
In OPENPATH READER, you can assign the entry to the Avigilon (formerly Openpath) reader and related settings.
l
Port— The port on the ACU to which the reader is connected.
l
Card reading — If enabled, allows RFID/NFC cards at this reader.
l
Wave to unlock — If enabled, allows the Wave to Unlock and Touch Entry functionality.
o
Mobile authorization range — The distance between the mobile device and the Avigilon reader in order
to register a Wave to Unlock attempt. Set the Near to Far range using the slider.
o
Wave detection range — The distance between the hand and the Avigilon reader to initiate the unlock
attempt. Set the Near to Far range using the slider.
Note: This setting may vary depending on your environment and require adjustments.
l
Auto proximity unlock (Elevators only) — If enabled, unlocks the entry when a user with a valid mobile
credential is within range of the reader.
o
Mobile authorization/Trigger range — The distance between the user's mobile device and the reader
to initiate an unlock attempt.
l
Advanced options
Sites 63

o
For the Avigilon reader:
Mobile communication range — The distance that the reader can detect a mobile phone that is in BLE
range.
Mobile beacon range —The distance that the beacon can detect a mobile phone and 'wakes up' the
Avigilon Alta Open app installed on the phone.
o
For the Avigilon keypad reader:
Key press audible feedback —If enabled, audible feedback upon key press.
Key press LED feedback —If enabled, LED feedback upon key press.
Allowed time interval for completion of 1FA PIN entry (Max 20 seconds) —Adjust the time interval,
as needed.
Request to exit (REX) settings
Often, doors will have a REX button or sensor that will unlock the door from the inside.
l
Port— The port for the REX device to which the entry is wired.
l
Mode— The Normally closed or Normally open mode of the REX device that sends commands to the ACU.
Note: Contact your electrical installer for the required mode for your entry configuration.
l
Trigger relay to unlock entry — If enabled, a triggered REX will open the associated relays and prevent forced-
open alarms.
Wiegand device settings
The Avigilon Alta system is compatible with legacy Wiegand devices.
l
Port— The port for the Wiegand device to which this entry is wired.
l
Mode— The direction the card credential data is sent.
o
Input— Receives data from the Wiegand reader.
o
Output (gateway) — Sends credential data to a third-party control panel.
Enable Gateway credential pass-through if you do not want the Avigilon Alta system to authenticate
credentials, but rather send all data to the legacy panel for authentication.
Enter a Default gateway card number so that all credentials (including mobile credentials) are sent to
the legacy panel as a Wiegand ID.
Additional device (control) settings
l
If your entry is configured with more than one of the above devices, select it from Control and click Add
control. The additional device appears below the first device.
Sites 64
l
To remove the additional device, click .
Entry states
An entry state defines whether an entry is unlocked and what access methods may be used to unlock it. Avigilon Alta
Control Center provides the following default entry states:
l
Unlocked— No credential is required for access.
l
No Entry — No entry allowed, even with an otherwise valid credential.
l
Lockdown - Override Only — No entry allowed, even with an otherwise valid credential (overrides allowed).
l
Convenience— Allows all valid credentials and trigger methods.
l
Onsite Only — Allows all valid onsite credentials and trigger methods.
l
Standard Security— Allows most mobile access and cards supported by Avigilon readers, and excludes
remote mobile 1FA and third-party Wiegand methods.
l
Strict Security— Allows only interactive 2FA onsite mobile access and encrypted smart cards, and excludes
all remote, 1FA, and non-encrypted methods.
l
Standard Security MFA- PIN— Standard MFA - Allows most mobile access, cards, and PINs supported by
Avigilon readers, and excludes remote mobile 1FA and third-party Wiegand methods for MFA with PIN
required as the second factor.
l
Strict Security MFA - PIN — Strict MFA - Allows only interactive 2FA onsite mobile access, PINs, and
encrypted smartcards excluding all remote, 1FA, and non-encrypted methods for MFA with PIN required as
the second factor.
View trigger methods in entry states
The TRIGGER METHODS column refers to the number of ways that an entry can be unlocked in that particular state.
l
Click an entry state in order to view the trigger methods included in that state.
Sites 65

Add entry states
1.
Go to Sites > Entry states.
2.
Click the button in the upper-right corner.
3. Enter the name for the entry state and a description.
4. Optional. If the entry requires two credentials from each user:
a. Click the Enable multi-factor slider.
b. Enter the trigger methods in Factor 1 and Factor 2.
c. In Multi-factor interval (5-30 seconds), specify the interval between the trigger methods.
5. In TRIGGER METHODS, use the Mobile, Card, PIN, Cloud key, Mobile override, Card override, and Cloud key
override checkboxes to enable the trigger methods for the entry state.
Tip: Refer to the Definitions tooltip for the various methods.
6. Click Save.
Trigger method definitions
l
Mobile 1FA — An unlock request that is triggered either from a mobile device that has no homescreen PIN-
code, biometric, or other similar protection, or from a device whose homescreen is currently not unlocked.
l
Mobile 2FA — An unlock request that is triggered from a device with PIN-code, biometric, or other similar
protection on the homescreen, and whose homescreen is currently unlocked. Therefore in order to trigger a
Mobile 2FA unlock, a person must both be in possession of the mobile device, as well as know or possess the
PIN-code or biometric needed to unlock the device.
l
Wave — An unlock request that is triggered by passing a hand in close proximity to a Wave-enabled Avigilon
Smart Reader, and which is authenticated by the mobile credential provisioned into the Wave-enabled
Avigilon Alta Open app.
l
Auto — An unlock request that is triggered by being in close proximity to an Auto-enabled Avigilon Smart
Reader, and which is authenticated by the mobile credential provisioned into the Auto-enabled Avigilon Alta
Open app. This mode is often used for elevator scenarios.
l
Remote — An unlock request that is triggered while the user is not near the entry.
l
Onsite— Opposite of Remote; an unlock request that is triggered while the user is near the entry.
l
Near reader — An unlock request that is considered Onsite because the mobile device is within close range of
the entry's Avigilon reader.
l
Over BLE — A mobile unlock request that is sent over BLE through the Avigilon Reader. Such a request is
always Onsite.
Sites 66
l
Over WiFi — A mobile unlock request that is sent over the mobile device's WiFi connection over the local
network directly to the Avigilon Access Control Unit. Such a request may be considered Onsite or Remote
depending on whether the mobile device is in range of the entry's Avigilon reader.
l
Over cloud — A mobile unlock request that is sent over the mobile device's WiFi or cell/LTE connection, and
routed via the Avigilon Alta cloud back to the Access Control Unit. Such a request, if permitted, enables
Remote unlock from anywhere in the world where the mobile device has an internet connection, but also may
be considered Onsite if the mobile device is in range of the entry's Avigilon reader.
l
Geofence — A mobile unlock or override request that is sent within the virtual geographic boundary of the
Avigilon reader and uses the location-based service on the Avigilon Alta Open app over a Cloud, WiFi, or BLE
connection.
l
Multi-Factor — An unlock request that requires two different credential types from a single user (such as card
and PIN). When enabled, users with permissions at the entry must present both credentials using the
approved trigger methods for each type to gain access.
Entry schedules
Entry schedules allow for entries to be in a specific state, such as locked and unlocked, based on date and time.For
example, an entry can be set to an unlocked state during normal business hours, Monday to Friday, but remain
locked (its default entry state) when the schedule is inactive.
Important: If no entry schedules are assigned to an entry, the entry is unlocked at all times.
Note: Devices that do not support real-time communication with a gateway will not support this feature.
Offline devices include Schlage no-tour connected wireless locks.
Add entry schedules
1.
Go to Sites > Entry schedules.
2.
Click the button in the upper-right corner.
3. Enter a name for the schedule and click Next.
4. In Entries, assign the entry schedule to entries by typing in the entry names or selecting from the list.
5.
Click the button in the EVENTS section.
a. Choose Repeating Eventor One-time event.
b. Optional: Enter a Name.
6. For Repeating Event only:
a. In Frequency, select Daily, Weekly, Monthly, or Annually.
b. Select the days or dates the schedule will occur on.
Sites 67
7. Enter a Start time and End time, and Time zone.
8. Enter a Start date and End date.
9. Select the Scheduled state. The default scheduled states are:
Note: This list depends on the entry states that are created in Sites.
l
Convenience— Allows all valid credentials and trigger methods.
l
Lockdown - Override Only — No entry allowed, even with an otherwise valid credential (overrides
allowed).
l
No Entry — No entry allowed, even with an otherwise valid credential.
l
Onsite Only — Allows all valid onsite credentials and trigger methods.
l
Standard Security— Allows most mobile access and cards supported by Avigilon readers, and
excludes remote mobile 1FA and third-party Wiegand methods.
l
Strict Security— Allows only interactive 2FA onsite mobile access and encrypted smart cards, and
excludes all remote, 1FA, and non-encrypted methods.
l
Standard Security MFA- PIN— Standard MFA - Allows most mobile access, cards, and PINs
supported by Avigilon readers, and excludes remote mobile 1FA and third-party Wiegand methods for
MFA with PIN required as the second factor.
l
Strict Security MFA - PIN — Strict MFA - Allows only interactive 2FA onsite mobile access, PINs, and
encrypted smartcards excluding all remote, 1FA, and non-encrypted methods for MFA with PIN
required as the second factor.
10. Optional:Enable Trigger after an unlock method included in and set the scheduled state.
If enabled, the entry will not change to the scheduled state until the first person with access triggers a door to
unlock.
11. Click Save.
Add holiday schedules
1.
Go to Sites > Entry schedules.
2. Create an entry schedule or edit an existing one.
3.
Click the button in the EVENTS section.
a. Choose Repeating Event.
b. Optional. Enter a Name. Example: Thanksgiving.
c. In Frequency, select Annually.
Sites 68
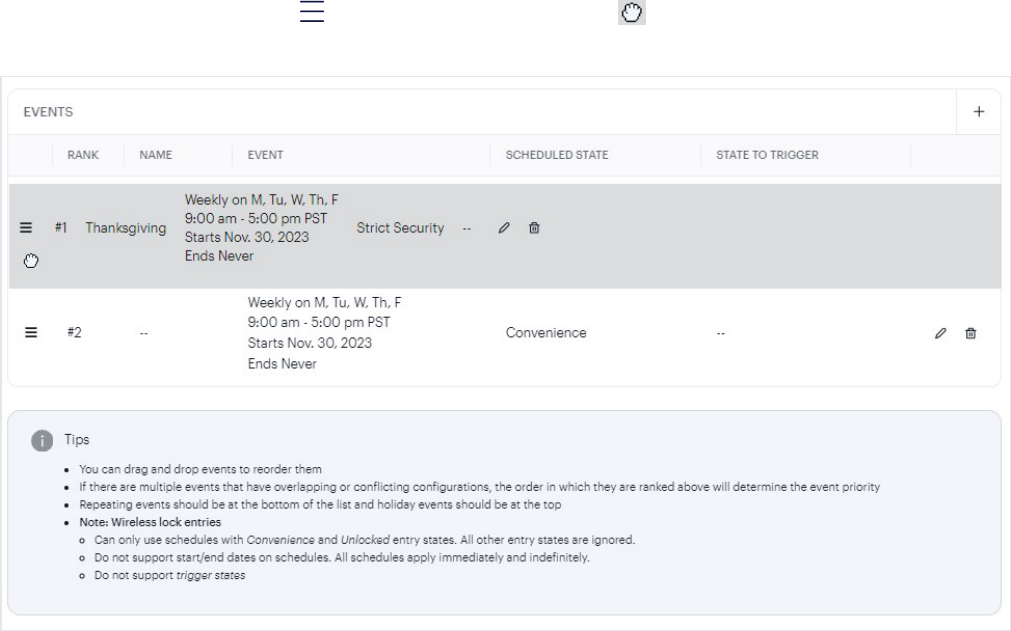
d. Select the day the schedule will occur on. Example: On the Fourth Thursday.
e. Enter a Start time and End time, and Time zone.
Example: For a 24-hour schedule, enter 12:00 am for the start time and 11:59 pm for the end time.
f. Enter a Start date and optional End date. The default is Never ends.
g. In Scheduled state, select an option.
h. Optional:Enable and set the state Trigger after an unlock method included in.
If enabled, the entry will not change to the scheduled state until the first person with access triggers a
door to unlock.
i. Click Save.
4.
Hover your mouse over the icon in the EVENTS list and drag ( ) to reorder your holiday entry event. The
holiday should rank higher than your usual schedule.
Lockdown plans (Premium and Enterprise plans)
The Lockdown plans page is where you can view and manage lockdown plans that are applied at the zone level in an
emergency situation, including specifying a ranking of the possible scenarios, the triggered entry state, and all the
users and groups that may trigger a lockdown when the situation arises and revert the lockdown when the
emergency situation is resolved.
Sites 69
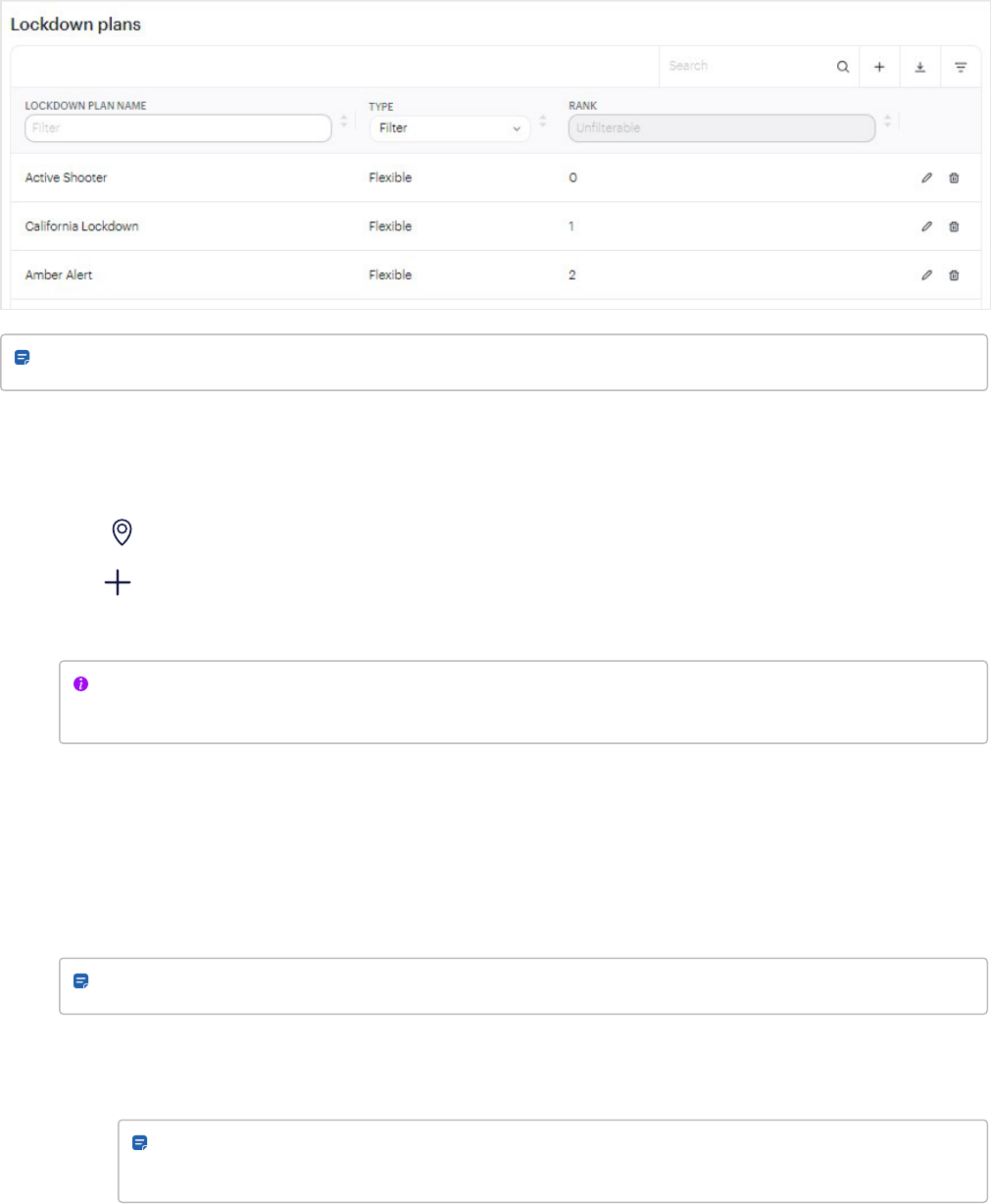
Note: Lockdown is supported only for locks that are connected to an ACU or gateway.
After adding a lockdown plan, see Triggering lockdown plans on page20.
Add lockdown plans
1.
Go to Sites > Lockdown plans.
2.
Click in the upper-right corner.
3. Enter the name of the lockdown plan and a Rank, the lower the number, the higher the rank.
Important: The rank determines the lockdown plan that takes priority when multiple lockdown plans
share entries. When assigning a rank, ensure the number is not already used.
4. Optional. In Duration, enter a time in minutes or hours after which the plan will auto-revert.
If you do not want the lockdown plan to revert automatically, leave this value blank.
5. Optional. The Use standard zone configuration setting is enabled by default to create a lockdown plan that
automatically includes all zones with the Lockdown - Override Only trigger state.
6. Select the zones that the lockdown plan will impact.
Note: You cannot add the zones that have been shared with you to a lockdown plan.
a. Click Add zone and the zone name.
b. In TRIGGERED STATE , select the entry state that will be triggered.
Note: We recommend using the Lockdown - Override Only entry state. This means only users
with override permissions can unlock entries in this state.
c. Repeat the above steps, as needed.
Sites 70

7. Click Save.
The User config tab is displayed. See Assign users and group permissions for lockdown plans below.
Assign users and group permissions for lockdown plans
1. On the User config tab, select the users and groups that can trigger and revert the lockdown plan.
Note: Enable Override permission to give the user permission to unlock entries in the Lockdown -
Override Only state. See Assign permission to override lockdowns on page43.
2. Click Save.
Sites 71
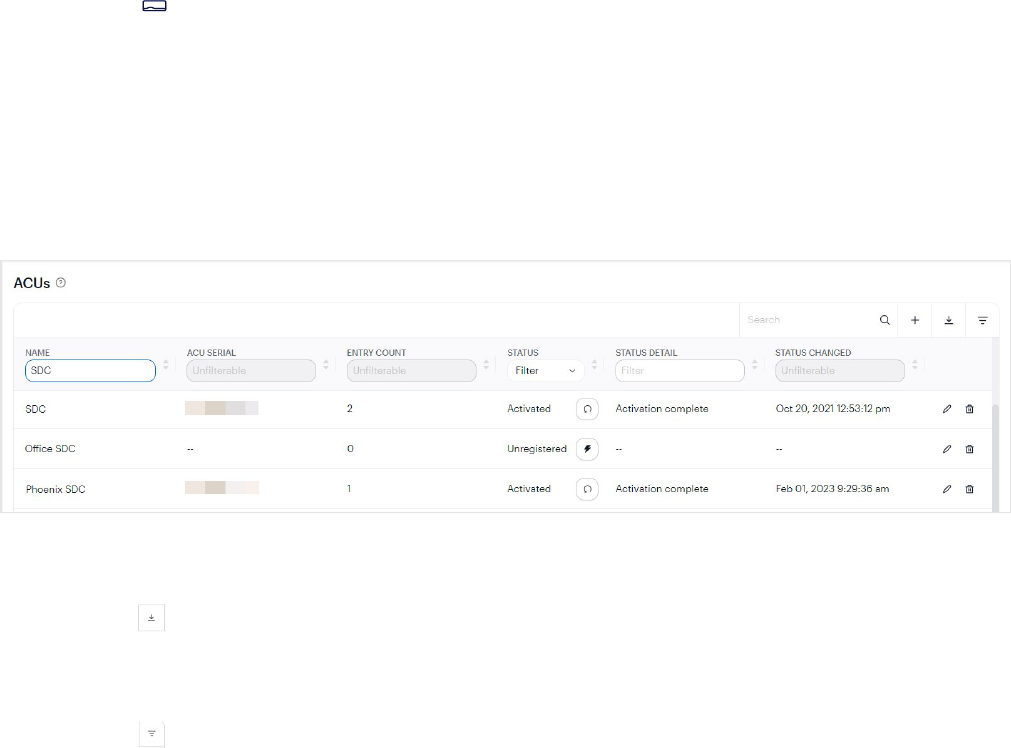
Devices
You can use the Devices page to create and manage Avigilon hardware, including access control units (ACUs),
Single Door Controllers (SDCs), readers, wireless locks, wireless lock gateways, video readers, video intercom
readers, and more.
ACU management
The ACUs page is where you can view and manage controllers including ACUs and Single Door Controllers (SDC
example is shown below).
Export information to CSV
l
Click the icon.
Show, hide, or reset information
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
Devices 72
Add ACUs or SDCs
Before you can provision an ACU using the Avigilon Alta Access app, you must first create an ACU or SDC in the Alta
Control Center.
Add multiple ACUs or SDCs using Quick start option
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to Administration > Quick start.
3. Enter a Site nameand any other relevant site information.
a. In Site language, select the preferred language for the site-wide emails sent by the system.
b. Click Next.
4. Enter the number of controllers located at your site and:
a. Enter names for the controllers.
b. In Controller type, select the type used:
l
First generation - Red Board (OP-AS-01)— For first generation Smart Hubs.
l
Single Door Controller (SDC)
l
Core series ACU — For Core Series Smart Hubs.
c. If your ACU or SDC also connects to an expansion board, add the appropriate types in EXPANSION
BOARDS:
l
Openpath 16-Port Elevator
l
Openpath 4-Port Expansion
l
Openpath 8-Port Expansion
Tip: This configuration is most common with the Core Series Smart Hub.
5. Enter the number of readers connected to the controllers. Enter their names and click Next.
6. Review your site details and click Confirm & submit. It may take a few minutes for setup to complete.
Add one ACU or SDC
1.
Go to Devices > ACUs.
2.
To add a new ACU or SDC, click the button in the upper-right corner.
3. Enter a unique name for the ACU or SDC.
4. In Controller type, select the type used:
Devices 73
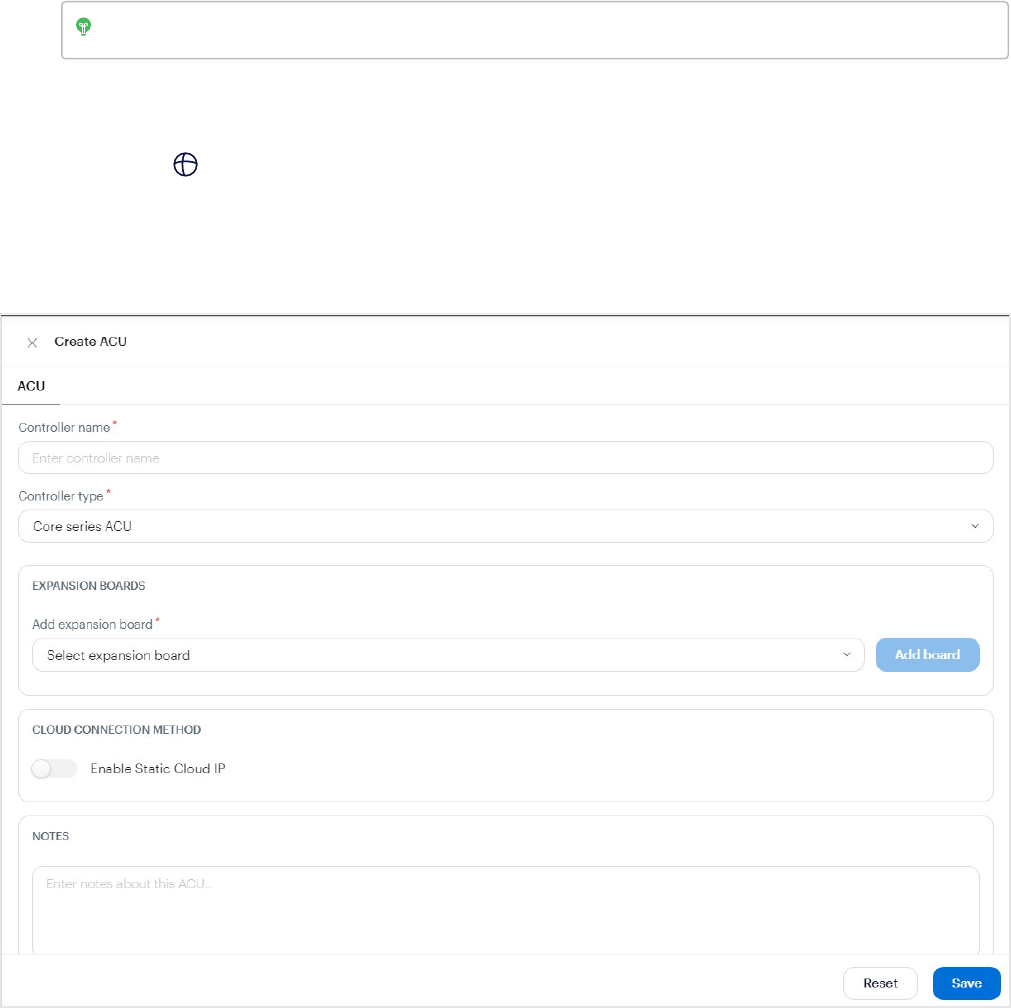
l
First generation - Red Board (OP-AS-01)— For first generation Smart Hubs.
l
Single Door Controller (SDC)
l
Core series ACU — For Core Series Smart Hubs.
5. If your ACU or SDC also connects to an expansion board, add the appropriate types in EXPANSION BOARDS:
l
Openpath 16-Port Elevator
l
Openpath 4-Port Expansion
l
Openpath 8-Port Expansion
Tip: This configuration is most common with the Core Series Smart Hub.
6. Optional. To connect your network to the Cloud using a static IP address and port on an allowlist, select the
Enable Static Cloud IP toggle. Default port is 443. An Enterprise plan is required to use Static Cloud IP.
a.
Go to App marketplace and ensure the Static Cloud IP app is installed.
b. After the toggle is enabled in the Alta Control Center, open the Avigilon Alta Access app and select
Provision with Static Cloud IP to provision the devices.
7. Click Save.
Devices 74
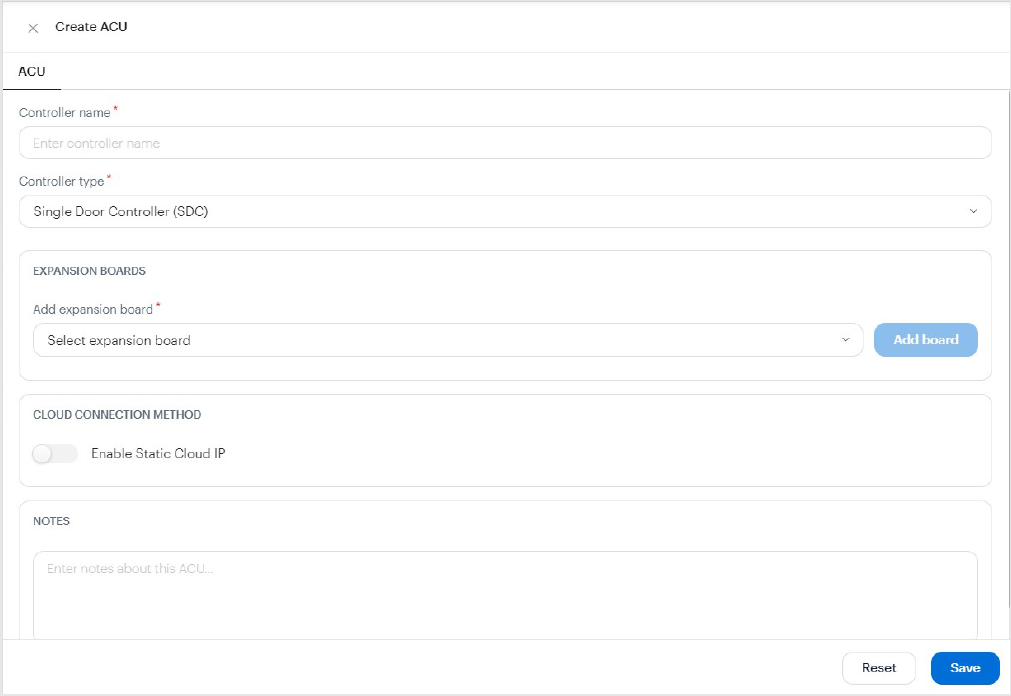
Add expansion boards
You need to edit ACUs when you install additional expansion boards in existing Smart Hubs.
1. To edit an ACU, click on the ACU from the ACUs page.
2. From Add expansion board, select and add the expansion board.
3. Click Save.
Edit ACU ports
From the Edit ACU page, click the Ports tab to view and manage ACU ports.
Devices 75
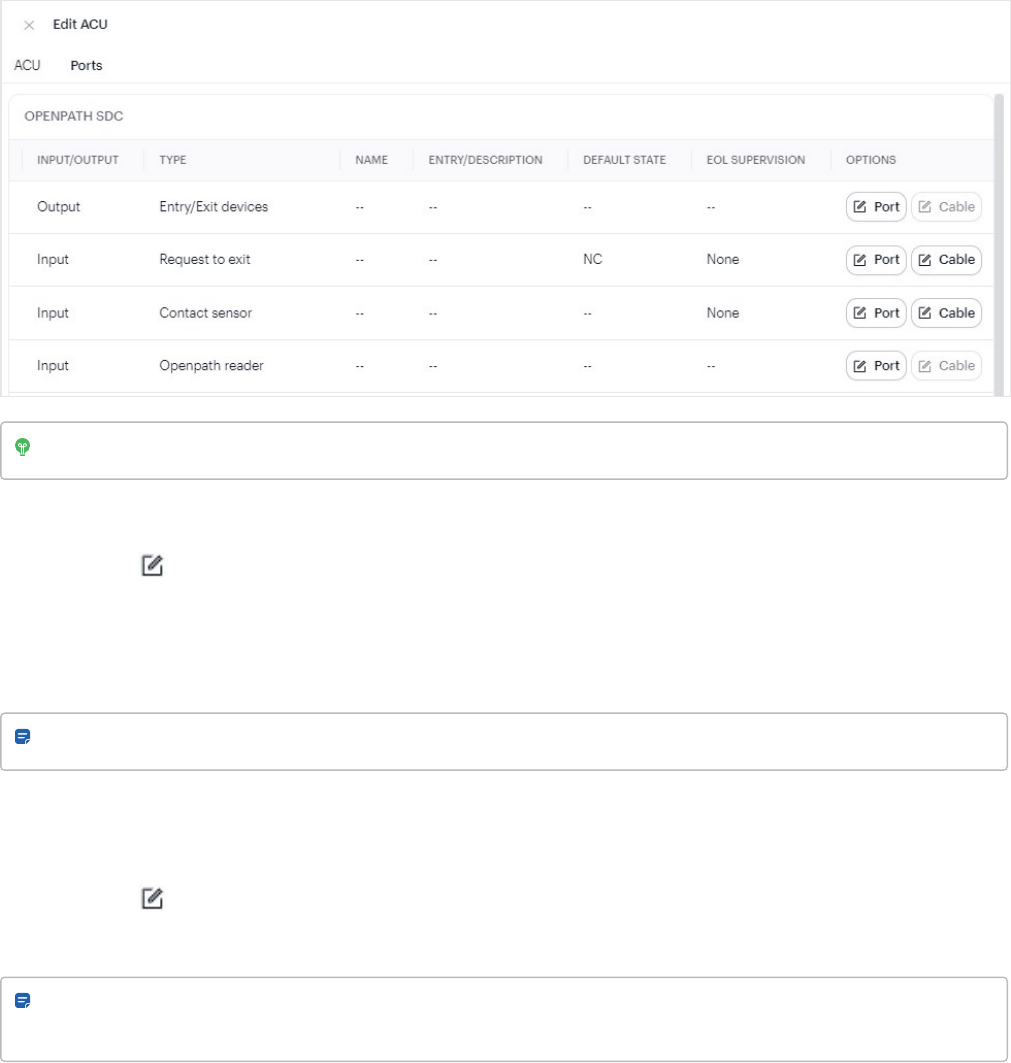
Tip: Scroll down and then scroll right to view the OPTIONS column.
Input type
1.
Click the Port icon.
2. Click Input type to change a Contact sensor, Openpath reader, Request to exit device, Wiegand device, or
Generic input to a different input type.
This can be used for creating rules. See Rules on page126.
Note: The input type on a port can only be changed if the port has not been assigned to an entry.
End-of-line supervision
The Single Door Controller and Core Series Smart Hub support end-of-line (EOL) supervision:
1.
Click the Cable icon.
2. Click End of line supervision to select Both, Cut Line Detect, Line Shorted Detect, or None.
Note: The setting selected must match your physical wiring configuration. See the Avigilon Alta Access
Control System Installation Guidefor more information.
Devices 76
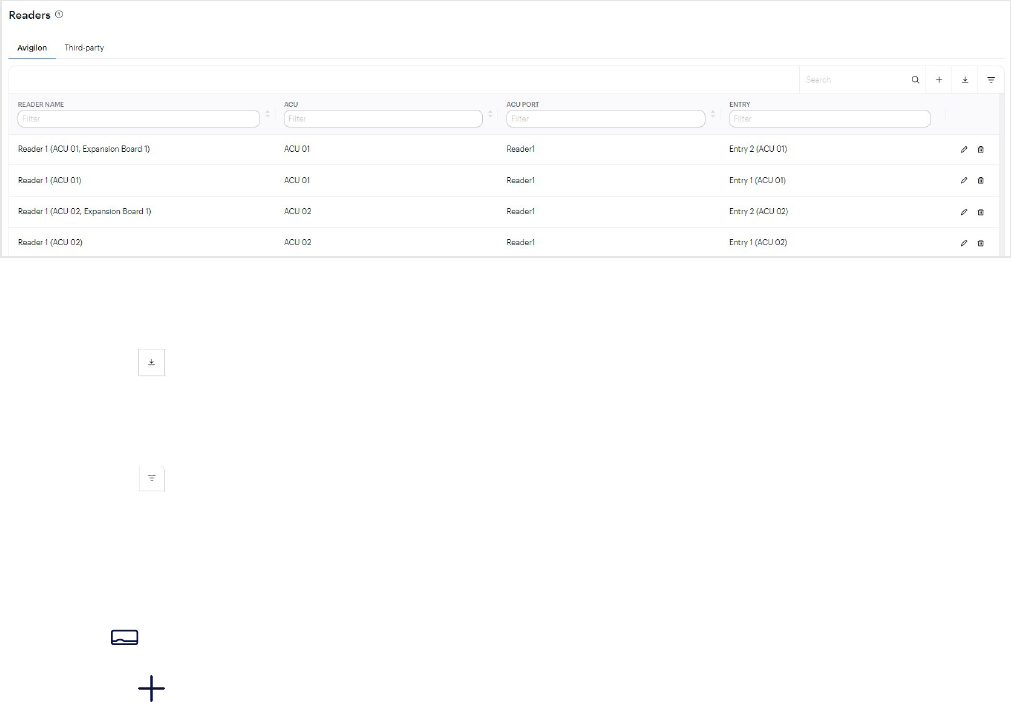
Reader management
The Readers page is where you can view and manage readers.
Export information to CSV
l
Click the icon.
Show, hide, or reset information
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
Add reader
1.
Go to Devices > Readers.
2.
Click the button in the upper-right corner.
3. Enter a name for the reader.
Names are usually relevant to the location where the reader is installed.
4. Select the ACU that will control the reader.
5. Select the port to which this reader is wired.
6. Click Save.
77
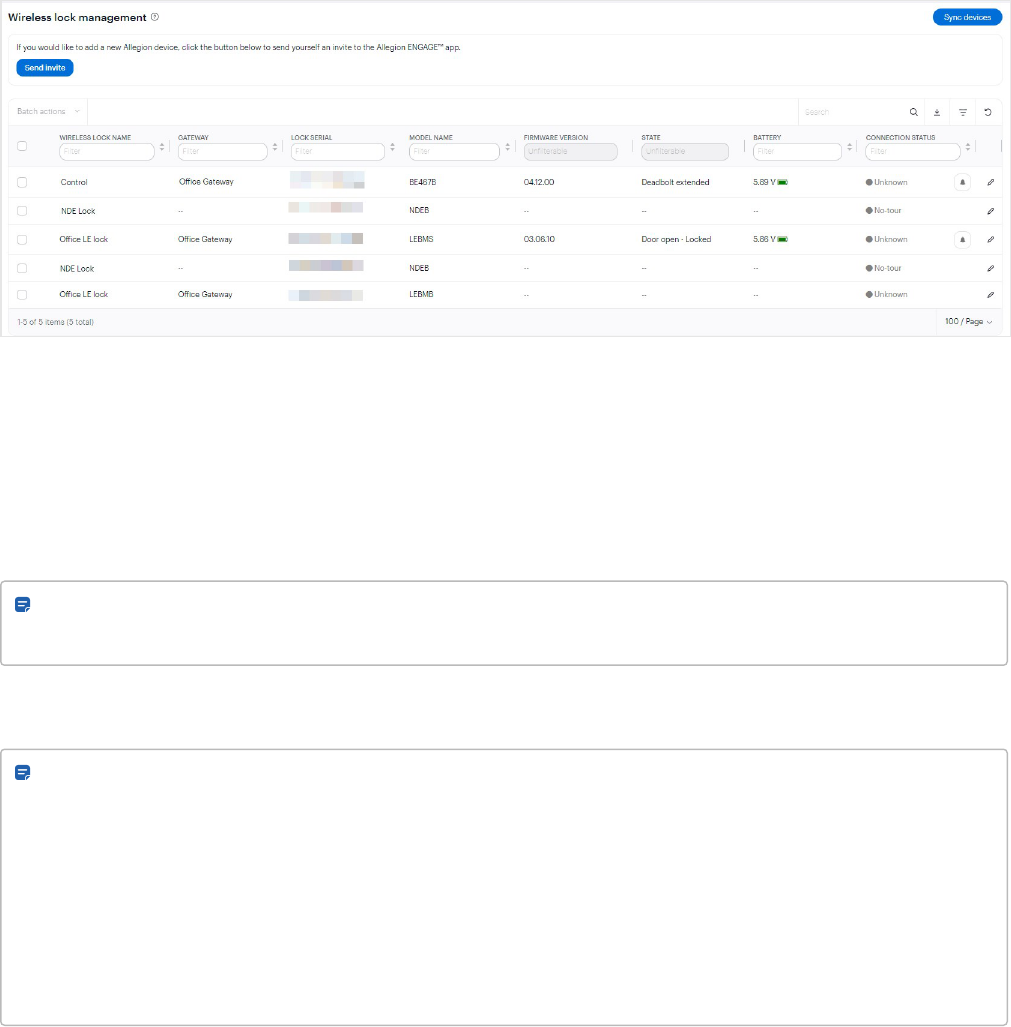
Wireless lock management
The Wireless lock management pageis where you can view and manage wireless locks that are connected to
gateways or without gateways.
For more information about the Schlage® no-tour wireless locks, see the Avigilon Access Control System Integration
Guide for Schlage Wireless Locks No-Tour (link).
Update lock firmware
1. Enter a checkmark next to one or more locks.
2. Click Batch actions to select Update firmware.
Note: To update the firmware of Schlage no-tour wireless locks, use the Avigilon Alta Access app to update
and sync the locks with the Alta Control Center.
Edit locks
Note: Settings are dependent on the lock model and configuration. To configure the following wireless lock
function, set it during the commissioning process or post-installation using the Schlage ENGAGE mobile app
(and not the Alta Control Center):
l
Apartment mode — Supported in LEB and NDEB series locks only. Ensures the gateway-connected or
no-tour connected lock remains open or closed, when the credential is scanned. The door doesn't
automatically relock when unlocked, and thus, lock out the user.
Accept the 'Openpath does not support Toggle Credential' message during initial configuration. For
more information, see the Schlage ENGAGE documentation.
78
Configure NDEB or LEB locks
1.
Go to Wireless locks andselect the lock.
2. In BASIC SETTINGS,set any of the following:
l
Power Failure Mode— Determines how the lock behaves when the battery fails.
o
As Is — Lock remains in the same state.
o
Safe— Lock is unlocked.
o
Secure— Lock is locked.
l
Beeper Enabled— Beeping is emitted from the lock when a credential is scanned.
l
Invalid Card Audit— Generates an event when an unknown (invalid) card is presented to the NDEB
wireless lock. To view these events, go to Reports > Activity logs or Dashboards > Activity
dashboard.
3. In READERSETTINGS, set the type of card and fob credentials supported by the lock.
l
For Openpath DESFire EV1, EV2, and EV3, select 14443 UID (CSN).
l
For Openpath DESFire EV3-A and Avigilon DESFire EV3-B, select 14443 Secure Mifare.
Note: You cannot enable 14443 UID (CSN) and 14443 Secure Mifare, 14443 Secure Mifare Plus,
and 14443 EV1 (NOC) at the same time.
4. In MOBILECREDENTIAL, choose whether to enable mobile credentials on this lock.
l
Communication Range — Adjust to determine how close the mobile credential needs to be near the
lock before appearing as a nearby entry in the Avigilon Alta Open app.
l
Performance — Adjust to determine how often the mobile app scans for locks.
5. Click Save.
Configure Control locks
1. From Wireless locks, select the lock.
2. Under BASIC SETTINGS, you can do the following:
l
Beeper Enabled— Beeping is emitted from the lock when a credential is scanned.
l
Invalid Card Audit— Generates an event when an unknown (invalid) card is presented to the NDEB
wireless lock. To view these events, go to Reports > Activity logs or Dashboards > Activity
dashboard.
79

Note: Reader settings cannot be edited on Control locks; high frequency cards and fobs are
enabled by default.
3. In MOBILECREDENTIAL, choose whether to enable mobile credentials on this lock.
l
Communication Range — Adjust to determine how close the mobile credential needs to be near the
lock before appearing as a nearby entry in the Avigilon Alta Open app.
l
Performance — Adjust to determine how often the mobile app scans for locks.
Configure Schlage no-tour wireless locks
1. Select a lock and edit the name or serial number.
2. Click Save.
80

Wireless lock gateway management
The Wireless lock gateways page provides the list of gateways synced using the Allegion ENGAGE app. From here,
you can sync gatewaysand update firmware.
Sync gateways with Alta Control Center
l
After completing the ENGAGE commissioning procedures, click Sync devices.
The gateways are displayed with their connection status and details.
Update gateway firmware
l
Click Update firmware.
81
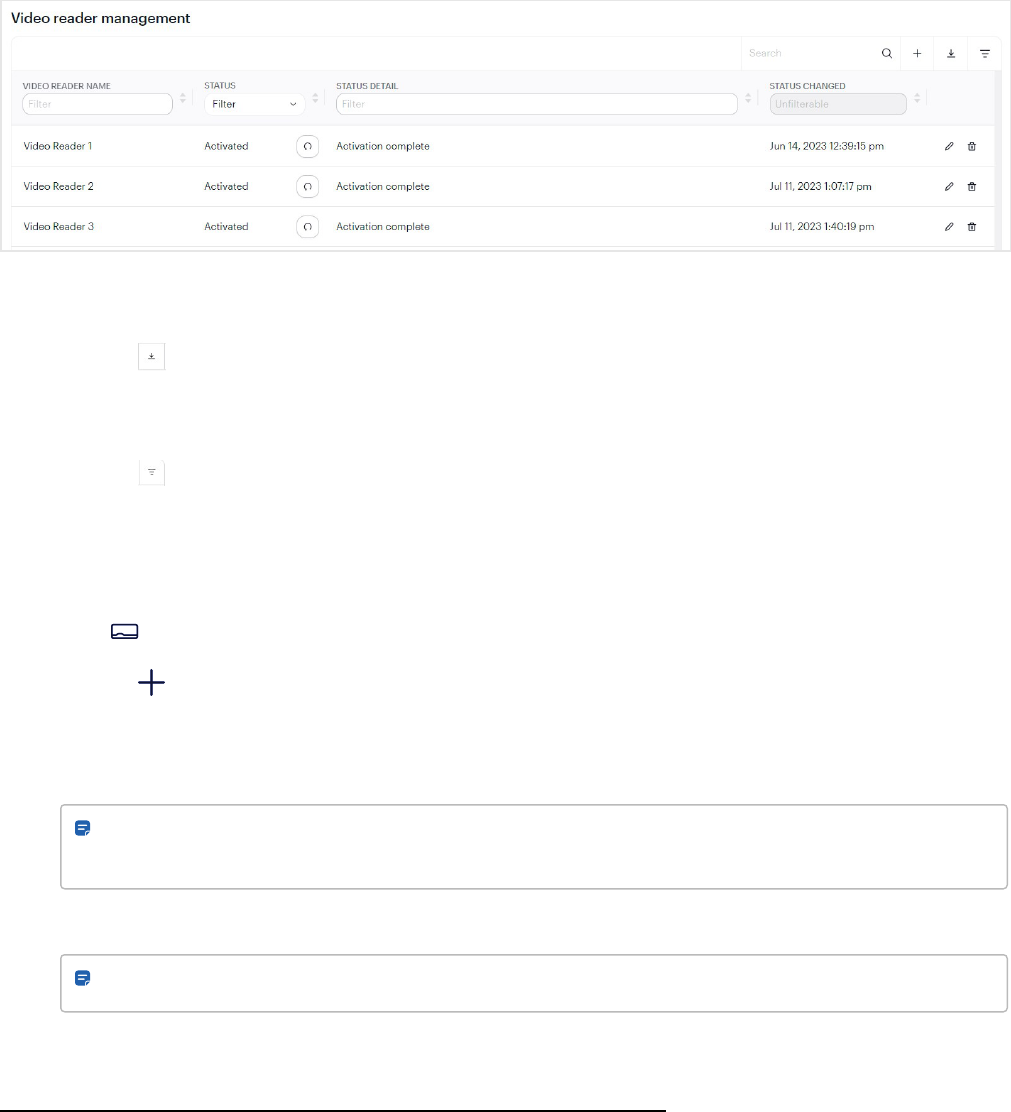
Video reader management
You can view and manage Video Reader Pro devices on the Video readers page.
Export information to CSV
l
Click the icon.
Show, hide, or reset information
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
Add video reader
1.
Go to Devices > Video readers.
2.
Click the button in the upper-right corner.
3. Enter a name for the reader.
4. If Wiegand wiring is used to connect to existing legacy systems, select the Standalone Mode toggle.
Note: Avigilon Alta licenses and internet access are not required. For more information, see this
Avigilon Alta article.
*
5. In the CLOUD VIDEOSTORAGE section, select a plan length.
Note: A cloud video storage license is required to view the video recordings.
*
For more information, see:
https://openpath.atlassian.net/servicedesk/customer/portal/16/article/1668284452?src=1724573529
82
The DETAILS section (read-only) displays information only after the reader is provisioned.
6. In the SETTINGS section:
l
Tamper sensor — Enable (default) or disable the recording of Tamper Detected events when the
reader is touched or moved.
l
Tamper sensor sensitivity — Adjust lower or higher, depending on your needs.
Note: A higher sensitivity level may produce false tamper events, for example, when someone
triggers a Touch to Unlock.
7. Click Save.
8.
On the Ports tab, click the Port button to view and manage reader, relay, and Wiegand port settings.
For next steps, see:
l
Add zones on page57 if not created yet.
l
Add entries on page61 and enter the device in the Controller field.
Note: During this step, you can configure the Wiegand port on the video intercom reader, as an input or
output, for Mobile Gateway mode.
l
Installing the Video Reader Pro / Video Reader Intercom Pro or the Avigilon Access Control Core Installation
Guide (link)
After provisioning, return to the Alta Control Center to finish configuring video settings or to enable ONVIF
1
.
View activated video reader
1. After provisioning the physical reader, return to the Alta Control Center to view the activated device in the
DETAILS section.
1
ONVIF is a trademark of Onvif, Inc.
83
2. Finish configuring video settings or to enable ONVIF.
Configure recording, detection, and ONVIF settings
1.
Go to Devices > Video readers, and select a reader.
2. Select the Video tab.
l
In the VIDEO PROPERTIES section:
o
Quality — High, Medium, or Low quality.
o
Brightness, Contrast, Saturation, and Sharpness — Adjust as necessary.
o
Wide Dynamic Range (WDR) — Disable (default) or enable to adjust for backlighting and other
extreme lighting conditions.
o
Night mode — Auto (default), Always on, or Always off.
o
Anti-overexposure — Enable (default) to reduce IR glare on persons and objects approaching
the video reader.
l
In the DETECTION SETTINGS section:
o
Enable motion detection — Enable (default) or disable to adjust the sensitivity settings of
motion detection by the camera.
84
o
Enable QR code recognition — Enable or disable (default) QR code detection by the camera
when a user presents a third-party QR code before entry. To set up the action taken when a QR
code is detected by the camera, see Add rules and triggers on page126.
Note: A Premium or Enterprise plan is required.
o
In the live video feed, draw a box on the feed to add privacy areas or regions of interest.
Privacy area — Hides sensitive areas of the feed from users.
Region of interest — Applies motion detection to only the marked areas.
l
In the RECORDINGSETTINGS section:
o
Burn current time into recordings and Burn camera name into recordings — Enable (default)
or disable the settings.
3. Click Save.
Enable ONVIF
Enable ONVIF
1
if you are exporting video to a third-party VMS.
1. On the Video tab, select the Enable ONVIF toggle (off by default).
2. Click Open camera UI.
Note: For best results, use Chrome, Firefox, or Microsoft Edge.
3. Log in using the default username and password.
Important: You must be logged in on the same LAN as the camera.
4.
Go to Configurations > Security > User accounts to change the password.
Note: The Alta Control Center always displays the default password, even if you change the password
in the Open camera UI page. To reset the password back to the default, disable ONVIF, wait 10
seconds, then enable again.
1
ONVIF is a trademark of Onvif, Inc.
85

Change cloud video storage plan
You can change your cloud video storage plan length, however, plans are not retroactive. For example, if you are
currently on a 30-day plan and you switch to an 180-day plan, you’ll still only have access to the past 30 days of clips
with 180 days of storage moving forward.
1.
Go to Devices > Video readers, and select the video reader.
2. In CLOUD VIDEOSTORAGE, select a different plan length.
3. Click Save.
86
Video intercom reader management
You can view and manage Video Intercom Reader Pro devices on the Video intercom reader management page,
including configuring two-way audio and call routing to building occupants, and more.
Export information to CSV
l
Click the icon.
Show, hide, or reset information
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
Add video intercom reader
Note: Before you start, go to the App marketplace and install the Video Intercom Voice Assistant app.
1.
Go to Devices > Video intercom readers.
2.
Click the button in the upper-right corner.
3. Enter a name for the device.
4. In the CLOUD VIDEOSTORAGE section, select a plan length.
Note: A cloud video storage license is required to view the video recordings.
The DETAILS section (read-only) displays information only after the reader is provisioned.
5. In the SETTINGS section:
87
l
Tamper sensor — Enable (default) or disable the recording of Tamper Detected events when the
reader is touched or moved.
l
Tamper sensor sensitivity — Adjust lower or higher, depending on your needs.
Note: A higher sensitivity level may produce false tamper events, for example, when someone
triggers a Touch to Unlock.
6. Click Save.
7.
On the Ports tab, click the Port button to view and manage reader, relay, and Wiegand port settings.
For next steps, see:
l
Add zones on page57 if not created yet.
l
Add entries on page61 and enter the device in the Controller field.
Note: During this step, you can configure the Wiegand port on the video intercom reader, as an input or
output, for Mobile Gateway mode.
l
Installing the Video Reader Pro / Video Reader Intercom Pro or the Avigilon Access Control Core Installation
Guide (link)
View activated video intercom reader
1. After provisioning the physical reader, return to the Alta Control Center to view the activated device in the
DETAILS section.
2. Finish configuring video settings, intercom and routing profile settings, or to enable ONVIF.
Configure recording, detection, and ONVIF settings
1.
Go to Devices > Video intercom readers, and select a reader.
2. Select the Video tab.
88
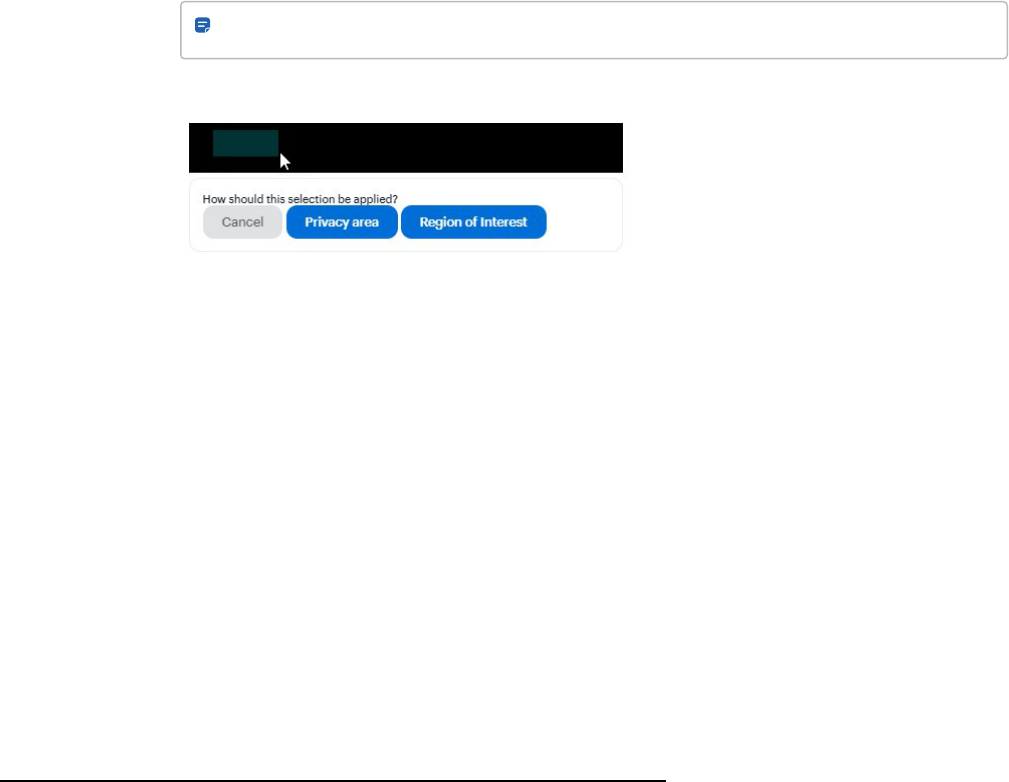
l
In the VIDEO PROPERTIES section:
o
Quality — High, Medium, or Low quality.
o
Brightness, Contrast, Saturation, and Sharpness — Adjust as necessary.
o
Wide Dynamic Range (WDR) — Disable (default) or enable to adjust for backlighting and other
extreme lighting conditions.
o
Night mode — Auto (default), Always on, or Always off.
o
Anti-overexposure — Enable (default) to reduce IR glare on persons and objects approaching
the video reader.
In the DETECTION SETTINGS section:
o
Enable motion detection — Enable (default) or disable to adjust the sensitivity settings of
motion detection by the camera.
o
Enable QR code recognition — Enable or disable (default) QR code detection by the camera
when a user presents a third-party QR code before entry. To set up the action taken when a QR
code is detected by the camera, see Add rules and triggers on page126.
Note: A Premium or Enterprise plan is required.
o
In the live video feed, draw a box on the feed to add privacy areas or regions of interest.
Privacy area — Hides sensitive areas of the feed from users.
Region of interest — Applies motion detection to only the marked areas.
l
In the RECORDINGSETTINGS section:
o
Burn current time into recordings and Burn camera name into recordings — Enable (default)
or disable the settings.
3. Click Save.
Enable ONVIF
Enable ONVIF
1
if you are exporting video to a third-party VMS.
1. On the Video tab, select the Enable ONVIF toggle (off by default).
2. Click Open camera UI.
1
ONVIF is a trademark of Onvif, Inc.
89
Note: For best results, use Chrome, Firefox, or Microsoft Edge.
3. Log in using the default username and password.
Important: You must be logged in on the same LAN as the camera.
4.
Go to Configurations > Security > User accounts to change the password.
Note: The Alta Control Center always displays the default password, even if you change the password
in the Open camera UI page. To reset the password back to the default, disable ONVIF, wait 10
seconds, then enable again.
Change cloud video storage plan
You can change your cloud video storage plan length, however, plans are not retroactive. For example, if you are
currently on a 30-day plan and you switch to an 180-day plan, you’ll still only have access to the past 30 days of clips
with 180 days of storage moving forward.
1.
Go to Devices > Video intercom readers, and select the video reader.
2. In CLOUD VIDEOSTORAGE, select a different plan length.
3. Click Save.
Configure two-way audio
On the Intercom tab of a Video Intercom Reader Pro, you can configure two-way audio communication.
Welcome greeting and message
l
In the TEXT TOSPEECH section, enter:
o
Default message — The message that plays if routing profiles are not used, or no one is taking
intercom calls (similar to a voicemail message).
o
Initial greeting — The welcome greeting.
Microphone and speaker settings
l
In the AUDIO section, MICROPHONE section:
o
Enabled - always on — Audio is 'on' during intercom calls and in the live video feed.
o
Enabled - On during intercom events — Audio is 'on' during intercom calls only.
o
Disabled — Audio is disabled.
o
Microphone level — Adjust lower or higher, as needed.
o
Audio recording toggle — Enable to record audio during intercom events.
90
l
SPEAKER section:
o
Speaker enabled — Adjust the speaker volume, lower or higher, as needed.
o
Privacy — Deselect the toggle, as needed.
o
Audio detection toggle — Enable to detect audio when the microphone is always on. Adjust the
detection sensitivity, lower or higher, as needed.
SIP mode
For SIP enabled and Voice over IP (VoIP) devices.
For information about the installation and configuration of your PBX software and VoIP phone systems, see third-
party vendor documentation.
l
In the SIP section, enter:
o
SIP mode — Change SIP disabled (default) to SIPonly to use SIP or SIP failover to use SIP only during
internet outages.
Note: When SIPis enabled on the video intercom reader, the voice assistant will be disabled.
o
SIP address — The IPaddress of the PBX software.
o
Authentication user — The extension number for the video intercom reader (for example, 5555).
o
Authentication password — The password for the extension number for the video intercom reader.
o
Display name (optional) — The caller ID to be displayed on the video intercom reader (for example, OP
intercom).
o
ID/Call destination — The extension number for the VoIP phone system.
o
Device SIPnumber — The extension number for the video intercom reader. Use the same value in
Authentication user.
Configure call routing to users, units, or front desk
On the Routing profile tab of a Video Intercom Reader Pro, you can configure the call routing profiles used by the
voice assistant to find users, units, or the front desk.
Note: Ensure you are added to an active routing profile to receive notifications in the Alta Control Center.
Before you start
l
Create access groups and access schedules for the Direct Connect profile.
Note: This step is required for all routing profiles.
l
Add building details and zones for multi-tenants for the Unit Connect profile.
91

Add existing routing profile
1.
Click the button in the upper-right corner.
2. Select the Use existing profile toggle.
3. In Intercom profile, select an existing profile.
4. Click Save.
Add new routing profile
1.
Click the button in the upper-right corner.
2. Leave the Use existing profile toggle deselected.
3. In the PROFILECONFIGURATION section, enter the name of the profile. In Profile type, select:
l
Direct Connect — Visitors call users by stating their name.
l
Front Desk Connect — Visitors call a group of users designated as the Front Desk.
l
Unit Connect — Visitors call one or more users by stating the unit or apartment number. For more
information, see Building management on page55.
l
Visual Voicemail — Visitors may leave a voicemail to be seen by a site administrator.
4. In the RECIPIENTCONFIGURATION section, enter the access groups that can be searched by name at the
intercom.
5. In the BACKUPCONFIGURATION section, enter the timeout in seconds before using the fallback profile when
the recipient can't be reached.
For example, if a visitor can't reach a user (Direct Connect) after 15 seconds, the visitor will hear the Farewell
message.
6. Click Save.
Use QR codes to look up directories on phones (optional)
On the Virtual directory tab of a Video Intercom Reader Pro, you can generate and print a QR code that visitors can
scan to look up a directory on their phone and then tap the icon to speak to the user or unit through the intercom.
If nobody answers, they can leave a voicemail message (if enabled)or tap Front desk to let them in.
92
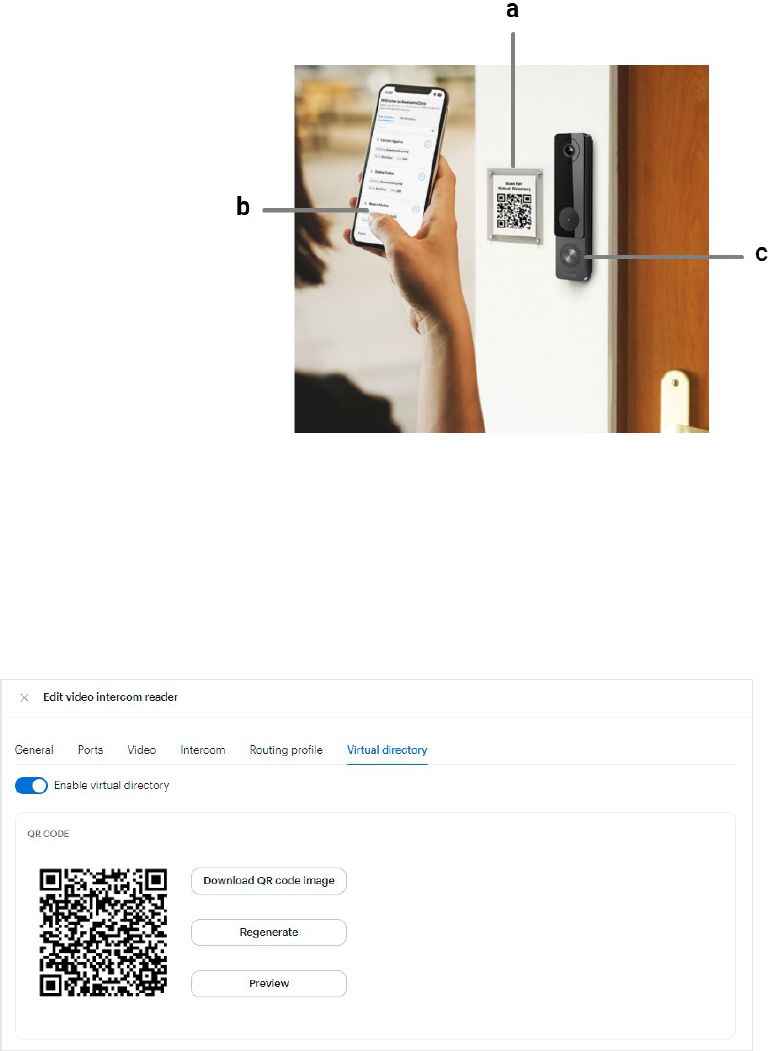
Figure 1 Overview of QR code placement (a), QR code scanning and directory retrieval (b), and intercom communication (c)
Create user directory and/or unit directory
Before you start, ensure the Direct Connect and/or Unit Connect settings are defined on the Routing profile tab, as
described in the previous section.
Generate QR code
1. Select the Enable virtual directory toggle (deselected by default).
A QR code is generated and additional fields are shown.
2. In Directory title, enter the title of the directory.
Example: "Welcome to our building"
3. In Notes for visitors, enter instructions.
93
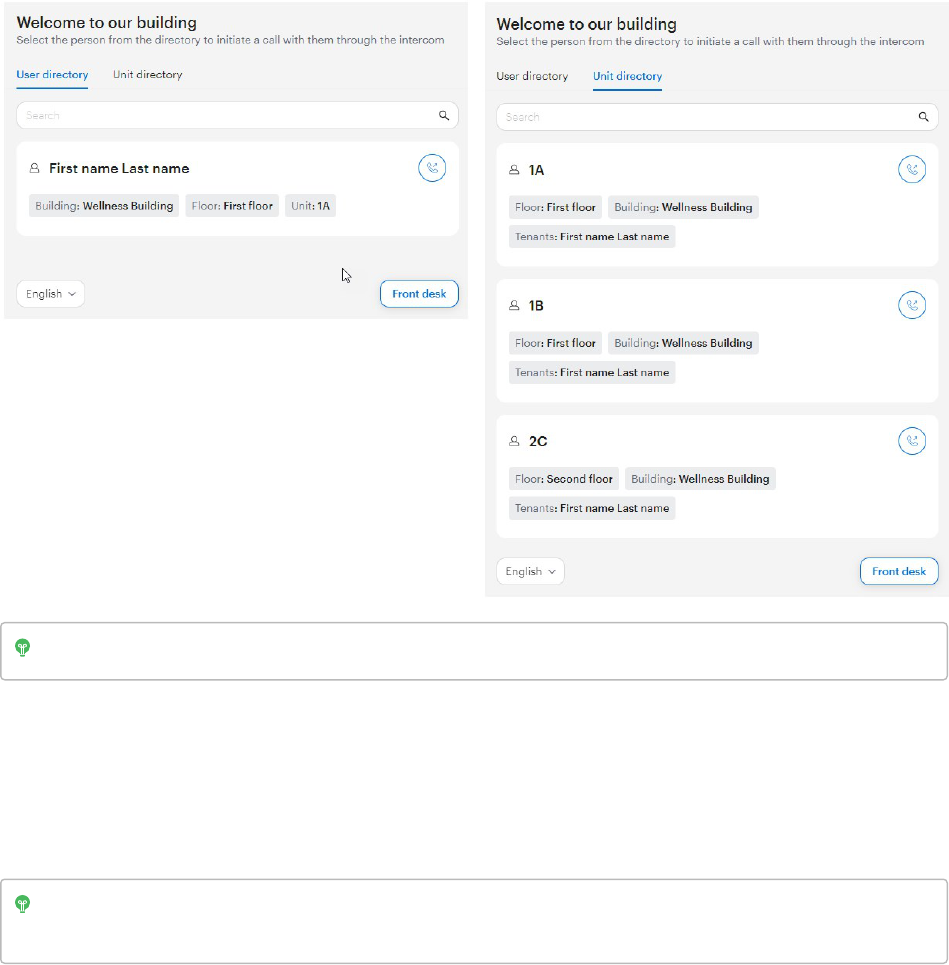
Example: "Select the person from the directory to initiate a call with them through the intercom"
4. In User directory values to display, enter the user directory values.
Examples: "Building, Floor, Unit"
5. In Unit directory values to display, enter the unit directory values.
Examples: "Floor, Tenant"
6. Click Save and then Preview to preview the user and unit directories (example below).
Tip: If the preview window expires, click Preview again to redisplay the directories.
Download and print QR code
1. When you are satisfied with the preview, click Download QR code image.
2. Find the JPGfile in the Downloads folder on your desktop.
3. Incorporate the QR code into signage to be placed near the Video Intercom Reader Pro.
Tip: Printing the QR code onto a waterproof sticker is recommended. You may find ready-to-use labels
and templates at your local supplier.
94
Regenerate QR code
1. Click Regenerate and confirm the operation.
Note: Regenerating the QR code will delete the former QR code.
2. Download and reprint the new QR code.
Disable directory
1. Deselect the Enable virtual directory toggle.
2. Click Delete to confirm the operation.
Note: Disabling the directory will delete it.
View live video feed
After provisioning the Video Intercom Reader Pro, you can view live video feed from the device in several places.
Note: A cloud video storage license is required to view the video recordings.
l
Go to Devices, select the video intercom reader, and then the Video tab.
l
Go to Dashboards and select the Activity dashboard.
l
Go to Cameras page and select the video intercom reader. See Initiate calls to intercom on Video
Intercom Reader Pro on page35 and Play and download video on page35.
Answer calls from intercom
If configured, you can receive notifications in the Alta Control Center when a visitor calls a user, group, or unit from
the intercom.
1. Click the notification in the lower-right corner to view the intercom device.
2. Do any of the following:
l
Answer the call
l
Unlock the entry
For the required configuration, see the Enable intercom notifications toggle in User profile on page22 and Configure
call routing to users, units, or front desk on page91.
95
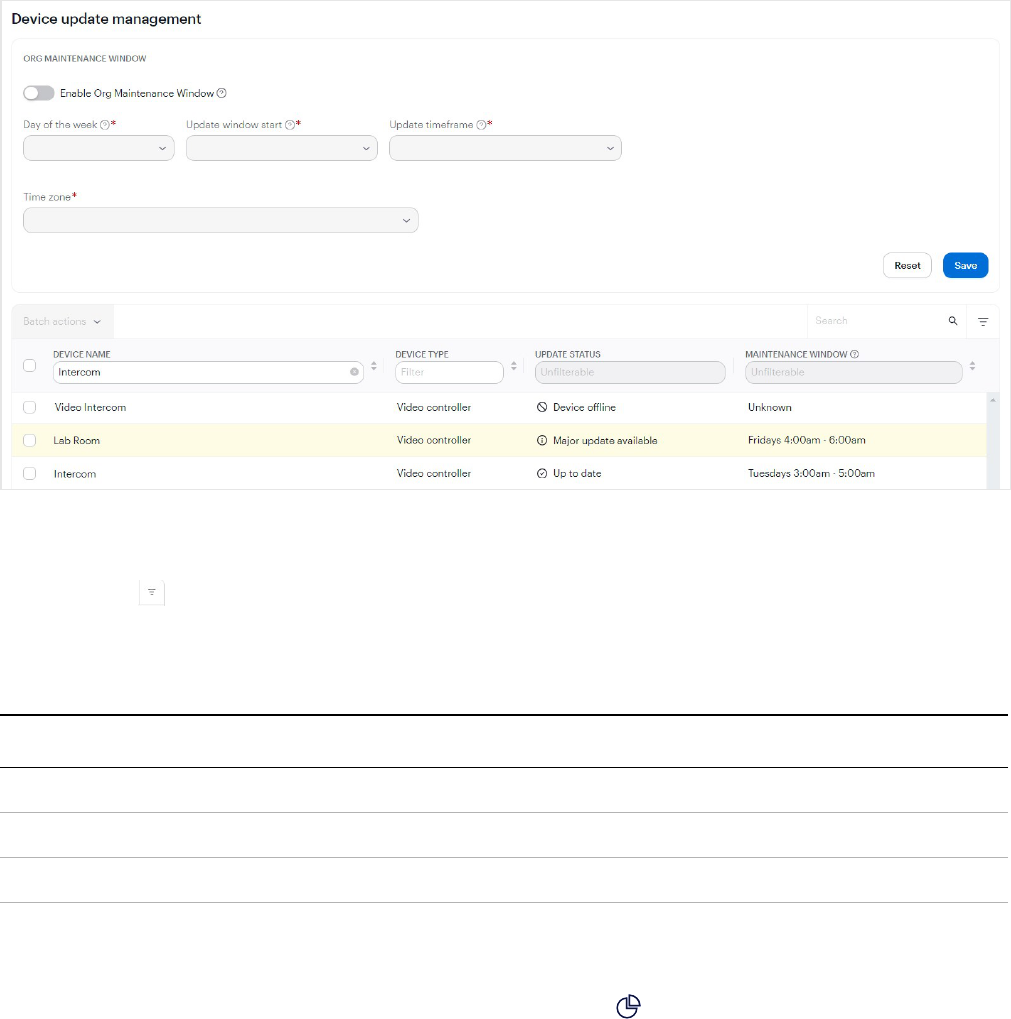
Device update management
The Device updates page provides a list of the software updates for the devices managed in Alta Control Center,
including when their default maintenance windows are scheduled to run. Updates are typically small and do not
introduce noticeable downtime. Kernel and firmware updates may take longer and require downtime.
Show or hide device updates
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
l
Information is read-only and cannot be edited.
Field Description
Device ID The ACU or Video device ID.
Device name The configured name of the device.
Device type Controller or Video controller.
Update status Device offline — The device is offline.
Unavailable — A connection issue has occurred between the device and the cloud.
For more information on the device status, go to Dashboards > Device dashboard.
Up to date — The device has the newest software version.
Minor update queued — The device has a minor software version available.
96
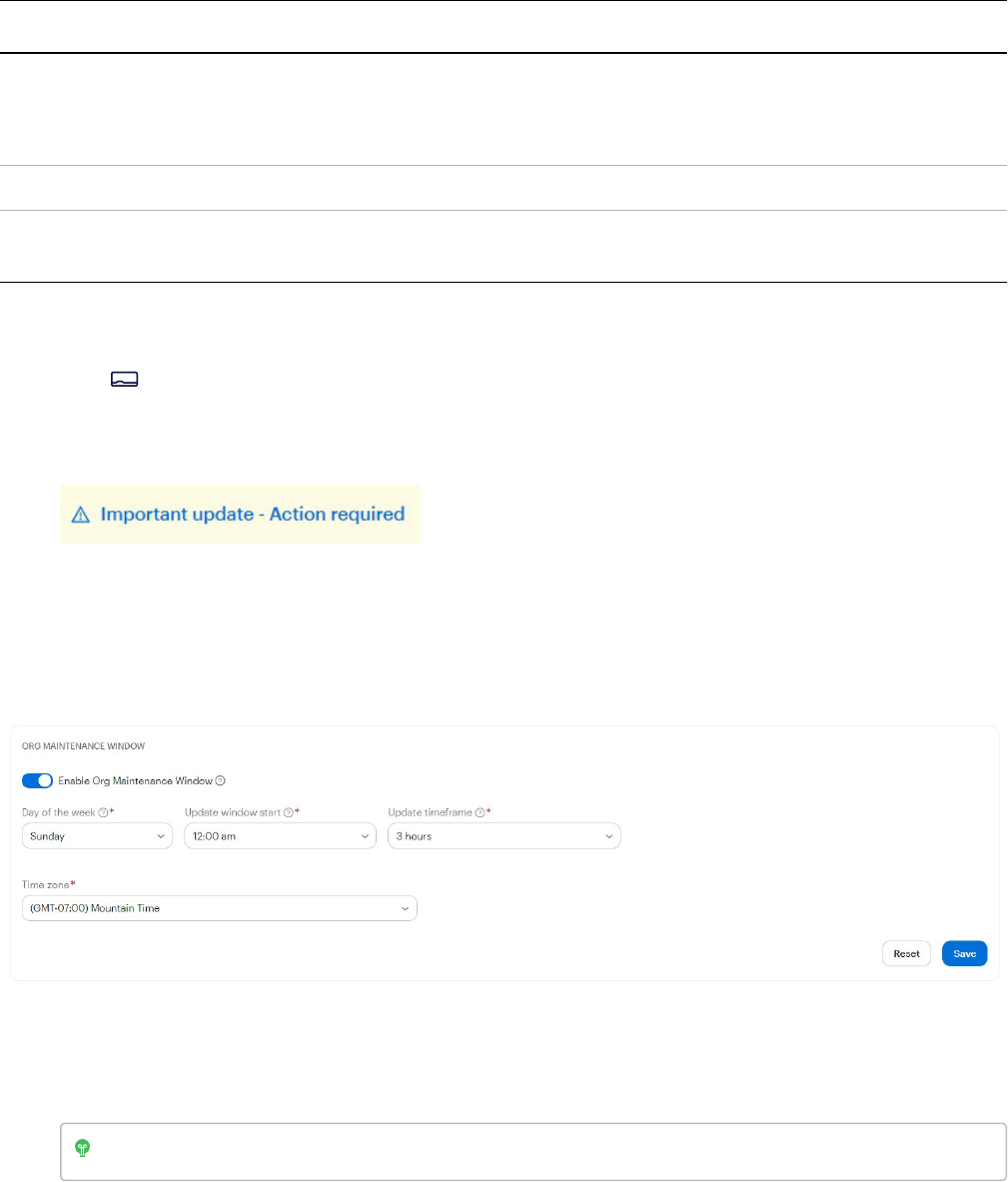
Field Description
Major update available — The device has a major software version available.
Important update - Action required — The device has an important software update that
requires your immediate action.
Update type Automatic is the default.
Maintenance
window
The weekly maintenance window for applying software updates at the beginning of the hour
shown.
Apply device updates on demand
1.
Go to Devices > Device updates.
2. Click a device that displays the Important update - Action required, Major update available, or Minor update
queued status. For example:
A message indicates the expected downtime for an important update.
3. Click Update Now. The updates are applied.
Set up a maintenance window for all device updates
1. Select the Enable Org Maintenance Window toggle.
2. Specify the day of the week, the beginning of the hour, the total hours allotted for completing all device
updates, and the timezone of the organization.
Tip: A longer timeframe is recommended when applying software updates to many devices.
3. Click Save.
The updates are applied in random order and complete within the allotted timeframe.
97
Reports
The Reports page is where you can view user, entry, and system activity.
The Alta Control Center offers a wide variety of report types:
Note: If you are viewing reports about Schlage no-tour wireless locks, only the following reports are applicable:
Activity logs, Alarms, Entry activity (by user), Entry activity summary, User activity (by entry), and User activity
summary. Information may be out-of-date. Report information is available only after visiting the no-tour
wireless lock in person and completing a manual sync using the Avigilon Alta Access app.
l
Activity logs— Displays a list of all unlock requests and hardware-related events across your Avigilon Alta
access control system and any cameras connected through your Alta Aware account.
l
Alarms — Displays the severity levels of alarms, the actions of the user or role that resolved them, video
camera recordings, and more.
Note: A Premium or Enterprise plan is required. The Alarm Management app must be installed.
l
Credentials— Displays all credentials within your organization, filtered by credential type.
l
Entry access audit— Displays the users that have access to any given entry.
l
Entry activity (by user), Entry activity summary, User activity (by entry), User activity summary — Displays
user activity, entry activity, and external IDof the entry or user, in helpful charts and diagrams.
l
Muster — Used during an emergency evacuation or drill to view the users who may be on site, and account for
their safety. The user must be assigned the Muster report role.
Note: A Premium or Enterprise plan is required. The Muster Reports app must be installed.
l
Occupancy — Displays the number of unique users who have accessed one or more sites over a period of
time, and the average number of occupants each day.
Note: A Premium or Enterprise plan is required.
Example:
Reports 98
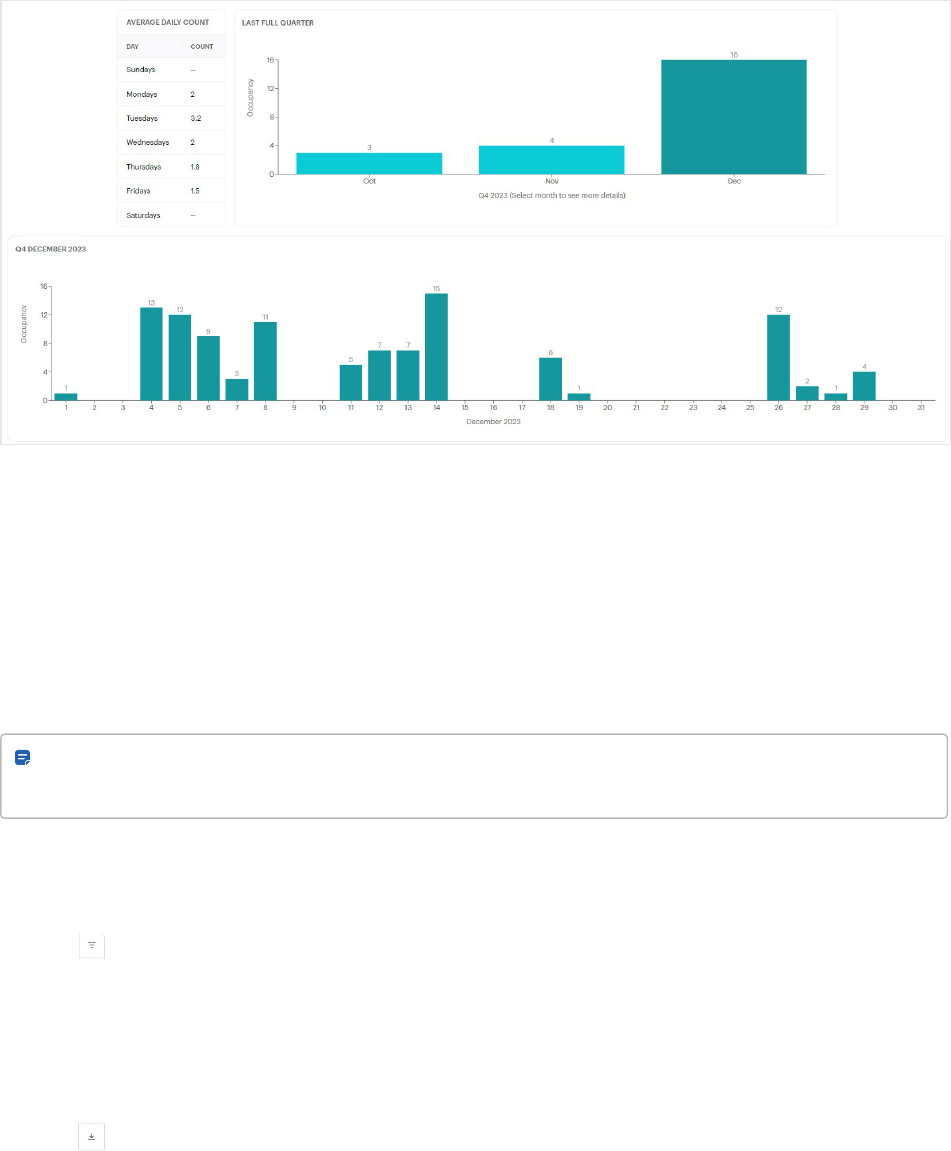
l
Portal audit report— Displays a log of the changes in the Alta Control Center or through the Avigilon Alta API.
l
Scheduled reports — Displays the reports scheduled for specified time periods and data categories and
includes the history of report requests.
l
User access audit — Displays all entries that a selected user has accessed.
A Premium or Enterprise plan is required.
l
Visual activity report — Displays video snapshots of entry events, which are filtered by user, site, entry, and
time.
Note: Before using this report, you must set up the Cisco Meraki integration or have Video reader
management on page82 installed.
Show, hide, or reset information
l
Click the icon to show or hide information in columns.
l
Click Reset table to go back to the default view.
Export report to CSV
l
Click the icon.
Reports 99
Configure reports (Activity logs, Alarms, and Portal audit report)
1.
Go to Reports and select the report type.
2. Select a time period for the report.
3. Select a Report delivery option:
l
Deliver to current browser tab— When using this method, do not refresh or close the browser tab.
Reports may take a few minutes to generate. Not recommended for large datasets.
l
Deliver via email— Use for large datasets. Select this method to run the report in the background and
receive an email when the report is done. You can deliver the report to multiple email addresses.
4. In Filter reports by,enter the report data to be retrieved, such as Alarm event. In Filter items, enter additional
report criteria.
5. Optional. Click Add filter to repeat the previous step.
6. Click Search. The report is displayed in the current browser tab or emailed, depending on the delivery option.
View and mark users as safe in the Muster report (Premium and
Enterprise plans)
1.
Go to Reports > Muster.
2. Select a time period for the report.
3. Optional. Select sites and zones.
4. Click Search. Do any of the following:
l
Select the Mark as safe toggle in the generated report after you have ensured a user is safe.
l
View the users who are automatically marked as safe in the generated report, if their credentials were
scanned at the muster point entry before you generated the report.
Note: A credential reader is required to be installed at the entry. This reader should only be used in a
muster event and not for any other purpose.
Schedule report generation and forwarding (Premium and
Enterprise plans)
1.
Go to Reports > Scheduled reports.
2.
Click in the upper-right corner.
3. Enter a name for the scheduled report.
4. Select the type of report.
Reports 100

Note: Only Activity logs, Occupancy report, andPortal audit report logsare supported.
5. Select a time period for the report and configure report settings.
6. Enter email addresses to send the reports to and select a Frequency.
7. Click Save.
View scheduled reports (Premium and Enterprise plans)
1.
Go to Reports > Scheduled reports.
2. Select the Request history tab.
Previously generated scheduled reports will appear here. A scheduled report will expire after 30 days.
3.
Click to download a CSV file of the report.
Reports 101
App marketplace
Note: Depending on how your account is configured, you may need your integrator to enable App
marketplace apps.
Avigilon Alta apps connect to third-party software and services that let you sync users and add functionality toAlta
Control Centerand other systems that you use.
l
Get apps is where you can add and configure apps for your system. Click an app to learn more about setup
and configuration.
l
Select All categories to view all the apps that can be installed from Alarm Integrations to Workplace
Communication.
l
My apps is where you can view your installed apps. Click an app to edit or configure settings.
Identity management
Identity Management / HR Softwareapps let you add and sync users from identity providers you already use.
Currently, Alta Control Center integrates with Google Workspace™ productivity and collaboration tools, Microsoft
Azure Active Directory, OneLogin Trusted Experience Platform™, Okta, and Workday® Human Capital Management
applications. The SAML Single Sign-on app works with your SAML-enabled identity provider system for single sign-
on only, without user syncing.
Note: Alta Control Center requires that you keep at least one Avigilon Alta-native administrative account in
case there are ever any issues connecting to your identity provider.
App marketplace 102

Manually sync accounts
After setting up an identity provider integration, you have the option to manually sync users at any time to display
them in the Alta Control Center.
l
Click the Synchronize button on the app's settings page.
Note: Syncing is not applicable to the SAML Single Sign-on integration.
App marketplace 103
Google Workspace
Note: To enable this feature, you must have administrative privileges in your Google Workspace account:
l
Directory User Read-Only:
https://www.googleapis.com/auth/admin.directory.user.readonly
l
Directory Group Read-Only:
https://www.googleapis.com/auth/admin.directory.group.readonly
1.
Go to App marketplace > Get apps. Click the Google Workspace or Google Workspace Advanced tile,
depending on your subscription, and then + Get app.
2. Google will prompt you to sign in. Sign in with your Google account and allow the Alta Access system to
access your users and groups.
3. After signing in, you'll be directed back to Alta Control Center where you can enable the following settings:
l
Auto-sync every 1 houror Auto-sync every 15 minutes — Syncs Alta Control Center with the identity
provider system, once every hour or once every 15 minutes, depending on your subscription. See
Administration > Account for subscription details.
l
Auto-create mobile credential — Creates a mobile credential for every user.
l
Auto-create cloud key credential— Creates a cloud key credential for every user.
l
Sync mobile phone numbers — Syncs the mobile phone number for every user. Phone numbers must
use E.164 format with a maximum of 15 digits: +[country code][subscriber number
including area code]
Note: The default mobile phone number (mobile field) will be synced. If users have a work
mobile phone number (work_mobile field) that is the primary number, the work mobile phone
number will be synced instead.
l
Enable single sign-on (SSO) with portal access — Lets users log into the Control Center with their
Google credentials.
Tip: Consider using the control.openpath.com/loginSSO or control.eu.openpath.com/loginSSO
setup page to prevent users from trying a standard login.
l
Only import users from groups that have an Avigilon Alta group mapping— If enabled, no users are
imported from the identity provider if they are not assigned to a group.
l
Auto-remove users from groups— Removes users from groups if they no longer exist in the identity
provider's groups.
4. To map a specific group or all groups from the identity provider to Alta Control Center:
App marketplace 104

Note: Complete this step if you have enabled the Only import users from groups that have an Avigilon
Alta group mapping setting.
a. Select the group from the identity provider.
b. Select the group from Avigilon Alta Control Center.
c. Click Create Access Group Mapping.
d. Repeat for all the groups that need to be mapped.
App marketplace 105
Microsoft Azure AD
You can integrate Microsoft Azure Active Directory (Azure AD)
1
with Avigilon Alta Control Center to import and sync
users and access groups automatically. OAuth2 and OAuth Client authentication are supported.
l
Set up OAuth2authentication below
l
Set up OAuth Clientauthentication on the next page
Note: To enable this integration, you must be assigned the Application Administrator role in Azure AD.
Set up OAuth2authentication
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to App marketplace > Get apps. Click the Microsoft Azure AD or Microsoft Azure AD Advanced tile,
depending on your subscription.
3.
Go to App marketplace > My apps. Select the Microsoft app.
4. Microsoft will prompt you to sign in. Sign in with your Azure AD account and click Accept to allow the Avigilon
Alta system to access your users and groups.
Note: The Avigilon Alta system can only read data from your Azure account; it cannot write data or
make any changes within the Azure system. The token the Avigilon Alta system uses only has read
permissions for Azure users, groups, and directory data.
5. After signing in, you'll be directed back to Alta Control Center where you can enable the following settings:
l
In Authentication strategy, select OAuth2.
l
Auto-sync every 1 houror Auto-sync every 15 minutes — Syncs Alta Control Center with the identity
provider system, once every hour or once every 15 minutes, depending on your subscription. See
Administration > Account for subscription details.
l
Auto-create mobile credential — Creates a mobile credential for every user.
l
Auto-create cloud key credential— Creates a cloud key credential for every user.
l
Sync mobile phone numbers — Syncs the mobile phone number for every user. Phone numbers must
use E.164 format with a maximum of 15 digits: +[country code][subscriber number
including area code]
l
Enable single sign-on (SSO) for users with portal access — Lets users log into the Alta Control Center
with their Azure credentials.
1
Microsoft and Azure are trademarks of the Microsoft group of companies.
App marketplace 106
Tip: Consider using the control.openpath.com/loginSSO or control.eu.openpath.com/loginSSO
setup page to prevent users from trying a standard login.
l
Only import users from groups that have an Avigilon Alta group mapping— If enabled, no users are
imported from the identity provider if they are not assigned to a group.
l
Auto-remove users from groups— Removes users from groups if they no longer exist in the identity
provider's groups.
6. To map a specific group or all groups from the identity provider to Alta Control Center:
Note: Complete this step if you have enabled the Only import users from groups that have an Avigilon
Alta group mapping setting.
a. Select the group from the identity provider.
b. Select the group from Avigilon Alta Control Center.
c. Click Create Access Group Mapping.
d. Repeat for all the groups that need to be mapped.
Set up OAuth Clientauthentication
1. Sign in to your Microsoft Azure account and register your application in the Azure portal.
1
2. Set up OAuth client (service principal) authentication:
2
a. Select your application in the Azure portal.
b. Go to the Certificates & secrets page and select Client secrets (0). Set up your client secret (also
known as application password). Record the Secret ID (which appears only this one time) in a secure
place.
c. Set an expiration period for the client secret (for example, 180 days or 6 months).
Note: Syncing will
stop
at the end of the expiration period. Remember to update the client secret
before this occurs.
d. Configure your application permissions in Configured permissions. At a minimum, Group.Read.All
and User.Read.All must be granted admin consent in the API / Permissions name column.
1
For more information, see Microsoft documentation: https://learn.microsoft.com/en-us/azure/active-directory/develop/howto-
create-service-principalportal
2
For more information, see Avigilon Alta article:
https://openpath.atlassian.net/wiki/spaces/EHC/pages/2023391259/How+do+I+sync+users+using+OAuth+Client+Service+Pri
ncipal+with+Microsoft+Azur e+Active+Directory#service
App marketplace 107
e. Go to the Overview page. Record the Application (client) ID and Directory (tenant) ID to be entered in
the Alta Control Center.
3. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
4.
Go to App marketplace > My apps. Click the Microsoft app.
5. Microsoft will prompt you to sign in. Sign in with your Azure AD account and click Accept to allow the Avigilon
Alta system to access your users and groups.
Note: The Avigilon Alta system can only read data from your Azure account; it cannot write data or
make any changes within the Azure system. The token the Avigilon Alta system uses only has read
permissions for Azure users, groups, and directory data.
6. Now you can enable the following settings:
l
In Authentication strategy, select OAuth Client.
l
In Client Id, enter the Application (client) ID from the Azure portal.
l
In Client secret, enter the Secret ID for the client secret from the Azure portal.
l
Auto-sync every 1 houror Auto-sync every 15 minutes — Syncs Alta Control Center with the identity
provider system, once every hour or once every 15 minutes, depending on your subscription. See
Administration > Account for subscription details.
l
Auto-create mobile credential — Creates a mobile credential for every user.
l
Auto-create cloud key credential— Creates a cloud key credential for every user.
l
Sync mobile phone numbers — Syncs the mobile phone number for every user. Phone numbers must
use E.164 format with a maximum of 15 digits: +[country code][subscriber number
including area code]
l
Enable single sign-on (SSO) for users with portal access — Lets users log into the Alta Control Center
with their Azure credentials.
Tip: Consider using the control.openpath.com/loginSSO or control.eu.openpath.com/loginSSO
setup page to prevent users from trying a standard login.
l
Only import users from groups that have an Avigilon Alta group mapping— If enabled, no users are
imported from the identity provider if they are not assigned to a group.
l
Auto-remove users from groups— Removes users from groups if they no longer exist in the identity
provider's groups.
7. To map a specific group or all groups from the identity provider to Alta Control Center:
App marketplace 108

Note: Complete this step if you have enabled the Only import users from groups that have an Avigilon
Alta group mapping setting.
a. Select the group from the identity provider.
b. Select the group from Avigilon Alta Control Center.
c. Click Create Access Group Mapping.
d. Repeat for all the groups that need to be mapped.
App marketplace 109
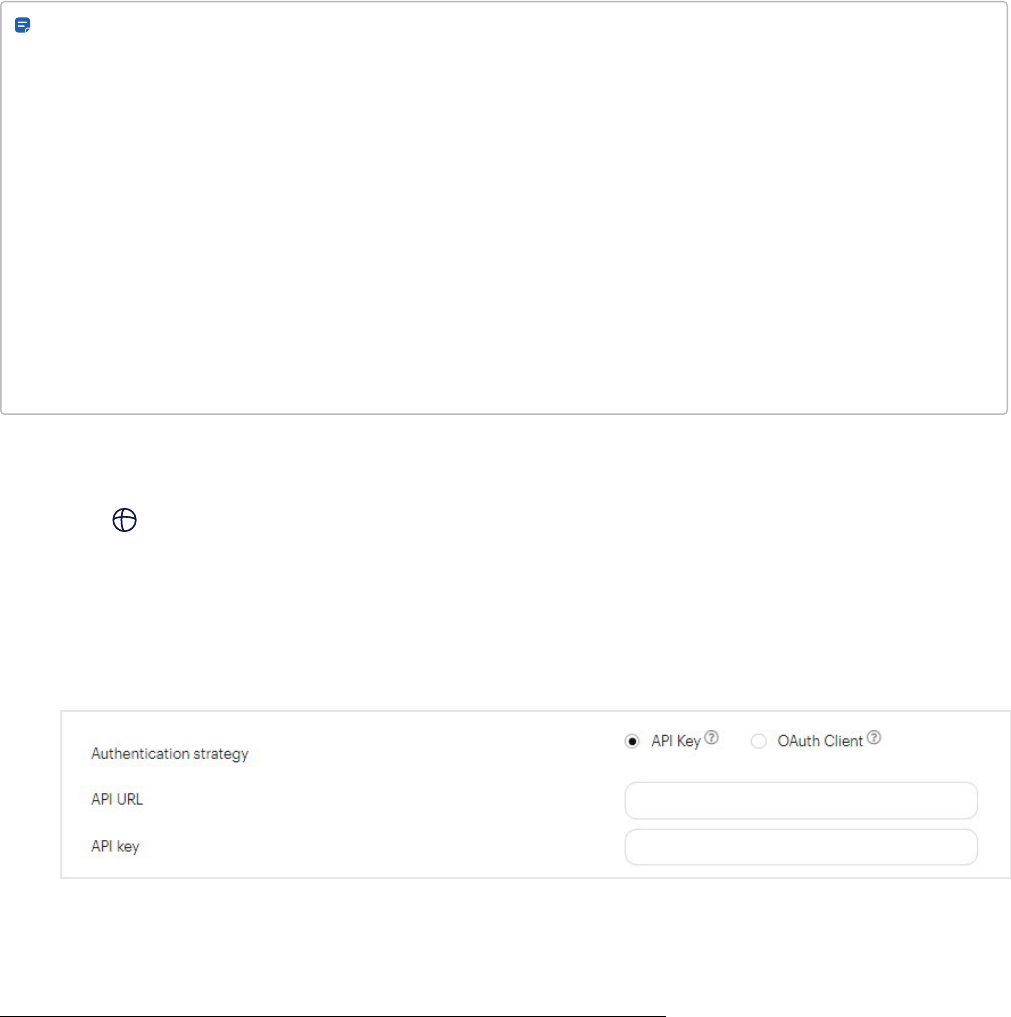
Okta
You can integrate Okta with Avigilon Alta Control Center to import and sync users and access groups in the US or EU
region. API token and OAuth 2.0 authentication methods are supported.
Note: Before you start, contact your integrator to install and configure the Okta and Avigilon Alta Control
Center SAML integration for the required region. Go to Sign on > Edit > Advanced Sign-on Settings, and enter
in Region Base URL:
l
https://api.openpath.com for US users
l
https://api.eu.openpath.com for EU users
For more information, see the Avigilon Alta article
1
about using the Okta Administrator Dashboard.
To use the API token (API Key) authentication method, you need admin privileges in your Okta account. We
recommend using a dedicated service account
2
that uses only the Okta group membership admin role to
synchronize your users and access groups. You also need to generate an Okta APIKey (token
3
) for the Okta
service account.
To use the OAuth 2.0 authentication method, you need the Okta super administrator (admin) role to add the
API Service Integration.
4
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to App marketplace > Get apps.
a. Click the Okta or Okta Advanced tile, depending on your subscription. Click the + Get app button.
b. In the window popup, select License in Item Class, your Organization, and a License Term. Click
Submit.
3. To use API key authentication, select API Key and enter the following settings:
1
For more information, see Avigilon Alta article:
https://help.openpath.com/space/EHC/2006908929/How+to+Configure+SAML+2.0+for+Okta+and+Avigilon+Alta+Security.htm
2
For more information, see Okta documentation: https://developer.okta.com/docs/guides/create-an-api-token/overview/#token-
best-practice-service-account
3
For more information, see Okta documentation:https: //developer.okta.com/docs/guides/create-an-api-token/main
4
For more information, see Okta documentation: https://help.okta.com/en-us/Content/Topics/apiservice/add-api-service-
integration.htm
App marketplace 110
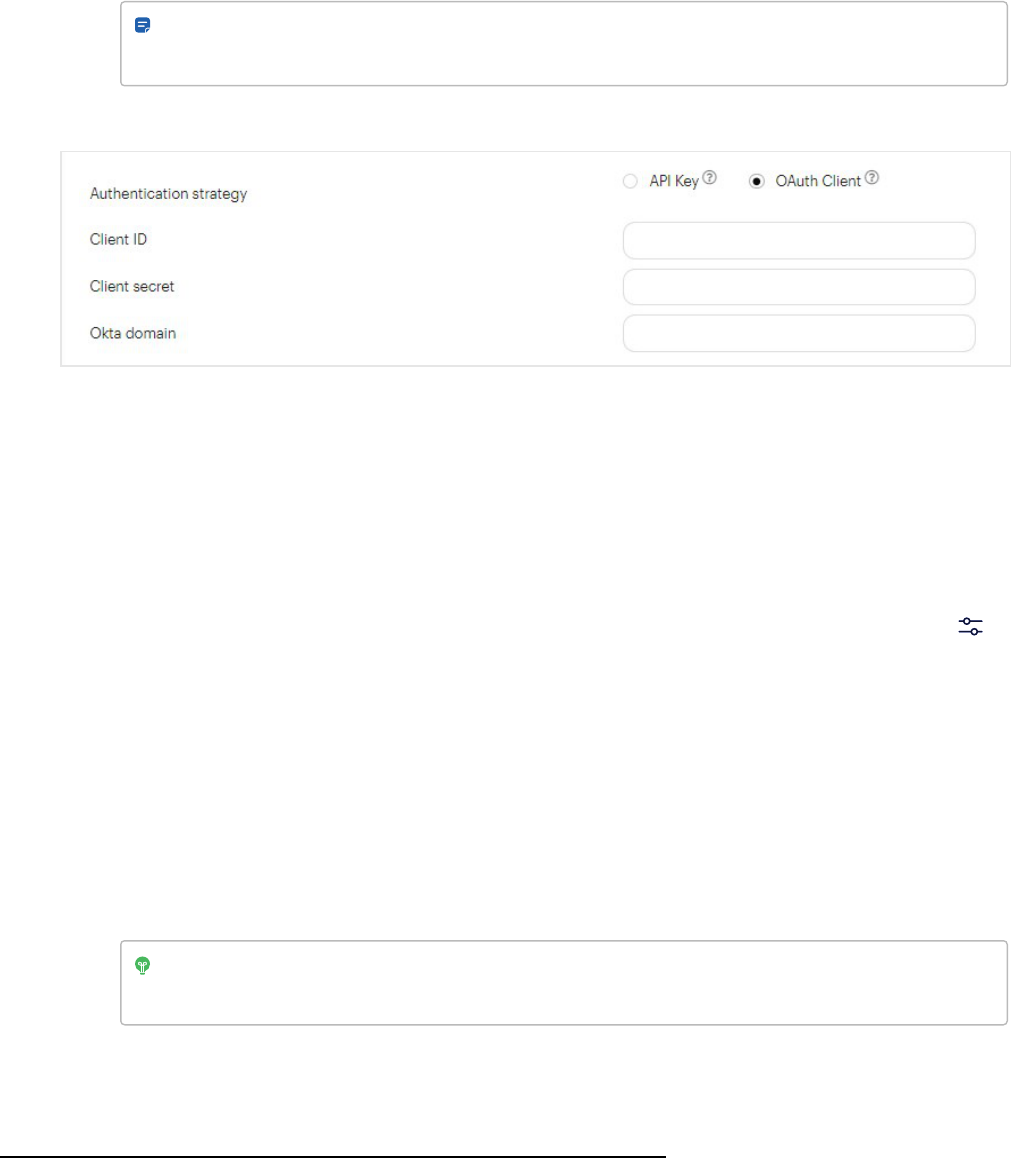
l
API URL — The Okta domain
1
for your organization (for example,
https://yourcompanyname.okta.com).
l
APIkey — The APIkey for the service account that is dedicated to the integration.
Note: After you save the API Key, Avigilon Alta does not use, or otherwise expose, the API Key
anywhere except when using it to call Okta to synchronize users and groups.
4. To use OAuth 2.0 authentication, select OAuth Client and enter the following settings:
l
Client ID — The Client ID from the API Service Integration step.
l
Client secret — The Client secret value from the API Service Integration step.
l
Okta domain — The Okta domain
2
for your organization (for example,
https://yourcompanyname.okta.com).
5. After saving one of the authentication strategies, you can enable the following settings:
l
Auto-sync every 1 houror Auto-sync every 15 minutes — Syncs Alta Control Center with the identity
provider system, once every hour or once every 15 minutes, depending on your subscription. See
Administration > Account for subscription details.
l
Auto-create mobile credential — Creates a mobile credential for every user.
l
Auto-create cloud key credential— Creates a cloud key credential for every user.
l
Sync mobile phone numbers — Syncs the mobile phone number for every user. Phone numbers must
use E.164 format with a maximum of 15 digits: +[country code][subscriber number
including area code]
l
Enable single sign-on (SSO) with portal access — Lets Okta super admin users log in to the Avigilon
Alta Control Center with their Okta credentials.
Tip: Consider using the control.openpath.com/loginSSO or control.eu.openpath.com/loginSSO
setup page to prevent users from trying a standard login.
1
For more information, see Okta documentation:https://developer.okta.com/docs/guides/find-your-domain/main
2
For more information, see Okta documentation:https://developer.okta.com/docs/guides/find-your-domain/main
App marketplace 111
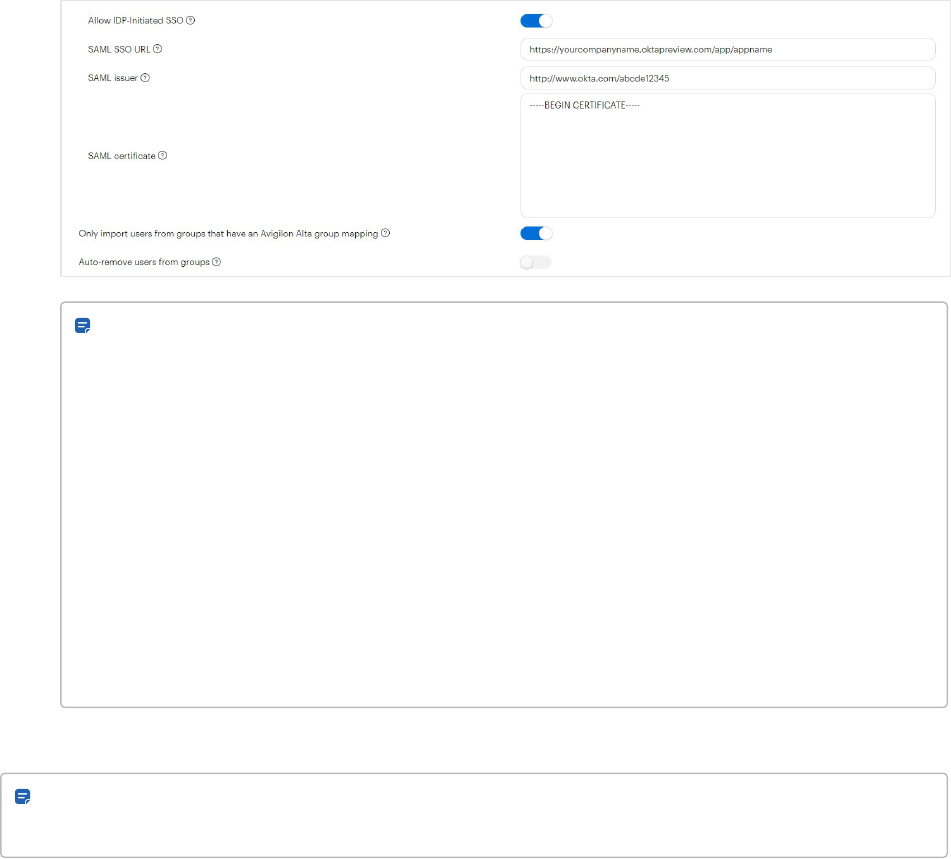
l
Only import users from groups that have an Avigilon Alta group mapping— If enabled, no users are
imported from the identity provider if they are not assigned to a group.
l
Auto-remove users from groups— Removes users from groups if they no longer exist in the identity
provider's groups.
l
Enable single sign-on (SSO) for mobile app — Lets users log in to the Openpath app using Okta
credentials.
l
Allow IDP-Initiated SSO — Lets users log in to the Avigilon Alta Control Center from the Okta portal. If
enabled, fill out the required fields: SAML SSO URL, SAML issuer, and SAML certificate.
Note: You'll find this information in the Okta portal.
a. Log in to the Okta portal and click Admin.
b. Go to Applications and click on your Avigilon Alta application.
If you haven't already added Avigilon Alta, click Add Application and then search for and
add the Avigilon Alta Security application.
c. Click Sign on.
d. In the Settings box, click View Setup Instructions.
e. Copy Sign on URL, Issuer, and Signing Certificate from the Okta portal into their
corresponding locations in the Avigilon Alta Control Center portal.
Tip: Go to Sign on > More details in the Okta portal.
7. To map a specific group or all groups from the identity provider to Alta Control Center:
Note: Complete this step if you have enabled the Only import users from groups that have an Avigilon
Alta group mapping setting.
a. Select the group from the identity provider.
b. Select the group from Avigilon Alta Control Center.
App marketplace 112
c. Click Create Access Group Mapping.
d. Repeat for all the groups that need to be mapped.
App marketplace 113
OneLogin
You can integrate the OneLogin Trusted Experience Platform™ with Avigilon Alta Control Center to import and sync
users automatically.
Note: To enable the OneLogin identity provider integration, you must have admin privileges in your OneLogin
account.
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to App marketplace > Get apps. Click the OneLogin or OneLogin Advanced tile, depending on your
subscription.
3. Enter the Subdomainfor your OneLogin account (for example, yourcompanyname.onelogin.com).
4. Click Get API credentials to go to the OneLogin page.
a. Click New Credential on the APIAccess page.
b. Enter a name for the credential, select Read Users, and click Save.
For more information, refer to OneLogin documentation.
*
5. Copy and paste the Client IDand Client secretto Alta Control Center, and click Save.
6. Enable the following settings:
l
Auto-sync every 1 houror Auto-sync every 15 minutes — Syncs Alta Control Center with the identity
provider system, once every hour or once every 15 minutes, depending on your subscription. See
Administration > Account for subscription details.
l
Auto-create mobile credential — Creates a mobile credential for every user.
l
Auto-create cloud key credential— Creates a cloud key credential for every user.
l
Sync mobile phone numbers — Syncs the mobile phone number for every user. Phone numbers must
use E.164 format with a maximum of 15 digits: +[country code][subscriber number
including area code]
Note: The default phone number (phone field) will be synced, including non-mobile phone
numbers. Users that don't have mobile numbers may not have access to some features in the
Alta Control Center.
l
Enable single sign-on (SSO) with portal access — Lets users log in to Alta Control Center with their
OneLogin credentials.
*
Refer to OneLogin documentation: https://developers.onelogin.com/api-docs/1/getting-started/working-with-api-credentials
App marketplace 114
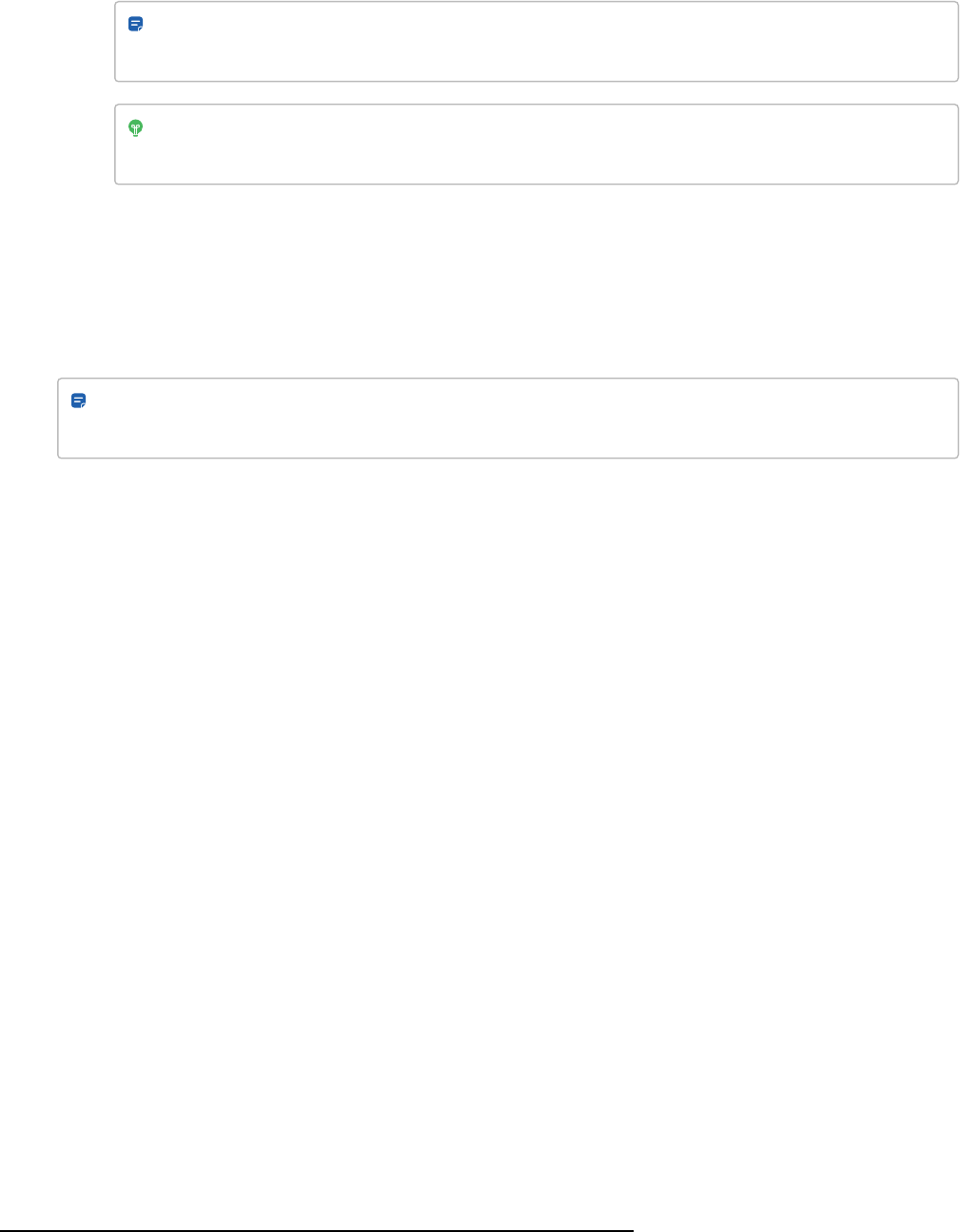
Note: Copy and paste your SSO Client ID, which you can find by connecting to an OIDC-enabled
app. For more information, see OneLogin documentation.
*
Tip: Consider using the control.openpath.com/loginSSO or control.eu.openpath.com/loginSSO
setup page to prevent users from trying a standard login.
l
Only import users from groups that have an Avigilon Alta group mapping— If enabled, no users are
imported from the identity provider if they are not assigned to a group.
l
Auto-remove users from groups— Removes users from groups if they no longer exist in the identity
provider's groups.
7. To map a specific group or all groups from the identity provider to Alta Control Center:
Note: Complete this step if you have enabled the Only import users from groups that have an Avigilon
Alta group mapping setting.
a. Select the group from the identity provider.
b. Select the group from Avigilon Alta Control Center.
c. Click Create Access Group Mapping.
d. Repeat for all the groups that need to be mapped.
*
Refer to OneLogin documentation:https://developers.onelogin.com/openid-connect/connect-to-onelogin
App marketplace 115
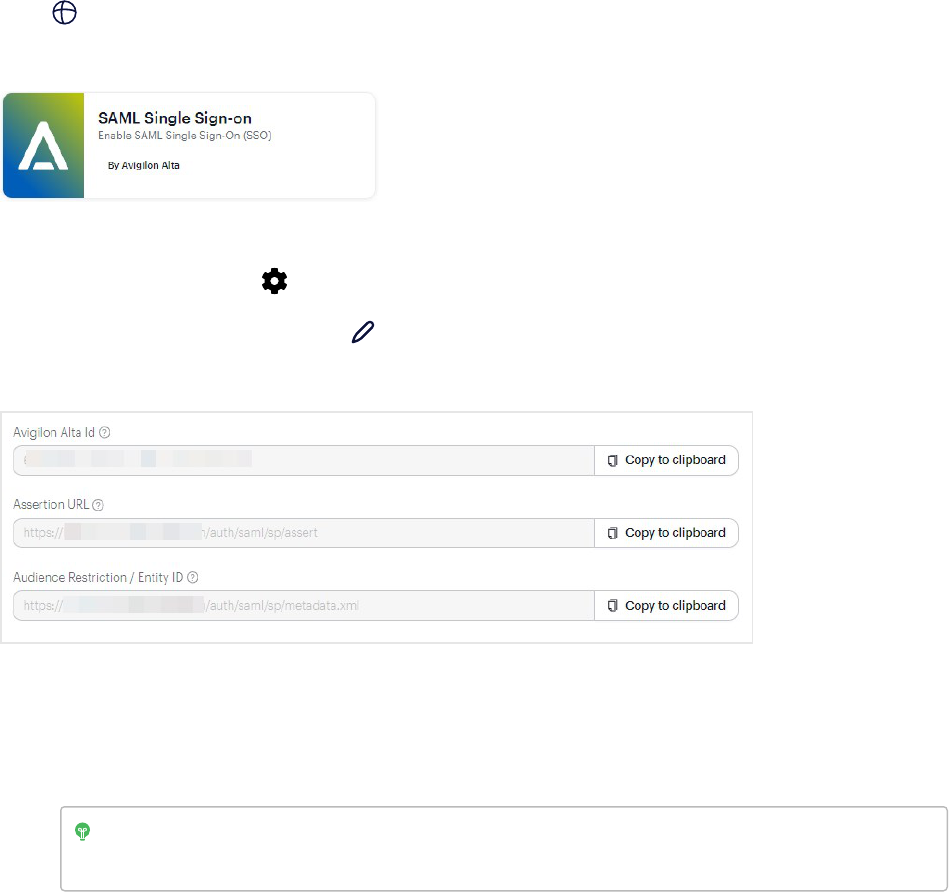
SAML Single Sign-on app
You can integrate the SAML Single Sign-on app with your SAML-enabled identity provider system to import users to
Alta Control Center. User single sign-on will occur after authentication by your identity provider.
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to App marketplace > + Get app.
3. Click the SAML Single Sign-on tile.
This app is available for Basic, Premium, and Enterprise plans.
4.
After the app is installed, click Configure.
If you are on the My apps page, click the icon.
5. Set up the app integration in your SAML-enabled identity provider system.
a. Click Copy to clipboard next to the following field in Alta Control Center, and provide the IDto new
users.
Avigilon Alta Id — The ID for initial Alta Control Center sign-in. Users will enter this ID with their email
when signing in for the first time.
Tip: Consider using the control.openpath.com/loginSSO or control.eu.openpath.com/loginSSO
setup page to prevent users from trying a standard login.
b. Click Copy to clipboard next to the following fields in Alta Control Center, and paste them in the
identity provider configuration.
App marketplace 116
Assertion URL — The SAML Assertion Consumer Service (ACS) URL where the SAML assertion is sent
in an HTTP POST.
Audience Restriction / Entity ID — The auto-generated ID for your SAML audience.
c. Create the email, firstName, lastName, and uniqueId attribute statements in the identity provider
system.
6. Enter the SAML SSO url, SAML issuer, and SAML certificate from the identity provider system in the Alta
Control Center.
7. Click Save.
App marketplace 117
Workday reports
You can integrate Workday® Human Capital Management reports with Avigilon Alta Control Center to import and
sync users and access groups, automatically.
Note: Workday Web Service API v39.1 or newer is required. In addition, you must have admin privileges in your
Workday account to configure custom reports. Custom reports must be configured before you start this
procedure. For more information, see this Avigilon Alta article
1
.
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to App marketplace > Get apps.
3. Click the Workday or Workday Advanced tile, depending on your subscription.
4. Enter the Workday account details.
l
Report URL — The URL of your Workday custom report for users.
l
Select + Get app.
l
Choose the appropriate license for your organization.
l
Click Submit.
Note: In the Workday application, go to CR - OpenPath Data Interface and click the ... Actions
menu. Select Web Service > View URLs and right-click on JSON to select Copy URL.
l
Report username — The username.
l
Report password — The password.
l
(Optional) Groups URL — The URL of your Workday custom report for access groups.
Note: In the Workday application, go to View Custom Report Openpath - Group Names and
click the ... Actions menu. Select Web Service > View URLs and right-click on JSON to select
Copy URL.
1
For more information, see: https://openpath.atlassian.net/servicedesk/customer/portal/15/article/1836056610.
App marketplace 118
5. Manually trigger the first sync.
l
Click the Synchronize button to display the active users and access groups on the Users page.
Note: With the Workday Advanced package subscription, you can enable alerts for sync failures.
For more information, see the Identity Provider toggle in Alerts by email or SMS on page129.
6. Enable the following settings, as needed.
l
Auto-sync every 1 houror Auto-sync every 15 minutes — Syncs Alta Control Center with the identity
provider system, once every hour or once every 15 minutes, depending on your subscription. See
Administration > Account for subscription details.
l
Auto-create mobile credential — Creates a mobile credential for every user.
l
Auto-create cloud key credential— Creates a cloud key credential for every user.
l
Sync mobile phone numbers — Syncs the mobile phone number for every user. Phone numbers must
use E.164 format with a maximum of 15 digits: +[country code][subscriber number
including area code]
Note: In the Workday application, the name of the report column must be defined as
mobilePhone.
l
Sync person Id — Syncs the employee ID from the identity provider system.
l
Sync department — Syncs the department from the identity provider system.
l
Sync job title — Syncs the job title from the identity provider system.
l
Only import users from groups that have an Avigilon Alta group mapping— If enabled, no users are
imported from the identity provider if they are not assigned to a group.
Tip: Consider using the control.openpath.com/loginSSO or control.eu.openpath.com/loginSSO
setup page to prevent users from trying a standard login.
l
Auto-remove users from groups— Removes users from groups if they no longer exist in the identity
provider's groups.
7. To map a specific group or all groups from the identity provider to Alta Control Center:
Note: Complete this step if you have enabled the Only import users from groups that have an Avigilon
Alta group mapping setting.
a. Select the group from the identity provider.
b. Select the group from Avigilon Alta Control Center.
App marketplace 119
c. Click Create Access Group Mapping.
d. Repeat for all the groups that need to be mapped.
App marketplace 120
Video management
Videomanagement apps let you view and play back video clips from cameras and video management systems that
are integrated with the Avigilon Alta software. Currently, Alta Control Center integrates with the following video
management systems, and more.
Alta Aware app
The Alta Aware app integration links the access control events in the Alta Control Center with video feeds from
cameras in the Alta Aware video management system.
System requirements
l
Alta Control Center event integration
o
Alta Control Center access control system added as a device in Alta Aware
For more information, see Alta Aware integration documentation.
o
Alta Control Center user account with Super Admin rights
For more information, see Alta Control Center event integration below.
l
Alta Aware camera integration
o
Alta Aware version 4.4 or newer
For more information on upgrading your Alta Aware version, see support.avasecurity.com.
o
Alta Aware app from App marketplace
For more information, see Alta Aware camera integration on the next page.
l
Normal browsing mode when navigating between systems
The button and app switcher links do not work in Chrome™ Incognito mode or private mode. For more
information, see Alta Aware, Alta DMP, and Control Center workflow on page17.
Alta Control Center event integration
To add a Super Admin user account that is used specifically for the Control Center event integration:
1.
Go to Users > Users.
2.
Click the button in the upper-right corner.
3. Enter the email and name.
4. Select the Portal access checkbox and add Super Admin.
5. Click Save.
6. Log in to Alta Aware.
App marketplace 121
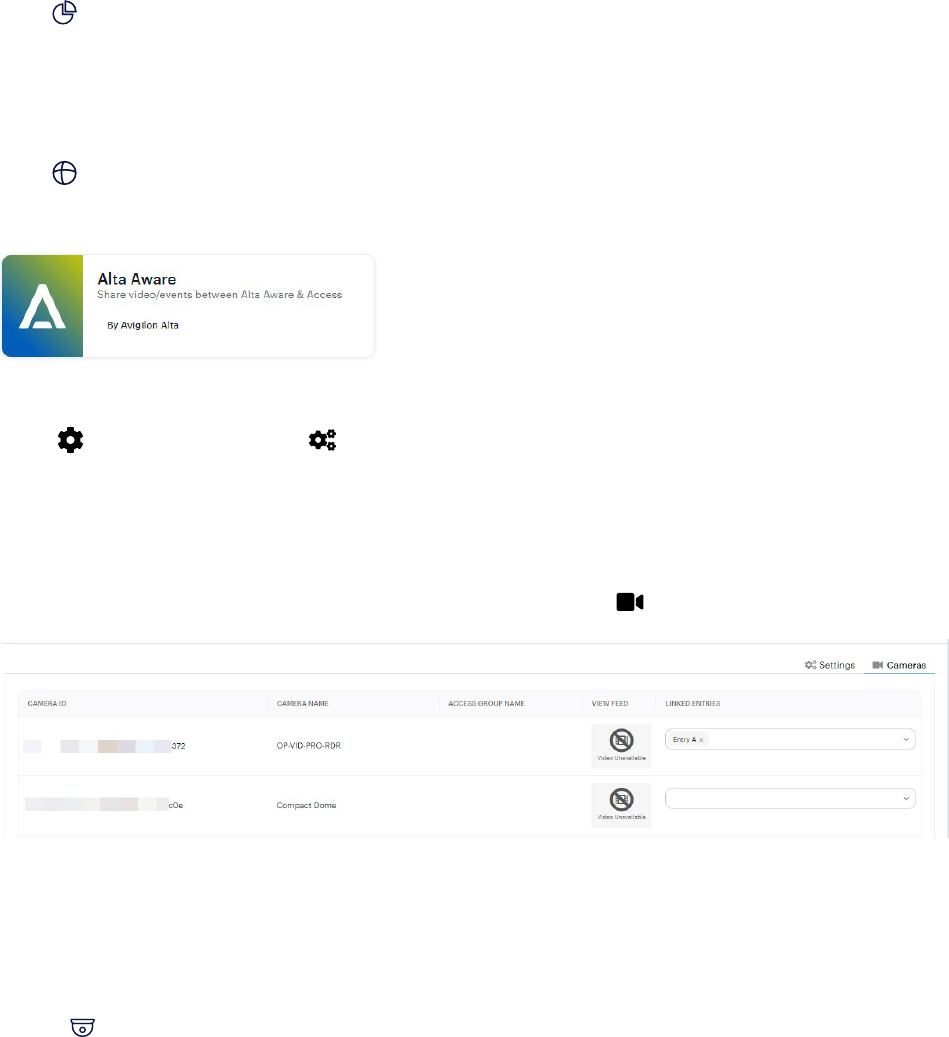
7. Enter the username and password for the 'access control point' integration. For more information, see Aware
documentation.
8.
Go to Dashboards, and add the Activity logs and Visual activity report widgets to your custom
dashboard. Or, change Activity to Activity logs or Visual activity report in the upper-right corner to view
relevant access events.
Alta Aware camera integration
1.
Go to App marketplace > Get apps.
2. Select the Alta Aware tile.
3. Select + Get app. The app is installed.
4.
Select Configure and fill out the Settings page.
Server address — The URL to access the Alta Aware VMS. For example:
https://yourcompanyname.us1.aware.ava.uk
Username and Password — The administrator's credentials which creates a user account in Alta Aware.
5.
Click Create. All cameras connected to Alta Aware are displayed on the Cameras page.
In the VIEW FEED column, you can click a video feed to access the camera in Alta Aware displayed on a new
browser tab.
In the LINKED ENTRIES lists, you can link multiple entries to a camera or multiple cameras to an entry.
6. Click Save.
Next, go to the Cameras page to view live video feeds from Alta Aware. For more information, see Cameras on
page34.
Camio
The Camio app integration links Avigilon Alta entry events and users with videos in the Camio video management
system. To set up this integration, you create outbound webhooks that send data to Camio, designate a user with
read-only portal access that translates UserIds to names, and then input Org and Entry information into the Camio
App marketplace 122
portal. For more information, see this Avigilon Alta article.
Cisco Meraki
The Cisco® Meraki® app integration lets you to view video snapshots in the Alta Control Center and events in the
Visual activity report under Reports. To set up this integration, see this Avigilon Alta article.
Milestone
The Milestone app integration links Avigilon Alta entry events and users with videos in the Milestone XProtect®
video management system. To set up this integration, see this Avigilon Alta article.
Rhombus
The Rhombus app integration links Avigilon Alta entry events and users with videos in the Rhombus video
management system. To set up this integration, designate a user with read-only portal access and use those
credentials to enable the integration in the Rhombus console. For more information, see this Avigilon Alta article.
Emergency notification and response
Rave Alert app
In Alta Control Center, you can configure a rule or alarm that sends an Alert code to the Rave Alert app to notify
employees, visitors, or students of a lockdown or emergency situation.
l
To configure your Common Alerting Protocol (CAP) listener and mass notification template, see Rave Alert
system documentation.
l
To configure rules and alarms in Control Center, see Add rules and triggers on page126 and Action triggers
and alarm notifications on page134.
Note: App installation and configuration are not applicable in the App marketplace.
App marketplace 123

Visitor management
Visitor management apps let you assign credentials to visitors in your visitor management systems and track their
entry activity in Activity logs in the Alta Control Center. Currently, Alta Control Center integrates with the following
visitor management systems, and more.
Envoy
The Envoy app integration lets you assign cloud credentials to visitors in the Envoy visitor management system. To
set up this integration, you generate guest access links for visitors in the Envoy system that can be shared by email
or SMS. For more information, see this Avigilon Alta article.
Workplace communication
Workplace communication apps let you use your business communication platform to manage access control
events through the integration with Avigilon Alta software.
Slack
The Slack
*
app integration works by defining commands that you type into Slack that will unlock individual entries.
To set up this integration, see this Avigilon Alta article.
Wireless lock integration
Schlage Wireless Locks
The Schlage wireless lock app integration connects the Allegion Schlage® NDE and LE series locks, and Control™
smart locks, in online or offline mode.
l
To set up online mode using the ENGAGE™ gateway, see this Avigilon Alta article.
l
To set up offline mode using the no-tour system integration which does not require the ENGAGE gateway, see
the Avigilon Access Control System Integration Guide for Schlage Wireless Locks No-Tour.
2
Middleware integration
Zapier
The Zapier® app integration triggers automated workflows that connect apps and services (called zaps) when new
users are created, as well as automatically generate guest access links and credentials.
To set up this integration, seethis Avigilon Alta article.
*
Slack is a trademark and service mark of Slack Technologies, Inc., registered in the U.S. and in other countries.
2
https://assets.avigilon.com/documents/avigilon-access-control-system-integration-guide-schlage-wireless-locks-notour-en.pdf
App marketplace 124
Configurations
Rules
The rules engine lets you create conditional rules that trigger actions based on access events and custom rules.
Tip: For advanced alarm management, refer to Alarms (Premium and Enterprise plans) on page131.
Add rules and triggers
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to Configurations > Rules.
3.
Click in the upper-right corner. Enter a name and description.
4. In the TRIGGER section, select the type of trigger and event.
Note: The Basic package only includes the Input trigger type, but you can still use the JSON editor to
create other rules.
Trigger type Name or related events Filter event by
CONDITIONS
Entry Entry Ajar Ended, Entry Ajar Started, Entry Forced Open,
Entry Unlock Authentication Failed, Entry Unlock
Authorization Failed
Entry filter, Site filter,
Zone filter
Entry Anti-Passback Breach, Entry Unlock Authenticated*,
Entry Unlock Authorized*, Entry Unlock Failed, Entry
Unlocked*
Entry filter, Site filter,
User filter, Zone
filter
Occupancy Limit Exceeded Within Anti-Passback Area (not applicable)
Event forwarder Includes events in this trigger list, as well as billing activity,
user creation and deletion, and identity provider sync issues.
To learn more, see this Avigilon Alta article.
Input
*
Contact Sensor End-Of-Line Supervision State Changed,
Contact Sensor State Changed, Generic Input End-Of-Line
ACU filter, ACU port
filter, State filter
*
Certain events may need a response before triggering an action (for example, failed authorization to unlock an entry). To block a
failed REX, authentication, or authorization request, select the Use blocking mode toggle.
Configurations 126

Trigger type Name or related events Filter event by
CONDITIONS
Supervision State Changed, Generic Input State Changed,
REX End-Of-Line Supervision State Changed, REX State
Changed
Tamper Detector State Changed ACU filter
Lockdown Lockdown Plan Revert Authorized*, Lockdown Plan
Reverted*, Lockdown Plan Trigger Authorized, Lockdown
Plan Triggered
For an example of a lockdown trigger, refer to this Avigilon
Alta article.
Lockdown plan
filter, User filter
Reader Reader Fault State Changed* ACU filter, ACU port
filter
Relay Relay Fault State Changed* ACU filter, ACU port
filter
Video intercom
reader
Intercom Button Pressed, Intercom Direct Connect session
requested, Intercom Front Desk Connect session requested,
Motion Detected, SIP DTMP digit heard, Sound Detected,
Tamper Detected, Video Voicemail Notification, Video
device - QR code detected
State filter, Video
intercom reader
filter, Video reader
filter
Video reader Motion Detected, Tamper Detected, Video device - QR code
detected
State filter, Video
reader filter
5. Optional. To apply a time constraint on this rule, click Add schedule and select a One-time schedule event or
Repeating schedule event. Enter date and time information.
6. In the ACTIONS section, specify what the rule will do once triggered.
Note: Only the Webhook action is applicable to the Video device - QR code detected event.
Type Related settings
CAP message Alert code — The alert code that will be sent to the mass emergency notification and
response system in Common Alerting Protocol (CAP) version 1.2 or newer.
Note: The alert code must match the alert code defined in the third-party system.
Authentication method — Choose from:
Configurations 127
Type Related settings
Note: Supported authentication methods are dependent on the emergency
notification and response system.
Basic — Enter the URL of the emergency notification and response system (example:
https://www.yourdomain.com/authentication_pathname), Username,
and Password.
Header — Enter the URL of the emergency notification and response system (see
example above), and credentials in the Authorization header value (example: Basic
ABCdef123).
URL — Embed the credentials in the URL of the emergency notification and response
system (example: https://www.yourdomain.com/authentication_
pathname?auth=BasicABCdef123).
For more examples, see this Avigilon Alta article.
Email / SMS Subject — The subject of the notification.
Body — The body of the notification.
Recipients — The phone numbers or emails.
Lockdown Lockdown plan — The lockdown plan.
Lockdown action — Trigger lockdown or Revert lockdown.
Relay ACU relay port number to trigger — The port number. The triggered relay will be on
the same ACU that the trigger event occurred on.
l
Single Door Controller: 1 or 2
l
Access Control Core: 1, 2, 3, or 4
l
Core Series expansion boards: (expansion number x 10000) + relay
port number
Example: Expansion board 2 on relay port 12 is 20012.
l
Auxiliary relays: (expansion number x 10000) + (max. port number
+ AUX number)
Example using 8-Port Board: Expansion board 3 on AUX Relay 2 is 30010.
You can also find these port IDs using the Avigilon Alta API.
State — Engage or Disengage.
Duration (seconds) — The duration in seconds.
Webhook URL — The URL for the webhook APIcall.
HTTPmethod — The GET or POST method.
For all types Select when the action is triggered by the user:
l
Delay before action (seconds) — The delay in seconds.
Configurations 128
Type Related settings
l
Block next action until finished and quit on error — The action needs a
response before triggering another action (for example, acknowledging before
clearing an alarm).
7. Click Save.
Create custom rules
1. To create custom or more complex rules, select the Use JSONeditor checkbox.
For an example of a rule created using the JSON editor, this Avigilon Alta article.
2. Click Save.
Alerts by email or SMS
Receive alerts by email or SMS to monitor your Avigilon Alta access control system.
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to Configurations > Alerts.
3. Configure alerts that generate email or SMSwarnings to US mobile numbers.
Note: The alerts depend on the locks or devices. For the alerts supported in offline locks, see the
Avigilon Access Control System Integration Guide for Schlage Wireless Locks No-Tour (link).
l
Include camera link checkbox —Includes a link to the camera in the alert that supports the option.
l
Billing —Invalid payments, expired terms, and/or your account being frozen.
l
Entry Ajar —An entry entering or leaving the ajar alarm state, such as when the contact sensor reports
the door being open longer than the set duration.
Note: To receive this alert, you must enable the Ajar feature. See Contact sensor settings on
page62.
l
Entry Authentication Failure —An entry unlock request failing due to an invalid credential being used
(e.g. a card with a number or CSN unknown to the ACU).
l
Entry Authorization Failure —An entry unlock request failing due to a user not having access to that
entry, using the wrong trigger method, or making an unlock request outside of associated schedules.
Configurations 129

l
Entry Unlock Failure —An entry unlock request failing during the physical unlock phase, either due to a
hardware issue or a failed webhook API call.
l
Entry Forced Open — An entry opening without first unlocking through the Avigilon Alta system or
triggering the REX.
Note: To receive this alert, you must also enable the Forced-Open Detection feature in Edit
entries on page61 settings on the entry.
l
Entry Anti-Passback Breach — A user attempting to re-enter a defined Anti-Passback Area without
first exiting and vice versa.
l
Other supported alerts: Lockdown Plan Triggered, Generic Input State Changed, REX State Changed,
Contact Sensor State Changed, Identity Provider, ACU Online Status Changed, Tamper Detector
State Changed, Relay Fault State Changed, Reader Fault State Changed, Input EOL State Changed,
Occupancy Management, Intercom Button Pressed, Motion Detected, Audio Detected, Video Reader
Tamper Detected, 3rd Party Device Communication Lost, 3rd Party Device Battery Low/Critical, 3rd
Party Device Error Detected, 3rd Party Device Tamper Detected, New Alarm Rate Limit Reached,
Approaching Open Alarm Limit, Open Alarm Limit Reached
4. Enter the email addresses and/or US-based phone numbers that will receive alerts.
Note: Enter phone numbers using the following format:+15556667777 (no hyphens and +1 before
the number).
Note: If the alert is enabled, but no email addresses or phone numbers are specified, the alert will be
sent to all Super Admin emails within the organization.
5. Click Save.
Configurations 130
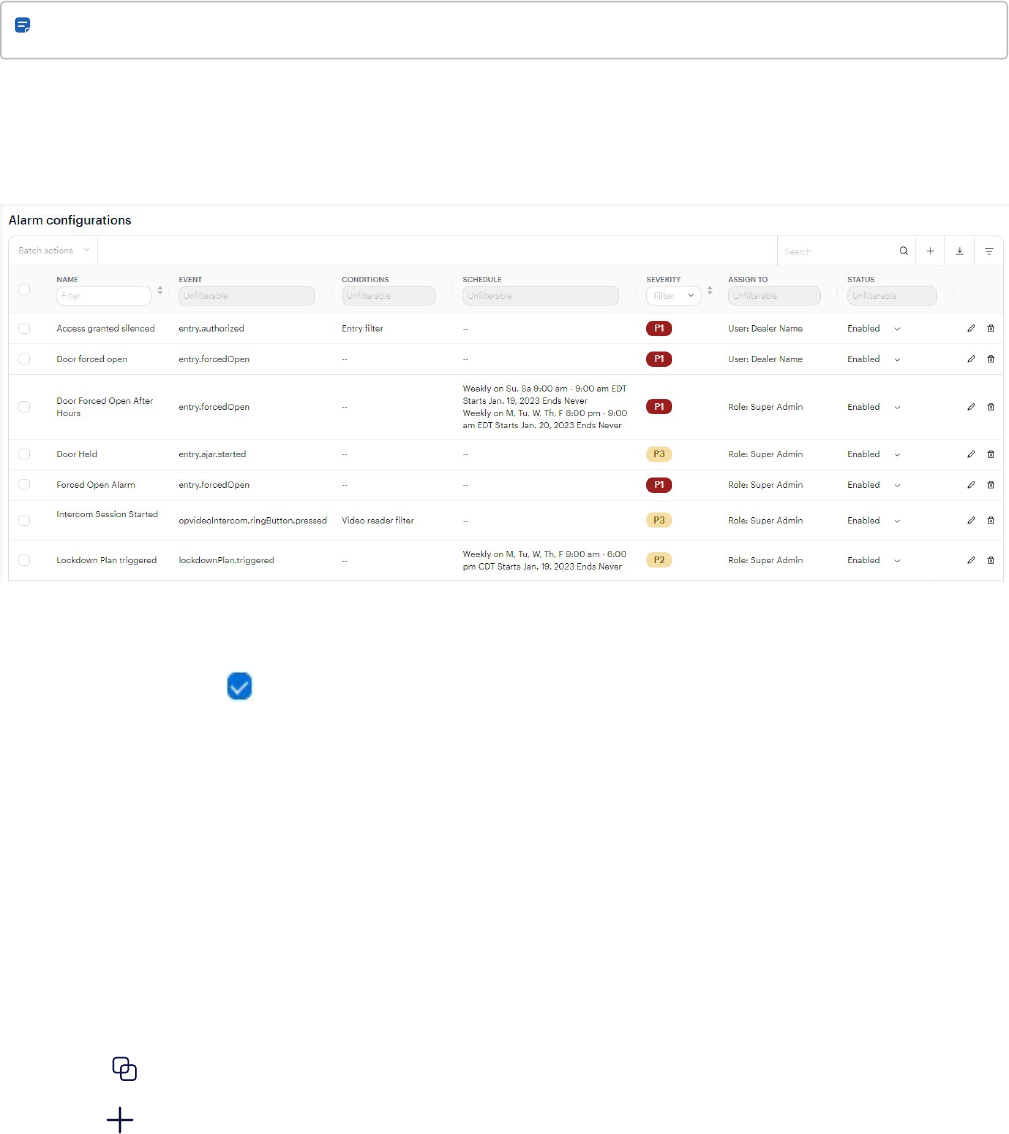
Alarms (Premium and Enterprise plans)
Note: A Premium or Enterprise plan is required.
The Alarm configurations page is used by administrators to configure alarms that notify monitoring operators about
a security situation (for example, a door forced open). After configuration is completed, monitoring operators can
receive popup notifications in the Alta Control Center, or emails and SMS notifications, and acknowledge and resolve
them.
Enable, disable, or silence alarms
1.
Enter a checkmark next to one or more alarm configurations.
2. Click Batch actions to select:
l
Enable — Shows alarms in the Alta Control Center.
l
Disable — Disables alarms and notifications. No alarms are logged in the Alta Control Center.
l
Silence — Disables alarm notifications only. Alarms are still visible in the Alarms dashboard, and report
history if enabled, in the Alta Control Center.
Configure alarms
1. Go to control.openpath.com/loginand sign in. To access the European Alta Control Center, go to
control.eu.openpath.com/login.
2.
Go to Configurations > Alarms.
3.
Click in the upper-right corner to create an alarm. Or, double-click an existing alarm to select it.
4. In the INFO section, enter a name and description for the alarm.
Configurations 131
Severity and instructions for resolution
l
In Severity, enter the priority of the alarm to be shown in the Alarms dashboard and popup notifications.
o
P1 displays as (highest priority).
o
P2 displays as .
o
P3 displays as .
o
P4 displays as .
o
P5 displays as (lowest priority).
l
In Instructions, enter the instructions for resolving the alarm. For example, you might dispatch security staff
to the physical location of the door forced open.
Alarm enabling and silencing
l
To show the alarm in the Alta Control Center, ensure the Enabled toggle is selected (default).
l
To silence popup notifications in the Alta Control Center (if configured in Profile settings) and show the alarm
in emails or SMS notifications, ensure the Silenced toggle is deselected (default).
Event triggers and advanced filtering
1. In the TRIGGER section, select the type of trigger and event, and then click Add filter.
2. If needed, enable the Use blocking mode toggle for the events marked by * in the table below.
Trigger type Name or related events Filter event by
CONDITIONS
Aware rule Event: The name of the rule defined in the Alta Aware
video management system.
Note: If your Alta Aware and Alta Control Center
systems have been unified and you have the
permissions in Alta Aware to edit rules, the Edit
rules in Aware link will be visible. Click to go
directly to the Rules list in the Alta Aware system
on a new browser tab.
(not applicable)
Configurations 132

Trigger type Name or related events Filter event by
CONDITIONS
Entry Entry Ajar Ended, Entry Ajar Started, Entry Forced
Open, Entry Unlock Authentication Failed, Entry
Unlock Authorization Failed
Entry filter, Site filter,
Zone filter
Entry Anti-Passback Breach, Entry Unlock
Authenticated*, Entry Unlock Authorized*, Entry
Unlock Failed, Entry Unlocked*
Entry filter, Site filter,
User filter, Zone filter
Occupancy Limit Exceeded Within Anti-Passback
Area
(not applicable)
Input
*
Contact Sensor End-Of-Line Supervision State
Changed, Contact Sensor State Changed, Generic
Input End-Of-Line Supervision State Changed,
Generic Input State Changed, REX End-Of-Line
Supervision State Changed, REX State Changed
ACU filter, ACU port filter,
State filter
Tamper Detector State Changed ACU filter
Lockdown Lockdown Plan Revert Authorized*, Lockdown Plan
Reverted*, Lockdown Plan Trigger Authorized,
Lockdown Plan Triggered
For an example of a lockdown trigger, refer to this
Avigilon Alta article.
Lockdown plan filter,
User filter
Reader Reader Fault State Changed* ACU filter, ACU port filter
Relay Relay Fault State Changed* ACU filter, ACU port filter
Video intercom reader Intercom Button Pressed, Intercom Direct Connect
session requested, Intercom Front Desk Connect
session requested, Motion Detected, SIP DTMP digit
heard, Sound Detected, Tamper Detected, Video
Voicemail Notification, Video device - QR code
detected
State filter, Video
intercom reader filter,
Video reader filter
Video reader Motion Detected, Tamper Detected, Video device -
QR code detected
State filter, Video reader
filter
User or role assignment
l
To assign one user, select Assign to > User and the user.
l
To assign a group of users, select Assign to > Role and the role.
*
Certain events may need a response before triggering an action (for example, failed authorization to unlock an entry). To block a
failed REX, authentication, or authorization request, select the Use blocking mode toggle.
Configurations 133
l
To require the user to acknowledge the alarm in a note in the Alta Control Center, enter a checkmark in
Require notes for acknowledgement.
Note: Only one user or one role can be assigned, however, you can enter multiple users to receive
notifications about the alarm, as described in Action triggers and alarm notifications below.
Cameras for video monitoring
In Camera(s), select any installed video intercom cameras that is relevant to the alarm.
Schedules
1. Click Add schedule to put the event triggers on a schedule.
Tip: If the event triggers need to be active at all times, do not add a schedule.
If you have configured a schedule in the Alta Aware system, you do not need to repeat the schedule in
the Control Center alarm configuration.
2. In Type, select One-time schedule event or Repeating schedule event.
3. Fill out the dates and times.
4. Click Add schedule to add another schedule.
Action triggers and alarm notifications
In the ACTIONS section, select the type of action and related settings, and click Add action.
Note: Only the Webhook action is applicable to the Video device - QR code detected event.
Type Related settings
CAP message Alert code — The alert code that will be sent to the mass emergency notification and
response system in Common Alerting Protocol (CAP) version 1.2 or newer.
Note: The alert code must match the alert code defined in the third-party system.
Authentication method — Choose from:
Note: Supported authentication methods are dependent on the emergency notification
and response system.
Basic — Enter the URL of the emergency notification and response system (example:
https://www.yourdomain.com/authentication_pathname), Username, and
Password.
Header — Enter the URL of the emergency notification and response system (see example
Configurations 134

Type Related settings
above), and credentials in the Authorization header value (example: Basic ABCdef123).
URL — Embed the credentials in the URL of the emergency notification and response
system (example: https://www.yourdomain.com/authentication_
pathname?auth=BasicABCdef123).
For more examples, see this Avigilon Alta article.
Email / SMS Subject — The subject of the notification.
Body — The body of the notification.
Recipients — The phone numbers or emails.
Lockdown Lockdown plan — The lockdown plan.
Lockdown action — Trigger lockdown or Revert lockdown.
On-screen
notification
Send to — One or more users who will receive email notifications.
Relay ACU relay port number to trigger — The port number. The triggered relay will be on the
same ACU that the trigger event occurred on.
l
Single Door Controller: 1 or 2
l
Access Control Core: 1, 2, 3, or 4
l
Core Series expansion boards: (expansion number x 10000) + relay port
number
Example: Expansion board 2 on relay port 12 is 20012.
l
Auxiliary relays: (expansion number x 10000) + (max. port number +
AUX number)
Example using 8-Port Board: Expansion board 3 on AUX Relay 2 is 30010.
You can also find these port IDs using the Avigilon Alta API.
State — Engage or Disengage.
Duration (seconds) — The duration in seconds.
Webhook URL — The URL for the webhook APIcall.
HTTPmethod — The GET or POST method.
For all types Select when the action is triggered by the user:
l
Delay before action (seconds) — The delay in seconds.
l
Block next action until finished and quit on error — The action needs a response
before triggering another action (for example, acknowledging before clearing an
alarm).
Select when one or more actions are performed by the monitoring operator:
Configurations 135

Type Related settings
l
Created — When alarm is created.
l
Acknowledged — When alarm is acknowledged.
l
Cleared — When alarm is cleared manually.
l
Auto cleared — When alarm is cleared automatically.
l
Cleared - false alarm — When a false alarm is cleared manually.
l
Reassigned — When alarm is reassigned.
Configurations 136

Mobile app
The Mobile app page is where you can enable badges on the Avigilon Alta Open app and design your organization's
badge.
Enable badge view
The Badge UI is a simplified UI for the Avigilon Alta Open app. When enabled, users will see a digital ID badge with
their name, photo, and other organizational information on their home screen of the Avigilon Alta Open app. If they
are in proximity of a reader, the entry will appear below their badge. Users can also view a list of all entries they have
access to by tapping View All.
1.
Go to Configurations > Mobile app.
2. Select the Enable badge view toggle.
Note: Users may need to update their Avigilon Alta Open app to the latest version to see the badge in their app.
Configurations 137
Customize badge design
1. Click the Badge UItab to design the digital badge.
2. On the Nametab, adjust the size, position, and text formatting.
3. On the Phototab, adjust the position of the user's photo and select a color for the photo's border.
Note: A user without a photo will instead display their initials.
4. On the Logotab:
l
Click Select Logoto upload an image in PNG, JPG, or JPEG format.
l
Click Replace Logoto replace an existing one, or remove the image to use text instead.
Note: You cannot edit the Text settings if an image is selected.
5. On the Backgroundtab:
l
Click Select Imageto use your own background image.
l
To use a solid color background instead, click the color tile in Background color to select a color
using the color picker (see example below), or drag the slider to enter your color in the HEX, RGB, or
HSB color model.
6. On the External IDtab, select the External ID toggle, and adjust the size, position, and text formatting.
7. On the Custom field 1 and Custom field 2 tabs, choose additional user information.
Note: To create a custom field, go to Users > Custom fields.
8. Click Saveto publish your changes.
Configurations 138
Tips for badge design
l
You can enable or disable any of the fields using the Enabledsliders.
l
You can customize the placement of any field by adjusting the Position settings, increasing or decreasing the
Center X (px) and Center Y (px) coordinates as desired.
o
Dimensional coordinates are based on the default badge size of 300 x 188px. If you're trying to center
a field, try inputting Center X (px): 150 and Center Y (px): 94.
l
For text fields, you can customize the font family, size, weight, line height, alignment, color, case (lower,
UPPER, or Capitalize Each Word). You can also choose whether first and last name appear on one, two, or
three lines.
l
At any point you can click Restore defaultswithin a tab to revert changes made to that particular field.
Clicking Restore defaultswill only affect the current field you are customizing.
Badge templates
The Badge templates page lets you design and format badges to print on your key cards. You can design multiple
templates, including landscape and portrait styles, or select from several default templates for contractors,
employees, and visitors.
Note: Before you start, go to the App marketplace and install the Badge Printing app.
Add badge template
1.
Go to Configurations > Badge templates.
2.
Click in the upper-right corner.
3. On the Settingstab, select a Base template (see the Preview on the right) and enter a name in Template
name.
Configurations 139
Tip: To use the default template without customizing further, click Saveand proceed to printing your
badges.
To set the template as the default for the organization, click the Org default slider.
ll
On the Nametab, adjust the size, position, and text formatting.
l
On the Phototab, adjust the position of the user's photo and select a color for the photo's border.
Note: A user without a photo will instead display their initials.
l
On the Logotab:
o
Click Select Logoto upload an image in PNG, JPG, or JPEG format.
o
Click Replace Logoto replace an existing one, or remove the image to use text instead.
Note: You cannot edit the Text settings if an image is selected.
l
On the Backgroundtab:
o
Click Select Imageto use your own background image.
o
To use a solid color background instead, click the color tile in Background color to select a
color using the color picker (see example below), or drag the slider to enter your color in the
HEX, RGB, or HSB color model.
l
On the External IDtab, select the External ID toggle, and adjust the size, position, and text formatting.
l
On the Custom field 1 and Custom field 2 tabs, choose additional user information.
Configurations 140
Note: To create a custom field, go to Users > Custom fields.
l
Click Saveto publish your changes.
Print badge
l
From Configurations > Badge templates:
1. Click the template you'd like to print.
2. In the Preview section, select the name of the user whose badge you want to print.
3. Click Print Badge.
4. Select the badge printer from the browser's print utility, or close and save the high res image to print
via a different method.
l
From Users > Users:
1. Click on the name of the user whose card credential you want to print.
2.
On the Credentials tab, click the print icon next to the card credential.
Note: If you don't see the print icon , click the Edit icon next to the card, assign a badge
template, and click Save.
3. Select the badge printer from the browser's print utility, or close and save the high-res image to print
via a different method.
Printing tips
l
Badge templates should work with any printer, but you may need to adjust print settings for your printer.
o
For the Evolis Primacy card printer, we recommend printing at 96 DPI at 100% scale.
o
If using a high definition printer, you may need to adjust the scale of the image in the printer settings.
l
Badge templates are designed for use with Avigilon key cards, which are 3.37 x 2.125 in. Printing on different
size cards may result in the image looking distorted.
l
If using the Safari application program, you may need to enable popups in order for the print utility to open.
Configurations 141

Administration
The Administration page is where you set up an account for the organization; choose a subscription plan
depending on the number of users, devices and entries in your organization; and set up billing information.
Account
Use the Account page to define organization details, set up purchasing and billing information, and review and
accept the Terms of service.
Accept terms and conditions
1.
Go to Administration > Account.
2. Review the terms and conditions and click Agree and submit.
Add help contact for mobile credential users
When a user is unable to access an entry using the Avigilon Alta Open app, an email can be sent to the site's
administrator for help.
Note: Avigilon Alta Open app version 2.10.0 or newer is required. If an email is not provided, the request will go
to Avigilon Alta Support by default.
1. In the USER HELP CONTACT section, click Change settings.
l
Enter one or more emails in Email.
The email will provide an error code with the reason and troubleshooting steps. For a list of the
possible codes, see this Avigilon Alta article.
l
Optional. Enter one or more phone numbers in Phone.
2. Click Save.
Edit organization information
1. In the INFO section, click Change settings.
l
Enter your Organization Name and Accounts payable email.
l
Set the language of the Alta Control Center emails in Organization Language.
2. Click Save.
Administration 142
Edit security settings
1. In the Security settings section, click Change settings.
l
Offline timeout setting (days):The number of days that an ACU can be offline before the token
expires. After this time, credentials will not authenticate. The maximum duration is 60 days.
l
Suspend idle users timeout setting (days):Suspends users who have not unlocked an entry within
the set duration. The minimum duration is the offline timeout duration plus 7 days. Leave the setting
blank to never suspend users.
Note: Users with portal access will never be suspended.
l
Allow your parent org to have VIEW access to this org: Enabled by default. Disable at anytime to
prevent your parent org from viewing your organization.
Note: Setting is shown only your integrator is configured as a parent org.
l
Allow Avigilon Alta Support to have VIEW access to this organization: Enabled by default. Disable at
anytime to prevent Avigilon Alta Support from viewing your organization.
l
Allow Avigilon Alta Support to have EDIT access to this organization and Allow Avigilon Alta
Support to have UNLOCK access to this organization: These settings cannot be enabled; you must
escalate changes to Avigilon Alta Support or Engineering.
l
Enable remote unlock by default for new users
Note: Existing users are not impacted by changes to this setting.
2. Click Save.
Quick start for sites, ACUs, and readers
Use the Quick start page to set up a site with ACUs and readers all on one page. This is useful if you're already
familiar with setting up sites and hardware.
Licenses
To upgrade a Basic package to Premium or Enterprise:
1.
Go to Administration > Licenses.
2. View the licensed-based features that can be purchased and details, including SKUs and quantities.
For example, the Basic: Entries license provides 2 entries and the Enterprise: Entries license provides 1000
entries.
3. Click Request package and then Yes.
Administration 143
To view the requested licenses, select the Request history tab.
Administration 144

Glossary
C
CAP
Common Alerting Protocol. An open, industry-standard message format for exchanging
all types of emergency notifications and alerts over a network. Alta Control Center sup-
ports the transmission of alert codes to external systems if actions are triggered in rule or
alarm configuration.
Glossary 145
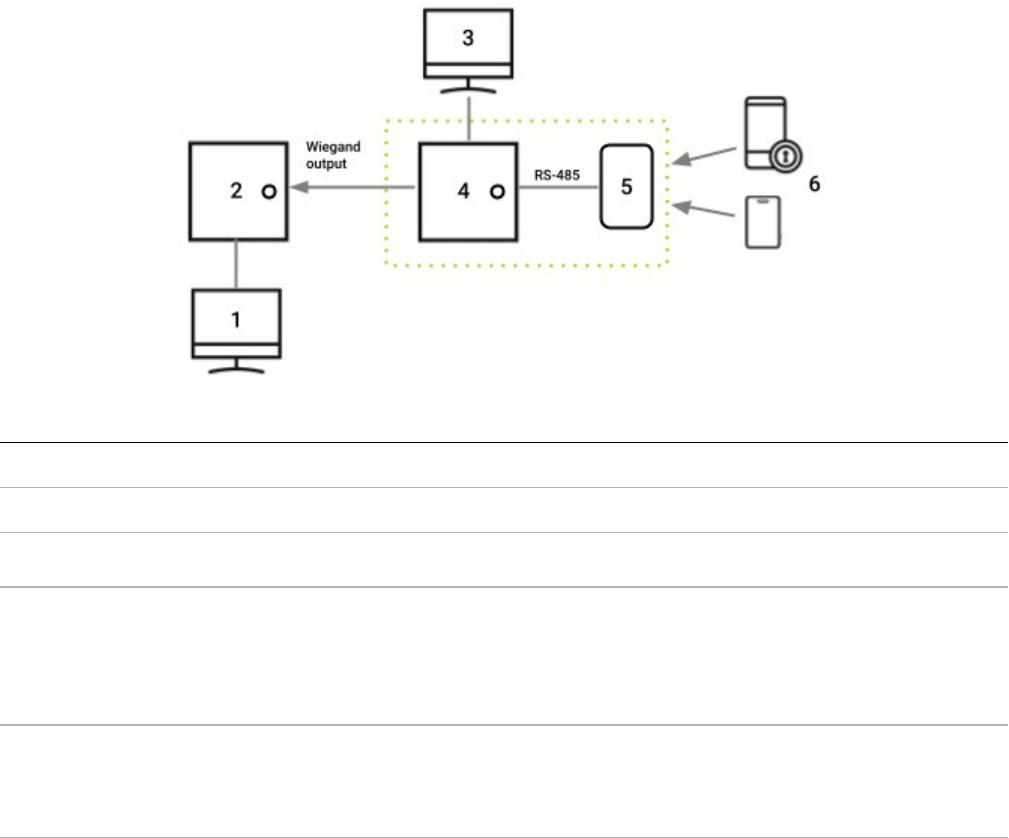
Appendix A: Configure mobile gateway with
legacy access control systems
You can configure Avigilon Alta Control Center to support legacy access control systems. In this configuration, the
legacy panel controls all locking hardware and entry mechanisms while the Avigilon system lets you use the Avigilon
Alta Open app, Smart Reader, and Wave to Unlock functionality.
System overview
Figure 1 Mobile Gateway diagram
1 Legacy access control system software
2 Legacy access control system panel
3 Avigilon Alta Control Center
4a Avigilon Smart Hub ACU installed between the Smart Reader and the legacy panel
The Avigilon Pro series readers (Video Reader Pro and Video Intercom Reader Pro) do not require the
Avigilon Access Control Unit (ACU).
4b Wiegand port configured as output to the legacy panel
For more information, see advanced wiring in the Avigilon Alta Access Control System Installation Guide
(link).
5 Avigilon Smart Readers
If existing Wiegand readers use a proprietary card format, they can be wired to new Avigilon Smart
Readers. Otherwise, replace existing readers with Avigilon Smart Readers.
Appendix A: Configure mobile gateway with legacy access control systems 146
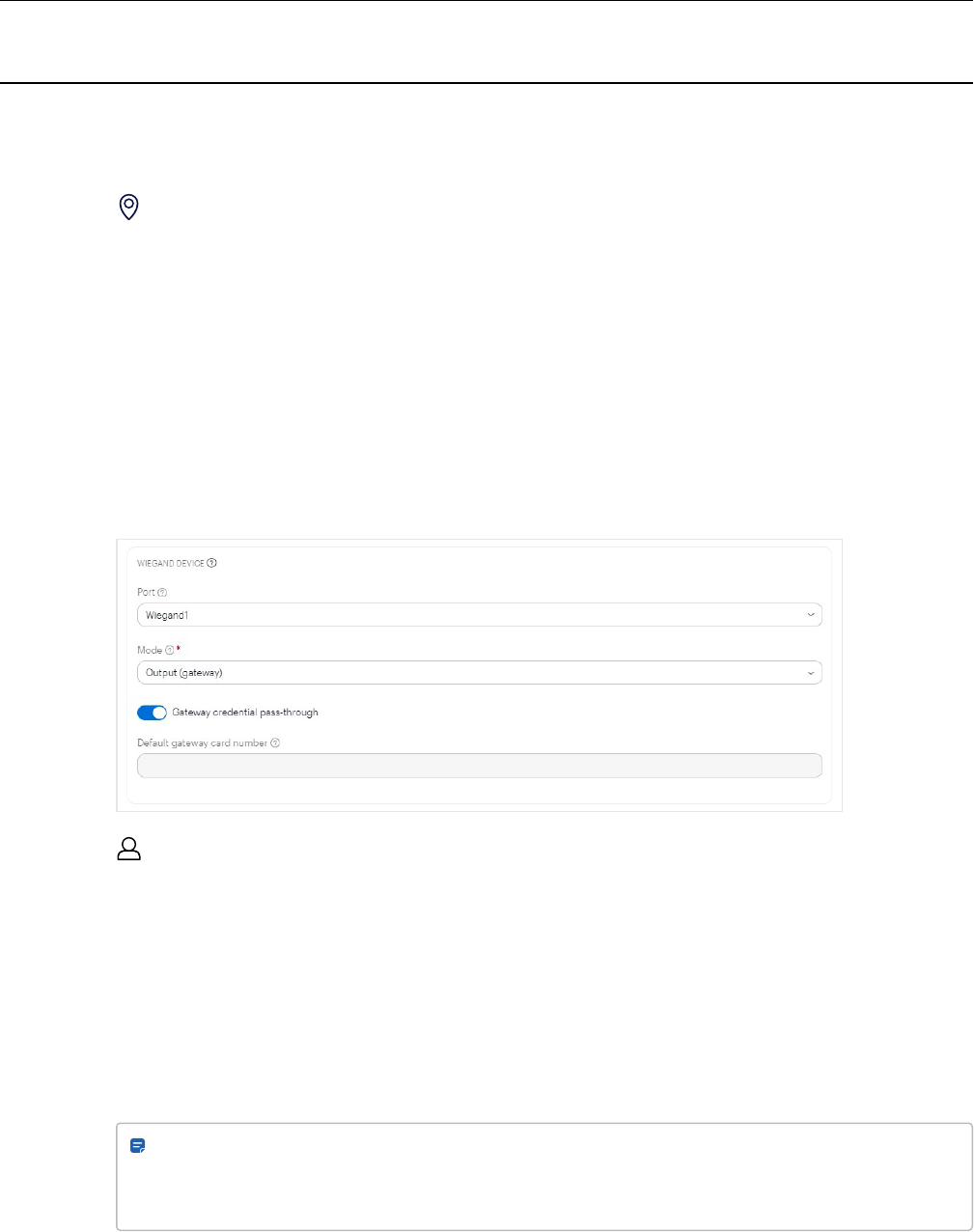
6 Avigilon Alta Open app, Cloud Key credentials and Wave to unlock functionality
Avigilon credential with default gateway number or Wiegand ID
Configure Wiegand device settings
l
On the Sites > Entries page, configure the Wiegand port for Output (gateway) mode.
o
Port— The port for the Wiegand device to which this entry is wired.
o
Mode— The direction the card credential data is sent.
n
Input— Receives data from the Wiegand reader.
n
Output (gateway) — Sends credential data to a third-party control panel.
Enable Gateway credential pass-through if you do not want the Avigilon Alta system to
authenticate credentials, but rather send all data to the legacy panel for authentication.
Enter a Default gateway card number so that all credentials (including mobile credentials) are
sent to the legacy panel as a Wiegand ID.
l
On the Users page, configure the credential.
o
For users who initiate authenticated unlock requests with a valid Avigilon credential but do not have a
dedicated Card: Wiegand ID credential set to Use for Gateway to be sent to the legacy panel, define a
Default gateway card number on the Entries page that will be sent instead.
o
Instead of setting up a Default gateway card number for the entry, you can send individual user
credentials to the legacy panel. Create a Card: Wiegand ID credential (physical card not required) for
the user and enable Use for Gateway. This way, that card number will be sent to the legacy panel
whenever the user makes an authorized unlock request using any of the user's valid Avigilon
credentials.
Note: This configuration supports one-to-one credential mapping for accurate user-level
reporting within the legacy system. See Issue keycard, fob, mobile, PIN, wiegand, or cloud-based
credentials on page39.
Appendix A: Configure mobile gateway with legacy access control systems 147
